ACM.87 How one change can have an effect on different working code, resulting in sudden catastrophe restoration and deployment failures
It is a continuation of my sequence of posts on Automating Cybersecurity Metrics.
I already fastened the error I’m going to write down about right here in a previous publish. I ended up penning this publish in the midst of making an attempt to create a user-specific secret in Secrets and techniques Supervisor, however I didn’t need to break up these posts so I moved this to the top. I hit a snag and needed to indicate how one can overcome it and issues it’s best to take into consideration with reference to manufacturing CloudFormation deployments.
Entry to KMS isn’t allowed (once more)
Even after utilizing my normal template to permit the IAM administrator group position to encrypt knowledge with the KMS key in my publish the place I used to be making an attempt to deploy a user-specific secret, I used to be getting an error stating that the IAM administrator didn’t have permission.
An error occurred (AccessDeniedException) when calling the CreateSecret operation: Entry to KMS isn't allowed
Now, this similar template for KMS key creation labored simply wonderful earlier than. Why would a script that labored completely wonderful earlier than be failing now?
The KMS error message, as I’ve written about earlier than, isn’t that useful. I do know that I permit entry to KMS each within the IAM coverage and useful resource coverage. Let’s have a look to confirm what the issue is.
First, a visit to CloudTrail logs. As with prior posts, I’m going to scroll over and search for an error message within the error column we added in a previous publish.
Effectively, that message is once more, not tremendous useful however let’s take a look at the small print by clicking on the log merchandise. The error message, once more, isn’t very useful.
What’s attention-grabbing is that I do know there’s one other error within the logs that isn’t showing with the default filter read-only=False. It additionally doesn’t present up once I set read-only = True. That is unusual to me as a result of both a log line is learn solely or it isn’t, so it ought to present up for one or the opposite, shouldn’t it?
I noticed the error final night time whereas testing earlier than so I do know there’s a associated error message. Let’s seek for KMS errors:
Now I see an Entry Denied error:
It’s occurring on the GenerateDataKey motion:
I don’t recall seeing this error earlier than whereas making an attempt to implement KMS scripts earlier on this sequence however possibly I’m simply forgetting. Anyway, let’s take a look at the small print:
Consumer: arn:aws:sts::xxxx:assumed-role/IAMAdminsGroup/botocore-session-xxxx isn't licensed to carry out: kms:GenerateDataKey on useful resource: arn:aws:kms:xxxx:xxxx:key/xxxx as a result of no resource-based coverage permits the kms:GenerateDataKey motion
How can this be? We handed that position in because the position allowed to encrypt knowledge with this key the identical manner we did earlier than utilizing the very same scripts. Let’s overview the useful resource coverage for the KMS key within the AWS console.
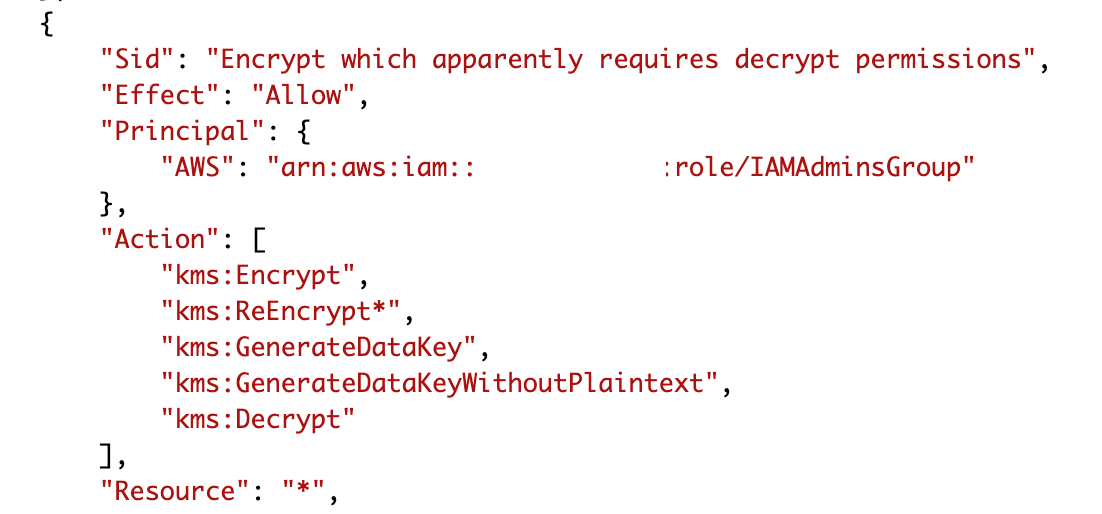
Clearly this coverage permits the IAMAdminsGroup position to carry out the GenerateDataKey motion:
I double checked the important thing ID and the important thing ID to which the coverage is connected matches the important thing ID within the error message. What??
