It is no secret that third occasion apps can enhance productiveness, allow distant and hybrid work and are total, important in constructing and scaling an organization’s work processes.
An innocuous course of very like clicking on an attachment was within the earlier days of e-mail, folks do not suppose twice when connecting an app they want with their Google workspace or M365 atmosphere, and so on. Easy actions that customers take, from creating an e-mail to updating a contact within the CRM, may end up in a number of different automated actions and notifications within the related platforms.
As seen within the picture beneath, the OAuth mechanism makes it extremely simple to interconnect apps and many do not take into account what the potential ramifications might be. When these apps and different add-ons for SaaS platforms ask for permissions’ entry, they’re normally granted with no second thought, presenting extra alternatives for dangerous actors to achieve entry to an organization’s knowledge. This places firms in danger for provide chain entry assaults, API takeovers and malicious third occasion apps.
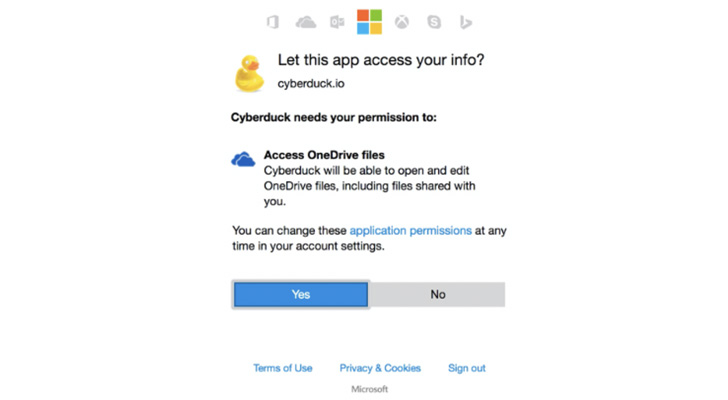 |
| Oauth mechanism permission request |
In terms of native machines and executable information, organizations have already got management in-built that allows safety groups to dam problematic applications and information. It must be the identical relating to SaaS apps.
Discover ways to achieve visibility into your SaaS stack
How Do third Occasion Apps Acquire Entry?
OAuth 2.0 has tremendously simplified authentication and authorization, and gives a fine-grained delegation of entry rights. Represented within the type of scopes, an software asks for the person’s authorization for particular permissions. An app can request a number of scopes. Via approval of the scopes, the person grants these apps permissions to execute code to carry out logic behind the scenes inside their atmosphere. These apps may be innocent or as threatening as an executable file.
Finest Practices to Mitigate Third Occasion App Entry Danger
To safe an organization’s SaaS stack, the safety staff wants to have the ability to determine and monitor all that occurs inside their SaaS ecosystem. Here is what a safety staff can share with workers and deal with themselves to mitigate third occasion app entry threat.
1 — Educate the staff within the group
Step one in cybersecurity all the time comes again to elevating consciousness. As soon as the staff turn out to be extra conscious of the dangers and risks that these OAuth mechanisms current, they are going to be extra hesitant to make use of them. Organizations also needs to create a coverage that enforces workers to submit requests for third occasion apps.
2 — Acquire visibility into the third occasion entry for all business-critical apps
Safety groups ought to achieve visibility into each enterprise vital app and overview all of the completely different third occasion apps which have been built-in with their business-critical SaaS apps – throughout all tenets. One of many first steps when shrinking the risk floor is gaining an understanding of the total atmosphere.
3 — Map the permissions and entry ranges requested by the related third occasion apps
As soon as the safety staff is aware of which third occasion apps are related, they need to map the permissions and the kind of entry that every third occasion app has been given. From there they are going to have the ability to see which third occasion app presents the next threat, based mostly on the upper stage of scope. With the ability to differentiate between an app that may learn versus an app that may write will assist the safety staff prioritize which must be dealt with first.
As well as, the safety staff ought to map which customers granted these permissions. For instance, a high-privileged person, somebody who has delicate paperwork of their workspace, who grants entry to a 3rd occasion app can current a excessive threat to the corporate and must be remediated instantly.
4 — Get the automated strategy to deal with third occasion app entry
SaaS Safety Posture Administration options can automate the invention of third occasion apps. The suitable SSPM resolution, like Adaptive Protect, has built-in logic that maps out all of the 3rds occasion apps with entry to the group’s SSPM built-in apps. This visibility and oversight empowers safety groups so whether or not an organization has a 100 or 600 apps, they’ll simply keep in management, monitor and safe their firm’s SaaS stack.
The Larger SaaS Safety Image
To safe an organization’s SaaS stack, the safety staff wants to have the ability to determine and monitor all that occurs inside their SaaS ecosystem. third occasion app entry is only one part of the SaaS Safety Posture Administration image.
Most present cybersecurity options nonetheless don’t supply sufficient safety or a handy solution to monitor an organization’s SaaS stack, not to mention the communications between their identified apps and platforms, leaving firms susceptible and unable to successfully know or management which events have entry to delicate company or private knowledge.
Organizations want to have the ability to see all of the configurations and person permissions of every app, together with all of the third occasion apps which have been granted entry by customers. This manner safety groups can retain management of the SaaS stack, remediate any points, block any apps utilizing too many privileges and mitigate their threat.


