ACM.46 DRY. Don’t Repeat Your self.
This can be a continuation of my collection on Automating Cybersecurity Metrics.
Earlier than I get began on this subsequent weblog publish a small request. For those who see plagiarism of my posts or anybody else’s, please do an creator a favor and report it:
I’ve written about DRY or Don’t Repeat Your self by way of software program programming earlier than. It’s one in every of my favourite ideas.
I’m penning this framework I’m engaged on as if it’s a giant group with totally different departments. Every division could have their very own code repositories. As well as, the group could have some code it needs to share by means of the corporate, type of like an inside open supply code repository. Maybe there’s and structure or DevOps group that has a set of capabilities that could be helpful all through the corporate.
Once I labored at a financial institution we ran batch jobs and all of the batch jobs used a standard library in order that they labored similarly. That batch job library was in its personal repository. Modifications to this vital part might trigger a number of issues to interrupt in order that they had been dealt with with care.
Equally, our functions relied on Java and a corresponding open-source jar file. A undertaking to replace the model of Java to repair a vulnerability for the whole set of batch jobs used within the firm took a couple of yr as a result of every vital banking software and the central part utilized by all of them wanted to be re-tested to make sure nothing broke and calculations weren’t affected by the improve.
Counting on a centralized frequent set of code could cause points on the subject of updating that centralized code. Then again, our frequent batch job library was a very good design and it helped all of the batch jobs run in a constant method. We had a scheduling software that would run all of the batch jobs and the operations group understood the right way to handle them since they stunning a lot all labored the identical approach. It was doable to have totally different batch jobs utilizing totally different variations of the core library all through the improve course of so functions may very well be upgraded in precedence order.
The trade-offs between shared and one-off code could be difficult to judge. Nevertheless, planning out how you’ll handle upgrades may help overcome any of the downsides of utilizing frequent code the place you may. GitHub makes issues a bit simpler as a result of a group can use code from a repository as is, use the code from a selected department, or fork the code after which suggest updates again to the first repo.
Once we had been having challenges maintaining with developer demand for networking at Capital One I proposed this concept of permitting folks to fork the code and suggest modifications. I feel it was a good suggestion however the complexity of reviewing networking by way of code versus taking a look at a community design was not possible. We nonetheless wanted different mechanisms for reviewing the modifications.
You’ll probably need a greater option to validate the code than trying on the code itself in lots of instances. Though code evaluations are useful, it’s too simple to overlook one thing within the particulars. You should still have somebody present documentation representing their design. Then you would have a QA group deploy the code and validate it matches the design or run automated instruments over the code and deployments to carry out some type of validation.
In any case, I like the concept of getting an skilled and security-minded group accountable for vital code in a standard repository and permit others to suggest modifications. When you may summary out frequent code you might be able to scale back the effort and time to get new functions deployed, and scale back safety bugs. When much less skilled builders suggest modifications which have safety issues to centralized repositories, the extra skilled group or who occurs to know the code base higher can clarify the issue and everybody can study from the expertise. Win-win!
A repository for shared code
In my previous refactoring weblog posts I created some shared capabilities particular to a selected subfolder such because the perform to deploy an IAM CloudFormation stack. Solely the IAM admins ought to require the IAM Capabilities choice when deploying a stack, in order that perform can stay throughout the IAM subfolder.
Nevertheless, we will create a perform to deploy CloudFormation stacks for almost every little thing else that doesn’t require that functionality. I created a brand new “Capabilities” folder on the root and added a file referred to as shared_functions.sh.
In my explicit repository I’m mocking up what might grow to be totally different repositories managed by totally different components of the group — KMS, IAM, and the repositories managed by builders akin to Lambda and Jobs. Sooner or later, if these had been separate repositories, groups might obtain the shared code to make use of of their deployments and replace it periodically if it modifications. For now, I’m merely going to incorporate the code by referencing it the place it exists within the frequent folder.