Ah, however recall that I added some code to set a situation which varies relying on which service is requesting to make use of the KMS key. This situation will both be a secrets and techniques supervisor situation or this generic situation for the rest:
Let’s see what the occasion supply is on our error message. Nope that can also be appropriate within the merchandise that’s failing and giving us the entry denied message:
Again over in my KMS coverage deployment script I set the situation service to EC2 as a result of initially I used to be going to make use of this key to encrypt AWS EC2 cases.
In the event you recall from a previous publish when you’ve been following alongside, something apart from secrets and techniques supervisor makes use of the default situation. Effectively, we’re utilizing secrets and techniques supervisor nevertheless it wasn’t the occasion supply.
Inspecting the request additional we will see that this motion is invoked by service above the occasion supply line:
Let’s change the coverage situation service to secrets and techniques supervisor:
Deploy the brand new key coverage after which attempt to create the SSH key once more.
Check all the paths whenever you make a change
What I spotted at this level is that I had a typo (in addition to an extraneous double damaging) in my KMS YAML CloudFormation template. Though my template had labored for my new case of a non-secrets supervisor service, I forgot to return and validate the template was nonetheless working for the secrets and techniques supervisor situation.
I had a typo on this line that checks to see if the service is secrets and techniques supervisor (I spelled supervisor improper).
I additionally eliminated the “!Not” within the line above because it was further work for no motive and altered the following code to repair the logic accordingly.
After fixing that typo the code labored wonderful and the SSH key received uploaded to Secrets and techniques Supervisor.
Check the stuff you didn’t change, not simply the stuff you modified!
Effectively, I’m just one individual making an attempt to write down and take a look at all this code. Hopefully if you’re engaged on a mission vital or customer-facing system you will have a QA group in addition to a Dev group. The QA group ought to guarantee they take a look at not solely the issues that modified however something that is perhaps affected by the factor that modified. Automated testing is finest if doable as I discussed in a previous publish and am engaged on implementing together with my code.
There’s a take a look at script within the root listing of the GitHub repository related to these posts that in the end calls all my deploy scripts so I’ll want to return and guarantee that’s working once I’m performed right here.
Check deployments on high of what you will have in manufacturing and from scratch
Moreover, the templates don’t execute when there are not any adjustments to them, so as a way to actually take a look at CloudFormation templates you must do two issues:
- Check deploying new code from the prevailing state of the code in manufacturing. In the event you take a look at on another model or variation of the code you don’t know what’s going to occur whenever you deploy in manufacturing. Usually that is the aim of a staging setting.
- Delete and deploy all of the code from scratch and take a look at that after every change if you’re relying on these scripts in a catastrophe restoration situation. In any other case, you don’t actually know if they’re going to work or not.
On this case, I found the error once I tried to implement new code. I had not but gone again and examined my different code that leverages a KMS key along with AWS Secrets and techniques Supervisor. I’ll want to determine a take a look at script I can write to do this.
For now, I must get onto deploying an EC2 occasion that makes use of this SSH key and see if it really works.
Teri Radichel
In the event you appreciated this story please clap and comply with:
Medium: Teri Radichel or E mail Listing: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests companies by way of LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this sequence:
____________________________________________
Creator:
Cybersecurity for Executives within the Age of Cloud on Amazon
Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration take a look at or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety lessons, articles, white papers, shows, and podcasts