Microsoft’s Azure AD Kerberos service, a cloud-based id and entry administration (IAM) service based mostly on Kerberos authentication, may be attacked utilizing strategies just like these utilized by attackers towards on-premises Kerberos servers.
Kerberos is a broadly used protocol used to authenticate customers and gadgets through symmetric key cryptography and a key distribution middle; it permits fashionable authentication mechanisms reminiscent of single sign-on (SSO). As a result of Kerberos authentication is a regular safety measure for a lot of enterprises, attackers have incessantly tried to compromise or bypass the authentication servers utilizing id assaults that spoof reputable customers.
Within the on-premises world, a pair of frequent id assaults are the Move the Ticket and Silver Ticket approaches, which permit an attacker to make use of stolen credentials or mint their very own credentials, respectively, and authenticate with enterprise companies. Each strategies proceed to work to a point towards the cloud variations of Kerberos authentication servers, in accordance with cybersecurity companies agency Silverfort, which dubbed the cloud-based iterations of the assaults the Bounce the Ticket and Silver Iodide threats.
“Identification assaults which have existed for a while are nonetheless a danger as organizations transfer into the cloud,” says Dor Segal, senior safety researcher on the agency. “Azure AD Kerberos is a brand new implementation however not a brand new protocol. Safety groups want to concentrate on this reality and put applicable mitigations in place.”
The truth that variants of the 2 assaults nonetheless work within the cloud present that transferring safety infrastructure to the cloud has little impression on the risk, Segal says.
“The problems outlined may impression anybody utilizing the brand new Azure AD Kerberos protocol,” he says. “Whereas Azure AD Kerberos continues to be in preliminary phases of adoption, as with something launched by Microsoft, the dimensions of utilization will improve. Prior to now, this kind of lateral motion was a problem affecting the on-premises enterprise community. These [new] assaults break this perimeter.”
Microsoft added Kerberos performance to its Azure Energetic Listing service final August, and attackers are positive to comply with, Silverfort argued in a analysis report issued Jan. 25. In any case, IAM methods have change into linchpins for a lot of firms’ zero-trust safety efforts, with Microsoft Energetic Listing, for instance, a goal of assaults in 9 out of 10 incidents. As well as, Kerberos is a frequent goal of attackers, who typically go after “tickets” — i.e., encrypted authentication credentials or tokens, utilized by the Kerberos protocol as proof {that a} consumer or machine has authenticated to the server.
A profitable try and duplicate a ticket positive factors attackers entry to protected assets for a restricted time, typically on the order of hours, permitting them to maneuver round a company community or use SSO companies like electronic mail that could be protected by the Kerberos credential.
Bouncing & Silver Tickets
Within the first assault, dubbed a Bounce the Ticket assault, an attacker who has compromised one consumer’s system and who steals a Kerberos ticket from the machine’s reminiscence can then then use the key key to realize entry to cloud workloads. This assault bears similarities to the on-premises Move the Ticket assault on Kerberos authentication companies and provides the assault the flexibility to “entry cloud-based assets that depend on Azure AD Kerberos,” in accordance with Silverfort’s analysis.
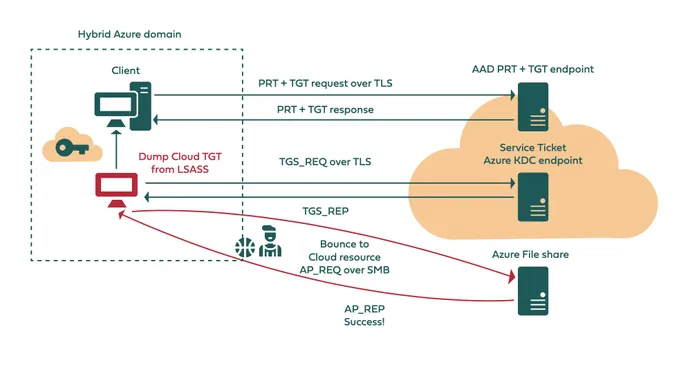
Within the second assault, dubbed a Silver Iodide assault, an attacker who positive factors entry to 1 consumer’s Azure AD account can connect with a selected service — within the instance given by Silverfort, the Azure Recordsdata cloud sharing service — after discovering a “safety hole” within the service. The safety weak spot, which Silverfort didn’t describe, can be utilized to create a brand new server ticket to entry or manipulate info. The method, which resembles the Silver Ticket assault towards on-premises Kerberos servers, may very well be used towards different cloud companies as effectively, so long as attackers can discover methods round particular controls, Silverfort acknowledged.
No Repair Forward
Total, the 2 points signify methods an attacker — who has compromised both a system on the community or an Azure AD account — may get better Kerberos tickets and reuse these secrets and techniques to increase entry to different infrastructure.
Silverfort disclosed the problems to Microsoft, and whereas the corporate is conscious of the weaknesses, it doesn’t plan to repair them, as a result of they aren’t “conventional” vulnerabilities, Segal says. Microsoft additionally confirmed that the corporate doesn’t think about them vulnerabilities.
“This system just isn’t a vulnerability, and for use efficiently a possible attacker would wish elevated or administrative rights that grant entry to the storage account information,” a Microsoft spokesperson tells Darkish Studying. “We advocate clients repeatedly evaluate their function definitions that embody ‘listkeys’ permissions, and allow software program that stops attackers from stealing credentials, reminiscent of Credential Guard.”
Silverfort’s Segal acknowledges that to repair the problems, the Kerberos protocol must be redesigned, and that’s unlikely.
“Fixing a weak spot in any implementation of Kerberos just isn’t as easy as patching a conventional software program vulnerability as a result of it will require re-engineering your complete protocol,” he says. “This could be a major enterprise which might take a considerable amount of useful resource and impression the compatibility of legacy functions utilizing Kerberos.”
Corporations could make it tougher to use any safety weak spot of their cloud-based Kerberos infrastructure, nevertheless. Organizations ought to evaluate any modifications to the Azure Entry Management service and monitor updates to the permissions. Decreasing the variety of methods approved to carry among the extra important cloud-based credentials — such because the Ticket-Granting Ticket (TGT) — will harden an enterprise’s infrastructure to Bounce the Ticket assaults, Silverfort acknowledged in its report.


