Two new safety weaknesses found in a number of electrical automobile (EV) charging techniques could possibly be exploited to remotely shut down charging stations and even expose them to information and vitality theft.
The findings, which come from Israel-based SaiFlow, as soon as once more display the potential dangers dealing with the EV charging infrastructure.
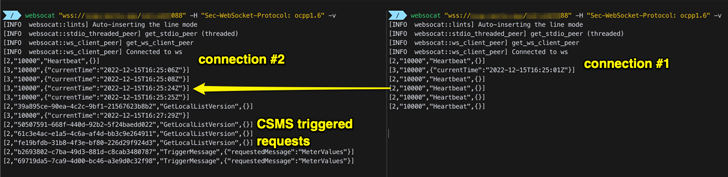
The problems have been recognized in model 1.6J of the Open Cost Level Protocol (OCPP) normal that makes use of WebSockets for communication between EV charging stations and the Charging Station Administration System (CSMS) suppliers. The present model of OCPP is 2.0.1.
“The OCPP normal does not outline how a CSMS ought to settle for new connections from a cost level when there’s already an lively connection,” SaiFlow researchers Lionel Richard Saposnik and Doron Porat stated.
“The shortage of a transparent guideline for a number of lively connections may be exploited by attackers to disrupt and hijack the connection between the cost level and the CSMS.”
This additionally implies that a cyber attacker may spoof a connection from a legitimate charger to its CSMS supplier when it is already related, successfully resulting in both of the 2 eventualities:
- A denial-of-service (DoS) situation that arises when the CSMS supplier closes the unique the WebSocket connection when a brand new connection is established
- Info theft that stems from protecting the 2 connections alive however returning responses to the “new” rogue connection, allowing the adversary to entry the driving force’s private information, bank card particulars, and CSMS credentials.
The forging is made potential owing to the truth that CSMS suppliers are configured to solely depend on the charging level id for authentication.
“Combining the mishandling of recent connections with the weak OCPP authentication and chargers identities coverage may result in an enormous Distributed DoS (DDoS) assault on the [Electric Vehicle Supply Equipment] community,” the researchers stated.
OCPP 2.0.1 remediates the weak authentication coverage by requiring charging level credentials, thereby closing out the loophole. That stated, mitigations for when there are a couple of connection from a single charging level ought to necessitate validating the connections by sending a ping or a heartbeat request, SaiFlow famous.
“If one of many connections just isn’t responsive, the CSMS ought to eradicate it,” the researchers defined. “If each connections are responsive, the operator ought to be capable to eradicate the malicious connection straight or through a CSMS-integrated cybersecurity module.”