netlab launch 1.3 launched assist for VXLAN transport with static ingress replication and EVPN management aircraft. Final week we changed a VLAN trunk with VXLAN transport, now we’ll exchange static ingress replication with EVPN management aircraft.
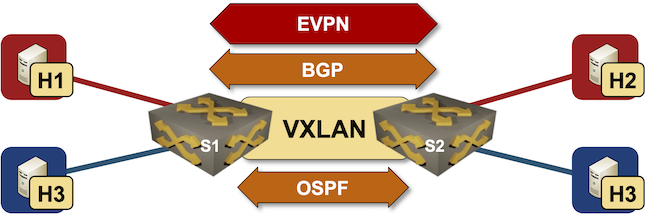
Lab topology
We’ll begin with the VXLAN bridging topology and add EVPN configuration module to the switches. We’ll even have so as to add BGP configuration module (EVPN wants BGP) and outline BGP AS with bgp.as international parameter… and that’s it – now we now have a working EVPN/VXLAN lab.
Including EVPN and BGP configuration modules
teams:
switches:
members: [ s1,s2 ]
module: [ vlan,vxlan,ospf,bgp,evpn ]
bgp.as: 65000
Behind the scenes netlab:
- As within the earlier instance, configures OSPF and VXLAN. VXLAN VNIs not use the ingress replication lists.
- Begins BGP course of on S1 and S2, and builds an IBGP session between the loopback interfaces.
- Assigns EVPN RT/RD to each VLAN with a VXLAN VNI.
- Prompts EVPN tackle household on the IBGP session between S1 and S2.
Now for an attention-grabbing plot twist. All the pieces netlab does works on a number of community working programs. All you need to do to construct a multi-vendor lab utilizing Arista EOS and Cumulus Linux is so as to add machine sorts to the switches.
Constructing a multi-vendor EVPN/VXLAN lab
nodes:
s1:
machine: eos
s2:
machine: cumulus
Begin the lab with netlab up and all of it works. Right here’s the BGP desk as noticed on S1 (Arista EOS):
EVPN BGP desk on Arista EOS
s1#sh bgp evpn
BGP routing desk info for VRF default
Router identifier 10.0.0.5, native AS quantity 65000
Route standing codes: s - suppressed, * - legitimate, > - lively, E - ECMP head, e - ECMP
S - Stale, c - Contributing to ECMP, b - backup
% - Pending BGP convergence
Origin codes: i - IGP, e - EGP, ? - incomplete
AS Path Attributes: Or-ID - Originator ID, C-LST - Cluster Checklist, LL Nexthop - Hyperlink Native Nexthop
Community Subsequent Hop Metric LocPref Weight Path
* > RD: 10.0.0.6:1000 mac-ip aac1.ab17.1b03 fe80::a8c1:abff:fe17:1b03
10.0.0.6 - 100 0 i
* > RD: 10.0.0.6:1001 mac-ip aac1.ab17.1b03 fe80::a8c1:abff:fe17:1b03
10.0.0.6 - 100 0 i
* > RD: 10.0.0.6:1000 mac-ip aac1.abcf.8cf5
10.0.0.6 - 100 0 i
* > RD: 10.0.0.6:1000 mac-ip aac1.abcf.8cf5 172.16.0.2
10.0.0.6 - 100 0 i
* > RD: 10.0.0.6:1000 imet 10.0.0.6
10.0.0.6 - 100 0 i
* > RD: 10.0.0.6:1001 imet 10.0.0.6
10.0.0.6 - 100 0 i
* > RD: 10.0.0.5:1000 imet 10.0.0.5
- - - 0 i
* > RD: 10.0.0.5:1001 imet 10.0.0.5
- - - 0 i
You too can use netlab to discover ways to configure netlab-supported options on platforms you’re not conversant in. Listed here are the related snippets of Arista EOS configuration generated in the course of the netlab preliminary course of:
Arista cEOS EVPN/VXLAN bridging configuration
hostname s1
!
spanning-tree mode mstp
!
vlan 1000
identify crimson
!
vlan 1001
identify blue
!
interface Ethernet1
switchport entry vlan 1000
!
interface Ethernet2
switchport entry vlan 1001
!
interface Ethernet3
description s1 -> s2
no switchport
ip tackle 10.1.0.1/30
ip ospf community point-to-point
ip ospf space 0.0.0.0
!
interface Loopback0
ip tackle 10.0.0.5/32
ip ospf space 0.0.0.0
!
interface Vlan1000
description VLAN crimson (1000) -> [h1,h2,s2]
!
interface Vlan1001
description VLAN blue (1001) -> [h3,h4,s2]
!
interface Vxlan1
vxlan source-interface Loopback0
vxlan udp-port 4789
vxlan vlan 1000 vni 101000
vxlan vlan 1001 vni 101001
!
router bgp 65000
router-id 10.0.0.5
no bgp default ipv4-unicast
bgp advertise-inactive
neighbor 10.0.0.6 remote-as 65000
neighbor 10.0.0.6 next-hop-self
neighbor 10.0.0.6 update-source Loopback0
neighbor 10.0.0.6 description s2
neighbor 10.0.0.6 send-community customary prolonged
!
vlan 1000
rd 10.0.0.5:1000
route-target import 65000:1000
route-target export 65000:1000
redistribute realized
!
vlan 1001
rd 10.0.0.5:1001
route-target import 65000:1001
route-target export 65000:1001
redistribute realized
!
address-family evpn
neighbor 10.0.0.6 activate
!
address-family ipv4
neighbor 10.0.0.6 activate
community 10.0.0.5/32
!
router ospf 1
router-id 10.0.0.5
max-lsa 12000
!
finish
Gathering Cumulus Linux configuration is a little more of an effort. Right here’s a abstract of how the bridging interfaces are configured (collected from a wide range of /and so forth/community/interfaces.d recordsdata):
Cumulus Linux interface configuration
iface bridge
bridge-vlan-aware sure
bridge-vids 1001
bridge-vids 1000
bridge-ports swp1
bridge-ports swp2
bridge-ports vni-101000
bridge-ports vni-101001
iface swp1
bridge-access 1000
iface swp2
bridge-access 1001
iface vni-101000
bridge-access 1000
vxlan-id 101000
vxlan-learning no
iface vni-101001
bridge-access 1001
vxlan-id 101001
vxlan-learning no
… and right here is the FRR management aircraft configuration:
Cumulus Linux FRR configuration
router bgp 65000
bgp router-id 10.0.0.6
no bgp default ipv4-unicast
neighbor 10.0.0.5 remote-as 65000
neighbor 10.0.0.5 description s1
neighbor 10.0.0.5 update-source lo
!
address-family ipv4 unicast
community 10.0.0.6/32
neighbor 10.0.0.5 activate
neighbor 10.0.0.5 next-hop-self
exit-address-family
!
address-family l2vpn evpn
neighbor 10.0.0.5 activate
advertise-all-vni
vni 101001
rd 10.0.0.6:1001
route-target import 65000:1001
route-target export 65000:1001
exit-vni
vni 101000
rd 10.0.0.6:1000
route-target import 65000:1000
route-target export 65000:1000
exit-vni
advertise-svi-ip
promote ipv4 unicast
exit-address-family
!
router ospf
ospf router-id 10.0.0.6
Need to run this lab by yourself, or strive it out with completely different gadgets? No downside:

