An lively malware marketing campaign is focusing on the Python Bundle Index (PyPI) and npm repositories for Python and JavaScript with typosquatted and faux modules that deploy a ransomware pressure, marking the newest safety subject to have an effect on software program provide chains.
The typosquatted Python packages all impersonate the favored requests library: dequests, fequests, gequests, rdquests, reauests, reduests, reeuests, reqhests, reqkests, requesfs, requesta, requeste, requestw, requfsts, resuests, rewuests, rfquests, rrquests, rwquests, telnservrr, and tequests.
Based on Phylum, the rogue packages embed supply code that retrieves Golang-based ransomware binary from a distant server relying on the sufferer’s working system and microarchitecture.
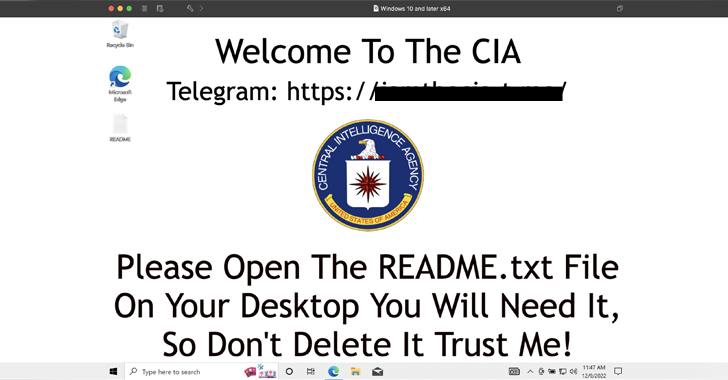
Profitable execution causes the sufferer’s desktop background to be modified to an actor-controlled picture that claims to the U.S. Central Intelligence Company (CIA). It is also designed to encrypt recordsdata and demand a $100 ransom in cryptocurrency.
In an indication that the assault is just not restricted to PyPI, the adversary has been noticed publishing 5 completely different modules in npm: discordallintsbot, discordselfbot16, discord-all-intents-bot, discors.jd, and telnservrr.
“The attacker has additionally printed a number of npm packages that behave in the same method,” Phylum CTO Louis Lang mentioned, including every of the libraries comprise the JavaScript equal of the identical code to deploy the ransomware.
The findings come as ReversingLabs uncovered a tranche of 10 extra PyPI packages pushing modified variations of the W4SP Stealer malware as a part of an ongoing provide chain assault geared toward software program builders that is believed to have began round September 25, 2022.
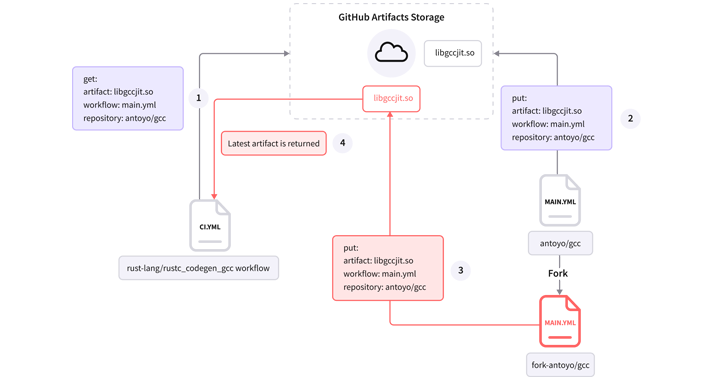
That is not all. Earlier this month, Israel-based software program provide chain safety agency Legit Safety demonstrated a brand new assault approach towards a Rust repository (“rust-lang”) that abuses GitHub Actions to poison authentic artifacts.
Construct artifacts are the recordsdata created by the construct course of, corresponding to distribution packages, WAR recordsdata, logs, and stories. By changing the precise modules with trojanized variations, an actor may steal delicate data or ship extra payloads to all its downstream customers.
“The vulnerability was present in a workflow known as ‘ci.yml’ which is chargeable for constructing and testing the repository’s code,” Legit Safety researcher Noam Dotan mentioned in a technical write-up.
By exploiting this weak point, an attacker may trick the GitHub workflow into executing a malware-laced artifact, successfully making it attainable to tamper with repository branches, pull requests, points, and releases.
The maintainers of the Rust programming language addressed the problem on September 26, 2022, following accountable disclosure on September 15, 2022.