Hackers with ties to the Iranian authorities have been linked to an ongoing social engineering and credential phishing marketing campaign directed towards human rights activists, journalists, researchers, teachers, diplomats, and politicians working within the Center East.
No less than 20 people are believed to have been focused, Human Rights Watch (HRW) mentioned in a report printed Monday, attributing the malicious exercise to an adversarial collective tracked as APT42, which is understood to share overlaps with Charming Kitten (aka APT35 or Phosphorus).
The marketing campaign resulted within the compromise of electronic mail and different delicate information belonging to a few of the targets. This included a correspondent for a significant U.S. newspaper, a ladies’s rights defender based mostly within the Gulf area, and Nicholas Noe, a Lebanon-based advocacy advisor for Refugees Worldwide.
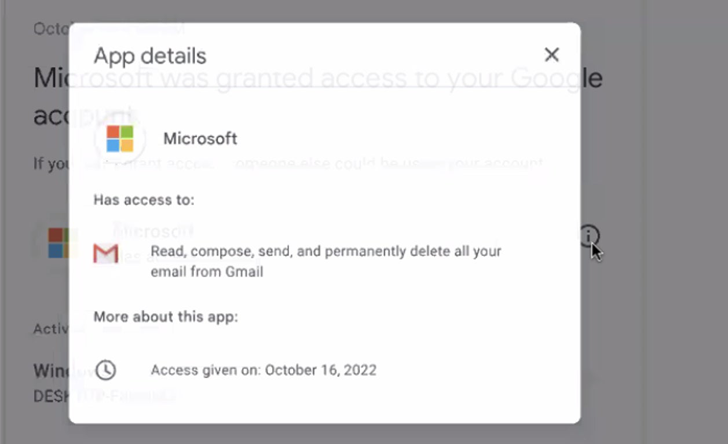
The digital break-in entailed having access to their emails, cloud storage, calendars, and contacts, in addition to exfiltrating your entire information related to their Google accounts within the type of archive information via Google Takeout.
“Iran’s state-backed hackers are aggressively utilizing refined social engineering and credential harvesting ways to entry delicate info and contacts held by Center East-focused researchers and civil society teams,” Abir Ghattas, info safety director at Human Rights Watch, mentioned.
The an infection chain commences with the targets receiving suspicious messages on WhatsApp below the pretext of inviting them to a convention and luring the victims into clicking a rogue URL that captured their Microsoft, Google, and Yahoo! login credentials.
These phishing pages are additionally able to orchestrating adversary-in-the-middle (AiTM) assaults, thereby making it potential to breach accounts which are secured by two-factor authentication (2FA) aside from a {hardware} safety key.
15 of the focused high-profile people are confirmed to have acquired the identical WhatsApp messages between September 15 and November 25, 2022, the worldwide non-governmental group mentioned.
HRW additional identified inadequacies in Google’s safety protections, because the victims of the phishing assault “didn’t notice their Gmail accounts had been compromised or a Google Takeout had been initiated, partly as a result of the safety warnings below Google’s account exercise don’t push or show any everlasting notification in a consumer’s inbox or ship a push message to the Gmail app on their telephone.”
The choice to request information from Google Takeout traces up with a .NET-based program known as HYPERSCRAPE that was first documented by Google’s Menace Evaluation Group (TAG) earlier this August, though HRW mentioned it couldn’t verify if the instrument was certainly employed on this particular incident.
The attribution to APT42 is predicated on overlaps within the supply code of the phishing web page with that of one other spoofed registration web page that, in flip, was related to a credential theft assault mounted by an Iran-nexus actor (aka TAG-56) towards an unnamed U.S. suppose tank.
“The risk exercise is extremely seemingly indicative of a broader marketing campaign that makes use of URL shorteners to direct victims to malicious pages the place credentials are stolen,” Recorded Future disclosed late final month. “This tradecraft is frequent amongst Iran-nexus superior persistent risk (APT) teams like APT42 and Phosphorus.”
What’s extra, the identical code has been linked to a different area utilized as a part of a social engineering assault attributed to the Charming Kitten group and disrupted by Google TAG in October 2021.
It is value mentioning that regardless of APT35 and APT42’s hyperlinks to Iran’s Islamic Revolutionary Guard Corps (IRGC), the latter is geared extra in the direction of people and entities for “home politics, international coverage, and regime stability functions,” per Mandiant.
“In a Center East area rife with surveillance threats for activists, it is important for digital safety researchers to not solely publish and promote findings, but additionally prioritize the safety of the area’s embattled activists, journalists, and civil society leaders,” Ghattas mentioned.