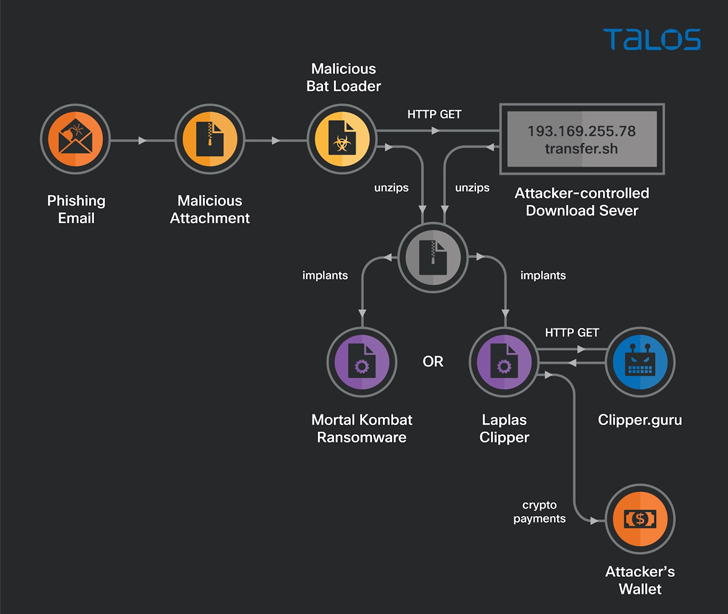
A brand new financially motivated marketing campaign that commenced in December 2022 has seen the unidentified menace actor behind it deploying a novel ransomware pressure dubbed MortalKombat and a clipper malware often known as Laplas.
Cisco Talos stated it “noticed the actor scanning the web for sufferer machines with an uncovered distant desktop protocol (RDP) port 3389.”
The assaults, per the cybersecurity firm, primarily focuses on people, small companies, and enormous organizations positioned within the U.S., and to a lesser extent within the U.Ok., Turkey, and the Philippines.
The place to begin that kicks off the multi-stage assault chain is a phishing e-mail bearing a malicious ZIP file that is used as a pathway to ship both the clipper or the ransomware.
Along with utilizing cryptocurrency-themed e-mail lures impersonating CoinPayments, the menace actor can also be identified to erase an infection markers in an try to cowl its tracks.
MortalKombat, first detected in January 2023, is able to encrypting system, software, backup, and digital machine information within the compromised system. It additional corrupts Home windows Explorer, disables the Run command window, and removes functions and folders from Home windows startup.
A supply code evaluation of the ransomware reveals that it is a part of the Xorist household of ransomware, Cisco Talos researcher Chetan Raghuprasad stated.
The Laplas clipper is a Golang variant of malware that got here to mild in November 2022. It is designed to observe the clipboard for any cryptocurrency pockets tackle and substitute it with an actor-controlled pockets to hold out fraudulent transactions.
“The clipper reads the sufferer machine’s clipboard contents and executes a perform to carry out common expression sample matching to detect the cryptocurrency pockets tackle,” Raghuprasad defined.
“When a cryptocurrency pockets tackle is recognized, the clipper sends the pockets tackle again to the clipper bot. In response, the clipper receives an attacker-controlled pockets tackle much like the sufferer’s and overwrites the unique cryptocurrency pockets tackle within the clipboard.”