The Darkish Pink superior persistent risk (APT) actor has been linked to a recent set of assaults concentrating on authorities and navy entities in Southeast Asian international locations with a malware known as KamiKakaBot.
Darkish Pink, additionally known as Saaiwc, was first profiled by Group-IB earlier this 12 months, describing its use of customized instruments akin to TelePowerBot and KamiKakaBot to run arbitrary instructions and exfiltrate delicate info.
The risk actor is suspected to be of Asia-Pacific origin and has been energetic since at the very least mid-2021, with an elevated tempo noticed in 2022.
“The most recent assaults, which occurred in February 2023, have been nearly equivalent to earlier assaults,” Dutch cybersecurity firm EclecticIQ disclosed in a brand new report revealed final week.
“The principle distinction within the February marketing campaign is that the malware’s obfuscation routine has improved to higher evade anti-malware measures.”
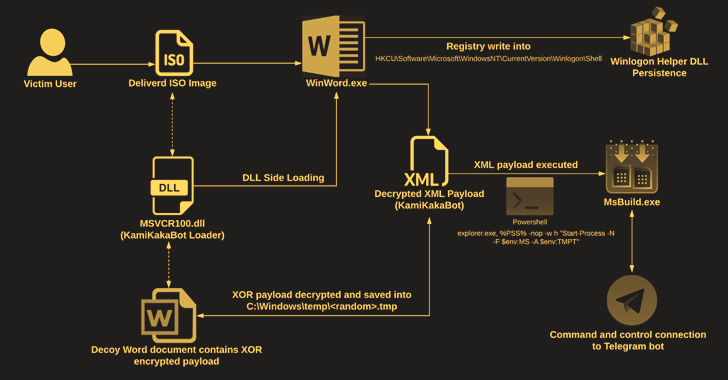
The assaults play out within the type of social engineering lures that comprise ISO picture file attachments in e mail messages to ship the malware.
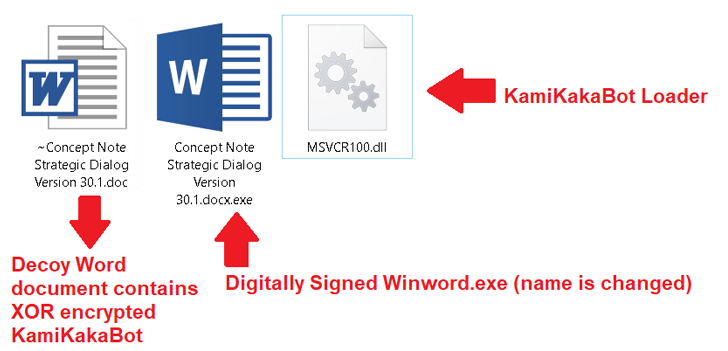
The ISO picture consists of an executable (Winword.exe), a loader (MSVCR100.dll), and a decoy Microsoft Phrase doc, the latter of which comes embedded with the KamiKakaBot payload.
The loader, for its half, is designed to load the KamiKakaBot malware by leveraging the DLL side-loading technique to evade safety protections and cargo it into the reminiscence of the Winword.exe binary.
KamiKakaBot is primarily engineered to steal information saved in internet browsers and execute distant code utilizing Command Immediate (cmd.exe), whereas additionally embracing evasion methods to mix in with sufferer environments and hinder detection.
Uncover the Hidden Risks of Third-Occasion SaaS Apps
Are you conscious of the dangers related to third-party app entry to your organization’s SaaS apps? Be part of our webinar to be taught in regards to the sorts of permissions being granted and the best way to reduce threat.
Persistence on the compromised host is achieved by abusing the Winlogon Helper library to make malicious Home windows Registry key modifications. The gathered information is subsequently exfiltrated to a Telegram bot as a ZIP archive.
“The usage of respectable internet providers as a command-and-control (C2) server, akin to Telegram, stays the primary alternative for various risk actors, starting from common cyber criminals to superior persistent risk actors,” the Amsterdam-based firm mentioned.
“The Darkish Pink APT group may be very possible a cyber espionage-motivated risk actor that particularly exploits relations between ASEAN and European nations to create phishing lures through the February 2023 marketing campaign.”