The Gootkit malware is prominently going after healthcare and finance organizations within the U.S., U.Okay., and Australia, in response to new findings from Cybereason.
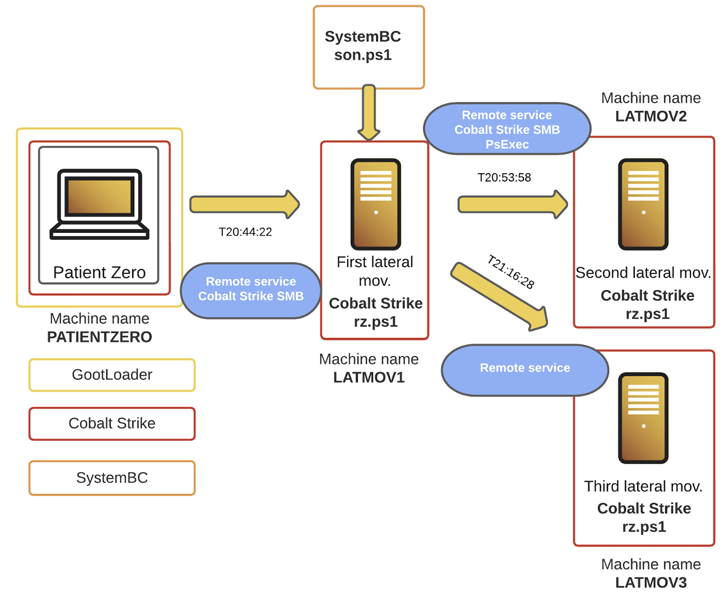
The cybersecurity agency stated it investigated a Gootkit incident in December 2022 that adopted a brand new methodology of deployment, with the actors abusing the foothold to ship Cobalt Strike and SystemBC for post-exploitation.
“The risk actor displayed fast-moving behaviors, shortly heading to manage the community it contaminated, and getting elevated privileges in lower than 4 hours,” Cybereason stated in an evaluation printed February 8, 2023.
Gootkit, additionally known as Gootloader, is completely attributed to a risk actor tracked by Mandiant as UNC2565. Beginning its life in 2014 as a banking trojan, the malware has since morphed right into a loader able to delivering next-stage payloads.
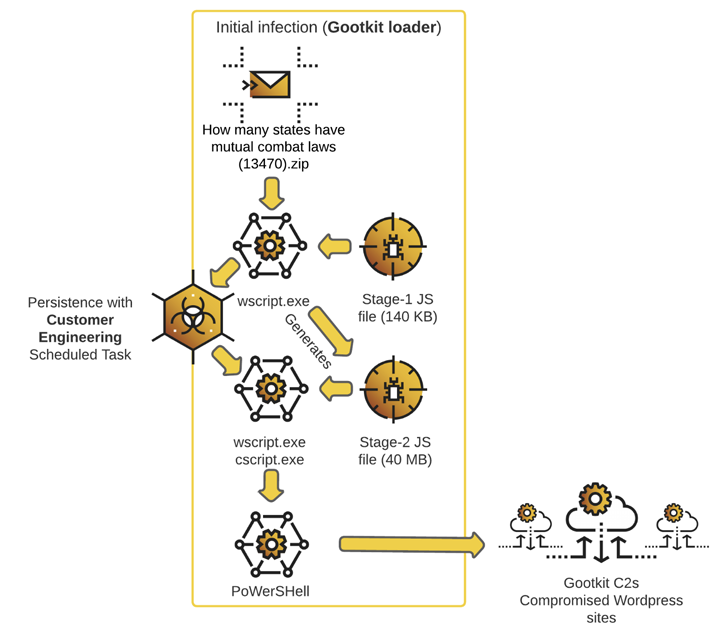
The shift in ways was first uncovered by Sophos in March 2021. Gootloader takes the type of heavily-obfuscated JavaScript recordsdata which might be served by compromised WordPress websites ranked greater in search engine outcomes by poisoning methods.
The assault chain depends on luring victims looking for agreements and contracts on DuckDuckGo and Google to the booby-trapped internet web page, finally resulting in the deployment of Gootloader.
The most recent wave can be notable for concealing the malicious code inside respectable JavaScript libraries reminiscent of jQuery, Chroma.js, Sizzle.js, and Underscore.js, which is then used to spawn a secondary 40 MB JavaScript payload that establishes persistence and launches the malware.
Within the incident examined by Cybereason, the Gootloader an infection is alleged to have paved the way in which for Cobalt Strike and SystemBC to conduct lateral motion and potential information exfiltration. The assault was finally foiled.
The disclosure comes amid the continued development of abusing Google Adverts by malware operators as an intrusion vector to distribute quite a lot of malware reminiscent of FormBook, IcedID, RedLine, Rhadamanthys, and Vidar.
The evolution of Gootloader into a classy loader is additional reflective of how risk actors are continually searching for new targets and strategies to maximise their income by pivoting to a malware-as-a-service (MaaS) mannequin and promoting that entry to different criminals.