Firstly of January, Gcore confronted an incident involving a number of L3/L4 DDoS assaults with a peak quantity of 650 Gbps. Attackers exploited over 2000 servers belonging to one of many high three cloud suppliers worldwide and focused a shopper who was utilizing a free CDN plan. Nevertheless, as a consequence of Gcore’s distribution of infrastructure and a lot of peering companions, the assaults have been mitigated, and the shopper’s net utility remained out there.
Why was mitigating these assaults so vital?
1. These assaults have been vital as a result of they exceeded the common bandwidth of comparable assaults by 60×. The carried out assaults relate to volume-based assaults focused to saturate the attacked utility’s bandwidth as a way to overflow it. Measuring complete quantity (bps)—moderately than the variety of requests—is the best way these assaults are normally tabulated.
The common bandwidth of this assault kind is mostly within the tens of Gbps (about 10 Gbps). Subsequently, the desired assaults (at 650 Gbps) exceeded the common worth by 60 instances. Assaults of this quantity are uncommon and are of specific curiosity to safety consultants.
Moreover, this worth (650 Gbps) is similar to the report DDoS assault on the most important Minecraft server (2.4 Tbps), solely one-fourth as large.
2. The shopper being attacked was utilizing a CDN plan with out extra DDoS safety. When purchasers use Gcore’s CDN (as a part of the Edge Community), the malicious visitors of the L3/L4 assaults immediately impacts solely its infrastructure (it serves as a filter), not the focused purchasers’ servers. The detrimental impression falls on the capability and connectivity of the infrastructure When a CDN is highly effective sufficient, it may well shield purchasers towards L3/L4 assaults—even when accessed utilizing a free plan.
What have been the technical specs of the assaults?
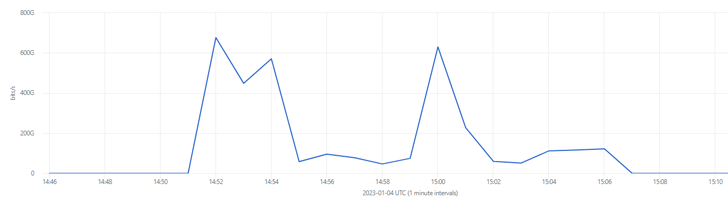
The length of the incident was quarter-hour, and at its peak, it reached over 650 Gbps. A doable motive why the incident took so lengthy is that the attackers weighed the ineffectiveness of the assaults (the shopper utility saved operating) towards their excessive value.
The incident consisted of three assaults with completely different vectors. They’re marked with visitors peaks on the diagram under:
- UDP flood assault (~650 Gbps). A whole lot of thousands and thousands of UDP packets have been despatched to the goal server to eat the bandwidth of the appliance and trigger its unavailability. Assaults of this vector use a scarcity of necessities of UDP connection institution: the attackers can ship packets with any information (it will increase the quantity) and use spoofed IP addresses (it makes it tough to seek out the sender).
- TCP ACK flood assault (~600 Gbps). Numerous packets with the ACK flag have been despatched to the goal server to overflow it. Assaults of this vector are based mostly on the truth that the junk TCP packets don’t embody a payload, however the server is compelled to course of them, and it might not have sufficient sources to deal with requests from actual finish customers. A CDN’s safety system is able to filtering packets and never forwarding them to the server if they don’t include payloads and should not certain to an open TCP session.
- A mixture of TCP and UDP (~600 Gbps). A customized variation of the earlier two varieties of assaults.
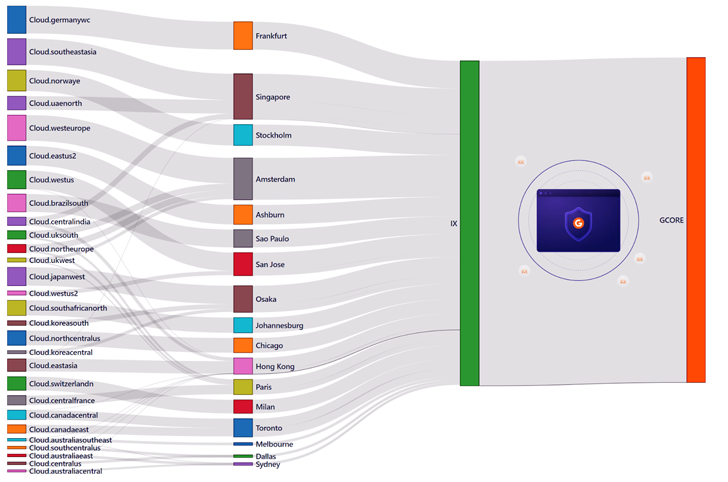
The distinctiveness of the incident was that the assaults have been carried out from a number of non-spoofed IP addresses. This allowed specialists to determine that the attackers used 2,143 servers in 44 completely different areas, and all the servers belonged to a single public cloud supplier. Using Anycast allowed Gcore to soak up the assault 100% over peering connections with this supplier.
Sankey diagram exhibiting the supply and circulate of the assault. Names of the places from the primary column are related to one of many high 3 cloud suppliers.
Why did the assaults not have an effect on the shopper?
1. Gcore’s connectivity by peering with many places performed a key function in mitigating the assaults. Gcore has over 11,000 peering companions (ISPs), and these companions join their networks utilizing cables and supply one another with entry to visitors originating from their networks. These connections enable for bypassing the general public web and immediately absorbing visitors from the peering companions. Moreover, this visitors is both freed from cost or prices a lot lower than visitors on the general public web. This low value makes it doable to guard buyer visitors on a free plan.
Within the context of the DDoS assault that occurred, the extent of connectivity drastically benefited the efficacy of mitigation. Gcore and the cloud supplier used to launch the assault are peering companions, so whereas the assault was taking place, Gcore was capable of ingest many of the visitors over the cloud supplier’s personal community. This drastically diminished the quantity of visitors that wanted to be dealt with by the general public web.
Personal peering additionally allows extra correct filtering and higher assault visibility, which results in extra environment friendly assault mitigation.
2. Gcore’s massive capability, as a result of placement of servers in lots of information facilities, additionally performed a job. Gcore’s edge servers are current in over 140 factors of presence and are based mostly on high-performance third technology Intel® Xeon® Scalable processors.
The general community capability is over 110 Tbps. With over 500 servers positioned in information facilities worldwide, the corporate is ready to stand up to large-scale DDoS assaults. So, the 650 Gbps of visitors may very well be distributed throughout the community, and every specific server would solely obtain 1-2 Gbps, which is an insignificant load.
Safety traits
In accordance with Gcore’s expertise, DDoS assaults will proceed to develop yr over yr. In 2021, the assaults reached 300 Gbps, and by 2022, they’d elevated to 700 Gbps. Subsequently, even small and medium-sized companies want to make use of distributed content material supply networks such because the CDN and Cloud to guard towards DDoS assaults.