A global legislation enforcement operation involving 11 nations has culminated within the takedown of a infamous cellular malware risk referred to as FluBot.
“This Android malware has been spreading aggressively by way of SMS, stealing passwords, on-line banking particulars and different delicate info from contaminated smartphones internationally,” Europol mentioned in a press release.
The “complicated investigation” included authorities from Australia, Belgium, Finland, Hungary, Eire, Romania, Spain, Sweden, Switzerland, the Netherlands, and the U.S.
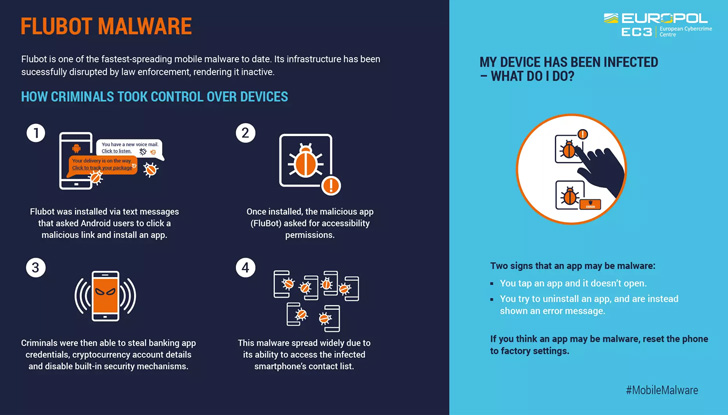
FluBot, additionally referred to as Cabassous, emerged within the wild in December 2020, masking its insidious intent behind the veneer of seemingly innocuous bundle monitoring purposes reminiscent of FedEx, DHL, and Correos.
It primarily spreads by way of smishing (aka SMS-based phishing) messages that trick unsuspecting recipients into clicking on a hyperlink to obtain the malware-laced apps.
As soon as launched, the app would proceed to request entry to Android’s Accessibility Service to stealthily siphon checking account credentials and different delicate info saved in cryptocurrency apps.
To make issues worse, the malware leveraged its entry to contacts saved within the contaminated gadget to propagate the an infection additional by sending messages containing hyperlinks to the FluBot malware.
FluBot campaigns, whereas primarily an Android malware, have additionally developed to focus on iOS customers in latest months, whereby customers making an attempt to entry the contaminated hyperlinks are redirected to phishing websites and subscription scams.
“This FluBot infrastructure is now underneath the management of legislation enforcement, placing a cease to the damaging spiral,” the company famous, including that the Dutch Police orchestrated the seizure final month.
Based on ThreatFabric’s cellular risk panorama report for H1 2022, FluBot was the second most lively banking trojan behind Hydra, accounting for 20.9% of the samples noticed between January and Might.
“ThreatFabric has carefully labored with legislation enforcement on the case,” founder and CEO Han Sahin advised The Hacker Information.
“It is an ideal win contemplating FluBot risk actors have or had one of the crucial resilient methods relating to distribution and internet hosting of their backends with DNS-tunneling by way of public DNS-over-HTTPS companies. This backend resilience in C2 internet hosting and fronting is what makes the efforts of the Dutch digital crime unit very spectacular.”
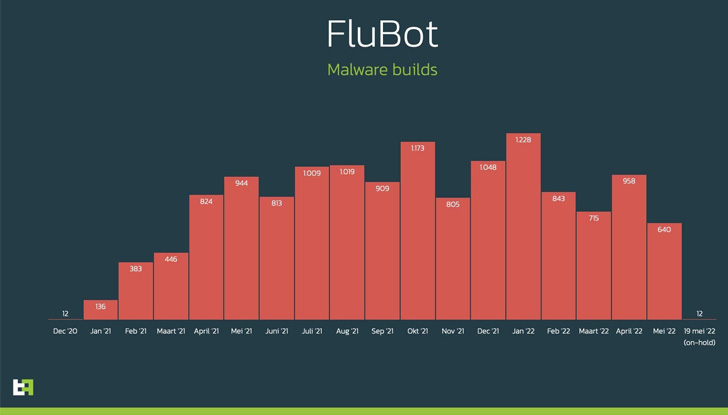
The Dutch cybersecurity firm additionally famous that distinctive malware samples developed by the operators of FluBot stopped after Might 19, coinciding with the takedown, successfully slowing their “worming efforts.”
“The general impression [of the dismantling] on the cellular risk panorama is proscribed since FluBot isn’t the strongest Android banking trojan,” Sahin added. “Exo, Anatsa, Gustuff, these are an actual downside to any person. The facility behind FluBot has all the time been [its] an infection numbers.”