Researchers found a essential safety vulnerability within the Screencastify Chrome extension that might enable webcam hijacking. An adversary might exploit this bug to sneakily report movies and steal movies alongside another information from the Google account the place the extension would save the video. Customers want to stay cautious because the bug stays partially unpatched (till scripting this story), thus risking the customers.
Screencastify Chrome Extension Vulnerability
Screencastify is a display screen recording Chrome browser extension that gained reputation for instructional and instructing functions. The extension permits the person to start out display screen recording and make movies through webcam. The person can then retailer advert share these movies with others as wanted.
Whereas the aim sounds helpful, any vulnerability on this extension could be equally deadly for a person’s on-line safety.
Based on a latest put up from Palant, a cross-site scripting vulnerability riddled Screencastify Chrome extension, threatening person safety.
The standard performance of Screencastify consists of integration with its web site for video-editing options and gaining full entry to Google Drive to retailer recorded movies. In addition to, quite a few corporations personal the Screencastify subdomains for numerous functionalities (excluding internet hosting firms), which can be liable to XSS vulnerabilities.
Thus, out of curiosity, the researcher analyzed Screencastify net pages and located an XSS flaw on the error web page. This error web page seems when the person tries to submit one other video following a beforehand uploaded one to a Classroom project.
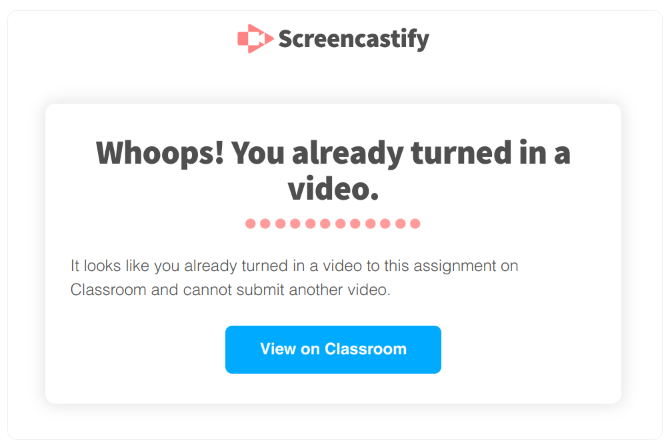
Supply: Palant.information
That’s the place the issue existed. As said within the put up,
This error web page is situated below a set deal with, so it may be opened immediately moderately than triggering the error situation.
Then, whereas clicking on the “View on Classroom” button ought to direct a person to a Google Classroom, the vulnerability existed in window.open(this.courseworkLink); the place the question parameter this.courseworkLink had no hyperlink variation in between. Therefore, the web page remained susceptible to clickjacking assaults.
The place does
this.courseworkLinkcome from? It’s a question string parameter. Is there some hyperlink validation in between? Nope. So, if the question string parameter is one thing likejavascript:alert(doc.area), will clicking this button run JavaScript code within the context of the screencastify.com area? It positive will!
Partial Patch Deployed
An adversary might exploit this vulnerability to retrieve Google OAuth entry tokens, entry Google Drive contents, and sneakily report movies through webcam.
After discovering the vulnerability, the researcher reached out to the distributors, who acknowledged the bug.
Nevertheless, the researcher fears that the issue nonetheless exists because the distributors have solely partially addressed the matter. Till scripting this story, Screencastify Model 2.70.0.4517 has arrived with partial fixes, forsaking a couple of Screencastify-managed subdomains and one by a single vendor. So, customers could anticipate to obtain one other replace quickly with full fixes. However till then, it’s higher to restrict utilizing Screencastify to stay protected from potential exploitation.


