A brand new backdoor related to a malware downloader named Wslink has been found, with the instrument doubtless utilized by the infamous North Korea-aligned Lazarus Group, new findings reveal.
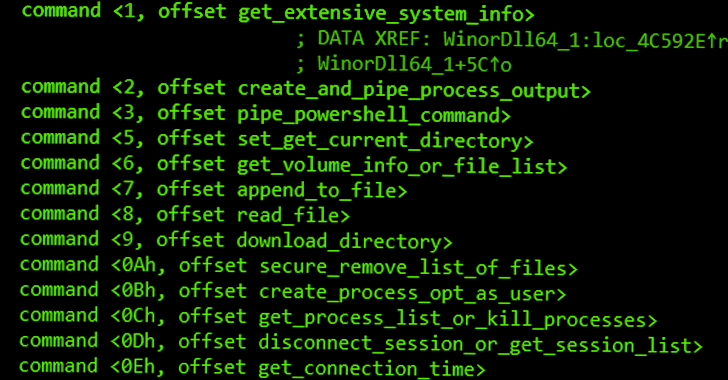
The payload, dubbed WinorDLL64 by ESET, is a fully-featured implant that may exfiltrate, overwrite, and delete recordsdata; execute PowerShell instructions; and acquire complete details about the underlying machine.
Its different options comprise itemizing lively classes, creating and terminating processes, enumerating drives, and compressing directories.
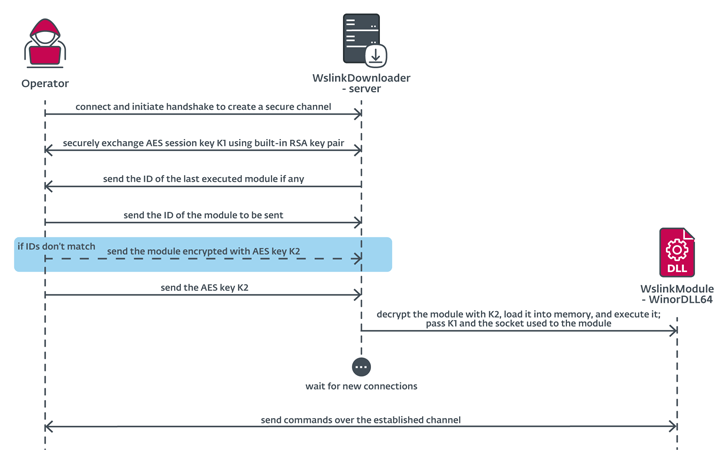
Wslink was first documented by the Slovak cybersecurity agency in October 2021, describing it as a “easy but exceptional” malware loader that is able to executing acquired modules in reminiscence.
“The Wslink payload may be leveraged later for lateral motion, as a result of its particular curiosity in community classes,” ESET researcher Vladislav Hrčka stated. “The Wslink loader listens on a port specified within the configuration and might serve further connecting purchasers, and even load numerous payloads.”
Intrusions leveraging the malware are stated to be extremely focused owing to the truth that solely a handful of detections have been noticed so far in Central Europe, North America, and the Center East.
In March 2022, ESET elaborated on the malware’s use of an “superior multi-layered digital machine” obfuscator to evade detection and resist reverse engineering.
The hyperlinks to Lazarus Group stem from overlaps in habits and code to that of earlier campaigns – Operation GhostSecret and Bankshot – which have been attributed to the superior persistent menace.
This consists of similarities with the GhostSecret samples detailed by McAfee in 2018, which include a “data-gathering and implant-installation element” that runs as a service, mirroring the identical habits of Wslink.
ESET stated the payload was uploaded to the VirusTotal malware database from South Korea, the place a number of the victims are positioned, including credence to the Lazarus involvement.
The findings are as soon as once more demonstrative of the huge arsenal of hacking instruments employed by the Lazarus Group to infiltrate its targets.
“Wslink’s payload is devoted to offering means for file manipulation, execution of additional code, and acquiring intensive details about the underlying system that probably may be leveraged later for lateral motion,” ESET stated.