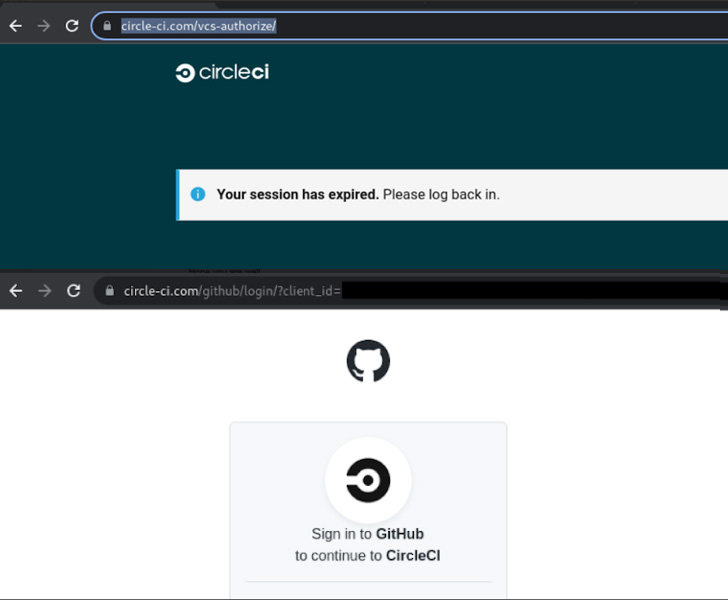
GitHub has put out an advisory detailing what could also be an ongoing phishing marketing campaign focusing on its customers to steal credentials and two-factor authentication (2FA) codes by impersonating the CircleCI DevOps platform.
The Microsoft-owned code internet hosting service mentioned it realized of the assault on September 16, 2022, including the marketing campaign impacted “many sufferer organizations.”
The fraudulent messages declare to inform customers that their CircleCI periods have expired and that they need to log in utilizing GitHub credentials by clicking on a hyperlink.
One other bogus electronic mail revealed by CircleCI prompts customers to register to their GitHub accounts to just accept the corporate’s new Phrases of Use and Privateness Coverage by following the hyperlink embedded within the message.
Whatever the lure, doing so redirects the goal to a lookalike GitHub login web page designed to steal and exfiltrate the entered credentials in addition to the Time-based One Time Password (TOTP) codes in real-time to the attacker, successfully permitting a 2FA bypass.
“Accounts protected by {hardware} safety keys usually are not susceptible to this assault,” GitHub’s Alexis Wales mentioned.
Amongst different ways embraced by the risk actor upon gaining unauthorized entry to the consumer account embrace creating GitHub private entry tokens (PATs), authorizing OAuth purposes, or including SSH keys to keep up entry even after a password change.
The attacker has additionally been noticed downloading personal repository contents, and even creating and including new GitHub accounts to a corporation ought to the compromised account have group administration permissions.
GitHub mentioned it has taken steps to reset passwords and take away maliciously-added credentials for impacted customers, alongside notifying these affected and suspending the actor-controlled accounts. It didn’t disclose the dimensions of the assault.
The corporate is additional urging organizations to think about using phishing-resistant {hardware} safety keys to stop such assaults.
The newest phishing assault comes a bit of over 5 months after GitHub suffered a extremely focused marketing campaign that resulted within the abuse of third-party OAuth consumer tokens maintained by Heroku and Travis CI to obtain personal repositories.