Pervasive encryption that protects information not simply in transit and at relaxation, however in use — thus releasing firms of the worry of information breaches — has lengthy been a dream of enterprise executives, IT groups, and compliance professionals.
In 2023, these goals could grow to be a sensible actuality, with a lot of database and data-security companies releasing software program to permit firms to maintain information encrypted whereas nonetheless permitting frequent operations, akin to looking. Final 12 months, for instance, database-technology supplier MongoDB launched a preview of its Queryable Encryption functionality, which permits firms to seek for information information in “expressive” methods while not having to decrypt the info. And, this week, information safety agency Vaultree launched a software program growth package to permit software makers to strive its Knowledge-in-Use Encryption characteristic, which — the corporate claims — permits extra in depth operations on encrypted information.
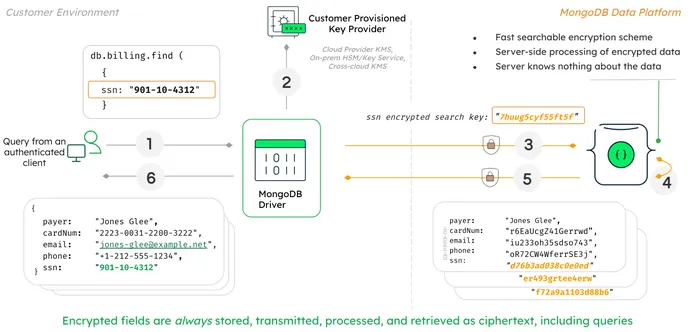
The purpose is to permit firms and their functions the power to entry and search databases effectively, whereas stopping unauthorized customers from ever decrypting delicate info, says Kenn White, safety principal at MongoDB.
“What we hear loads from clients is issues round leaks, breaches, and assaults on public cloud infrastructure, together with privileged customers, and so we’re targeted on areas the place we will add further safety controls and technical measures to restrict who can see delicate information in actual time,” he says. “[W]e imagine [encryption-in-use] will proceed to be an space with plenty of potential for innovation, significantly for operational workloads.”
The applied sciences promise to assist organizations reduce the so-called “blast radius” when a community or system is compromised. Sometimes, companies struggling a breach face a cascade of forensic investigations, regulatory filings and fines, and the potential publicity of delicate information and mental property. Encrypted information permits firms to sidestep lots of the devastating impacts of a breach, however has sometimes required advanced information structure designs to ensure plaintext info just isn’t inadvertently left insecure.
Many expertise firms have tried to unravel the issue and permit the safe use of information by functions by extending using encryption. Within the 2010s, for instance, Ionic Safety aimed to encrypt all information on the fly and solely permit its use by approved customers with particular privileges. Twilio purchased the corporate in 2021.
If the present crop of applied sciences succeed the place others have failed, firms might see considerably much less threat within the occasion of a breach, says Ryan Lasmaili, CEO at Vaultree.
“We all know if there is a leak, and the info is totally encrypted, it reduces the corporate’s threat instantly to regulatory compliance,” he says. “However GDPR proper now, for instance, doesn’t cowl data-in-use encryption, as a result of to this point, it has been seen as not being there but.”
Avoiding Llamas within the Indy 500
MongoDB’s Queryable Encryption encrypts database fields, which means that the data is cryptographically safe always, but can nonetheless be used for looking. The keys for decrypting the data are saved with every shopper, giving solely particular folks and units the power to decrypt delicate fields. Even a database administrator can’t decrypt each area except they’ve the correct keys.
Making the applied sciences a actuality relied on analysis by small teams of educational cryptographers. Queryable Encryption, for instance, got here from the work of Seny Kamara and Tarik Moataz, each of Brown College, who went on to create a startup, Aroki Software program, which was bought by MongoDB in 2021.
The purpose of Queryable Encryption is to ship expertise immediately that may deal with queries which can be really helpful and make the aptitude straightforward for builders, MongoDB’s White mentioned throughout a presentation on the USENIX ENIGMA Convention in January. Key to all that’s that efficiency mustn’t get in the best way, he mentioned.
“It needs to be sub-linear — the distinction between 1,000 paperwork, one million, 5 million, and 100 million paperwork, it must be sub-linear,” he mentioned. “Plenty of the educational work had been executed in a means that was super-linear, so works nice on 10 information, or 100, 1,000, 5,000 — past that, it is painful. And you may throw extra CPUs at it, however you already know, it is form of like racing the Indy 500 with llamas — there’s solely a lot you are able to do.”
Different applied sciences, like totally homomorphic encryption (FHE), promise to permit a extra in depth vary of operations on encrypted information and have been extensively funded by the US Division of Protection. A group from Intel and Microsoft signed a multiyear analysis grant with the DoD in 2021 underneath the DARPA Knowledge Safety in Digital Environments (DPRIVE) program to create a {hardware} accelerator to hurry up the infamous processing-intensive FHE approaches. In January, Duality Applied sciences, one other DPRIVE grant recipient, introduced it was named to Part 2 of that program to speed up machine-learning processing on encrypted information.
“Structured encryption, like most encryption schemes, protects information confidentiality — which means that information is protected in a means the place solely folks permitted to obtain the info even have entry to this information,” says Kurt Rohloff, chief expertise officer at Duality Applied sciences. “FHE additionally gives information confidentiality, however permits extra processing on the info with out requiring decryption.”
Extra Testing Wanted
New encryption fashions and applied sciences sometimes require a marathon of testing and analysis. MongoDB’s Queryable Encryption stemmed from tutorial analysis on structured encryption, with a number of papers describing the method. FHE has had a long time of analysis and open growth. Vaultree’s Knowledge-in-Use Encryption stays, to a big diploma, a black field, though CEO Lasmaili pledges that scientific papers might be forthcoming.
In a weblog on the probabilities of pervasive encryption, cybersecurity agency Kaspersky warned that such applied sciences require quite a lot of oversight, as a result of even small missteps can undermine the safety of the methods.
“This occurs to be a standard downside of sensible cryptography — when the builders of an info system really feel compelled to craft one thing in-house that meets their explicit information encryption necessities,” the corporate said. “This ‘one thing’ then typically seems to be susceptible as a result of the event course of did not take into consideration the newest scientific analysis.”
Whereas encryption-in-use could declare an early lead as a result of it’s usable in its present state, breakthroughs in FHE could win in the long term, particularly as quantum computing could find yourself being a differentiator. FHE continues to have purposeful and safety advantages, particularly in a post-quantum encryption world, says Duality Applied sciences’ Rohloff.
“Absolutely homomorphic encryption does permit many safer operations on it as in comparison with common structured encryption,” he says. “Not all variations of structured encryption [are] protected towards quantum computing assaults, however all used totally homomorphic encryption schemes are believed to be protected towards quantum computing assaults.”


