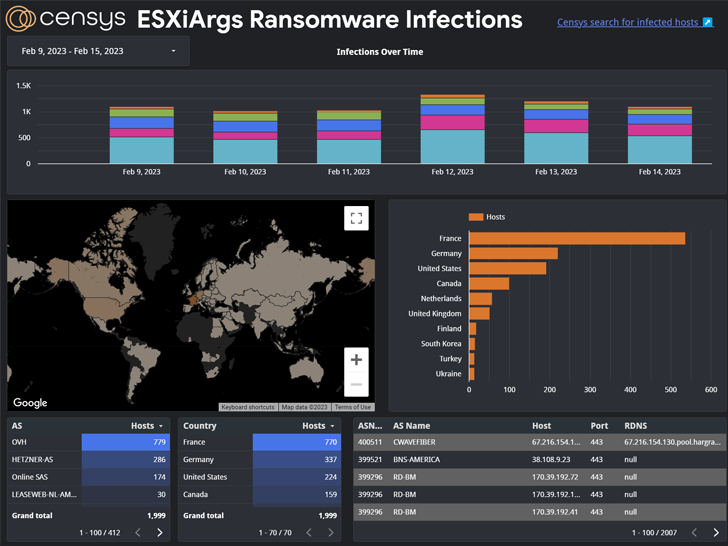
Greater than 500 hosts have been newly compromised en masse by the ESXiArgs ransomware pressure, most of that are positioned in France, Germany, the Netherlands, the U.Ok., and Ukraine.
The findings come from assault floor administration agency Censys, which found “two hosts with strikingly related ransom notes courting again to mid-October 2022, simply after ESXi variations 6.5 and 6.7 reached finish of life.”
The primary set of infections dates again to October 12, 2022, a lot sooner than when the marketing campaign started to realize traction at the beginning of February 2023. Then on January 31, 2023, the ransom notes on the 2 hosts are stated to have been up to date with a revised model that matches those used within the present wave.
A few of the essential variations between the 2 ransom notes embody the usage of an onion URL as a substitute of a Tox chat ID, a Proton Mail tackle on the backside of the notice, and a decrease ransom demand (1.05 Bitcoin vs. 2.09 Bitcoin).
“Every variant of the ransom notes from October 2022 via February 2023 are strikingly related in wording to the notice of an earlier ransomware variant, Cheerscrypt, which gained notoriety in early 2022,” researchers Mark Ellzey and Emily Austin stated.
It is price noting that ESXiArgs is suspected to be based mostly on the leaked Babuk ransomware code, which additionally spawned different variants resembling Cheerscrypt and PrideLocker final 12 months.
The event comes lower than per week after the menace actors returned with a brand new variant that tweaks the encryption methodology and the ransom notice following the discharge of a decryptor to assist get better contaminated techniques.
The U.S. Cybersecurity and Infrastructure Safety Company (CISA) has since acknowledged that the attackers are “doubtless concentrating on end-of-life ESXi servers or ESXi servers that shouldn’t have the out there ESXi software program patches utilized.”
“The vulnerability in VMware ESXi is a transparent reminder of the significance of retaining techniques updated with the newest safety patches whereas additionally using robust perimeter protection,” Bitdefender’s Martin Zugec stated.
“Attackers needn’t scour for brand new exploits or novel methods after they know that many organizations are weak to older exploits due, partly, to the dearth of correct patch administration and danger administration.”
The spike additionally coincides with an 87% year-over-year improve in ransomware assaults concentrating on industrial organizations in 2022, with 437 out of 605 assaults placing the manufacturing sector, per a new report from Dragos, partly fueled by continued evolution in ransomware-as-a-service (RaaS) fashions.
Information gathered by the commercial safety agency reveals that 189 ransomware assaults had been reported within the ultimate quarter of 2022 alone. High focused verticals included manufacturing (143), meals and beverage (15), power (14), pharma (9), oil and fuel (4), and mining (1).