In keeping with a menace evaluation by Palo Alto Networks’ Unit 42, a misleading phishing method referred to as area shadowing is on the rise. It might even be extra prevalent than beforehand assumed by data safety specialists. Between April 25 and June 27 of 2022, the corporate discovered that 12,197 domains had been shadowed to supply malicious content material.
A shadow area is often a subdomain surreptitiously added on to a usually respected area that can painting one thing which may look respectable when it isn’t. So, for instance, should you had been to go to one thing like “yourbank[.]com” and requested to log in to your account, you may assume nothing of it. Nevertheless, shadowed domains may current as thisisactuallybad[.]yourbank[.]com. This web page is likely to be used to steal your login data with the same finish outcome to the pretend steam login browsers we lately reported on.

The report goes on to level out that detecting shadowed domains is kind of troublesome to do. In lots of circumstances, subdomains are sometimes simply and shortly configured, and often deliberately. For instance, net design corporations will deliberately ask for a subdomain if their consumer wants a redesign to make use of for testing. In different circumstances, it could be a legitimately added service that turns into hijacked. The strategy used for computerized detection from Unit 42 includes a number of circumstances needing to be met. It checks circumstances similar to verifying if the subdomains match the patterns of different subdomains on the area, if the IP handle that the subdomain factors to is considerably completely different from the unique, how lengthy the subdomain has been lively, and extra.
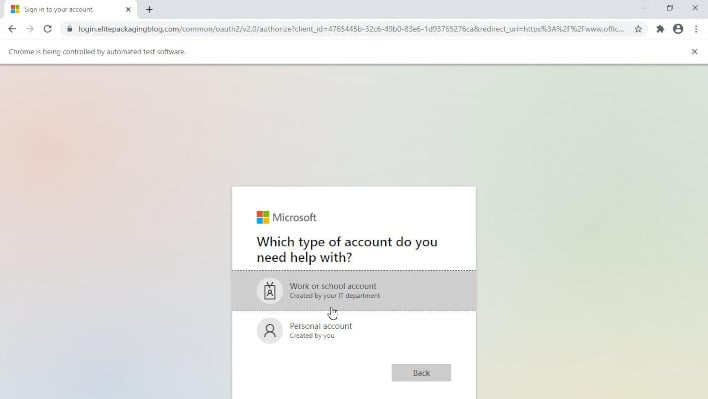
Screenshot of a false login proven from a shadowed area
There are a number of methods to look out for shadow domains your self. If you happen to’re a site proprietor, you’ll be able to examine to see if in case you have any subdomains you do not acknowledge in your DNS information. If you happen to do, change your password and, in some circumstances, your safety entry, then take away these subdomains. If you happen to’re a basic consumer, pay very shut consideration to the handle you are following a hyperlink for if it is in your e-mail, and pay shut consideration to who truly despatched the message. Additionally, if you’re prompted with a login, double examine the handle bar—if you’re not solely acquainted with the whole area identify, together with the subdomain, don’t log in. It’s possible you’ll even with to contact the institute during which you are making an attempt to entry their web page to verify particulars by way of your personal means. For instance, if it’s your financial institution, name your financial institution utilizing the quantity in your statements. You may learn the complete report from Unit 42 by clicking right here.