Shared capabilities
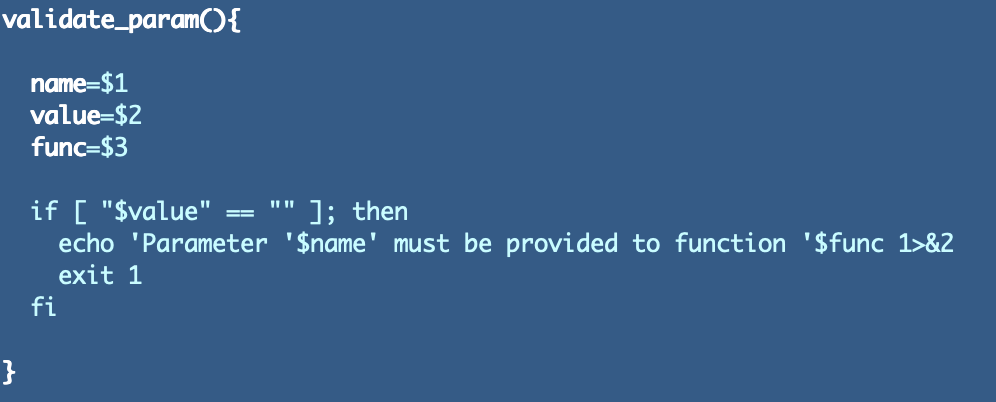
In the intervening time these are the capabilities in our shared library. I moved our perform over that validates that parameters don’t comprise an empty string. I added the power to exit with an error so we will terminate the calling code when the error happens by including >&2 after the error message echo and an exit 1 command.
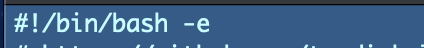
For those who had been questioning what this line is on the prime of all my bash scripts it’s referred to as a shebang.
It tells the working system what sort of code is within the script and what program to make use of to execute the code. I might put python right here if I used to be writing code after which I might simply double click on to execute the file as an alternative of typing python in entrance of the file title. On this case, we’re utilizing bash.
The -e on the finish signifies that I would like this system to exit every time there’s an error. Within the above perform, earlier than I had the exit code indicating an error, my scripts didn’t acknowledge that there was an issue and would proceed to execute. Now that drawback is fastened.
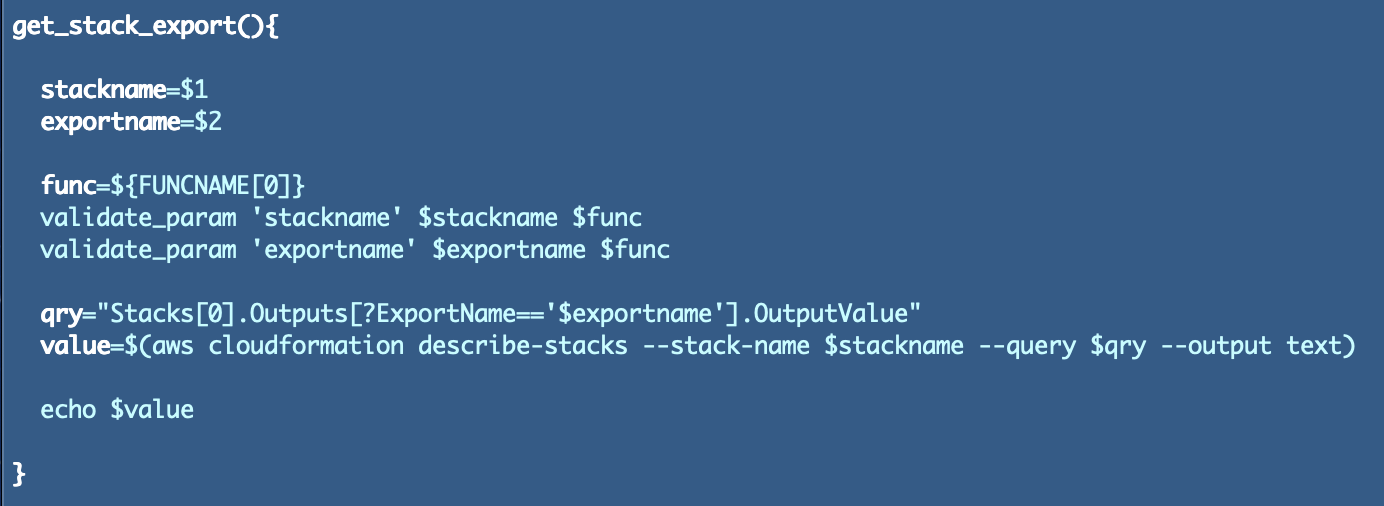
There’s a perform to get an export from a stack, since that is code that may grow to be a bit difficult and error susceptible.
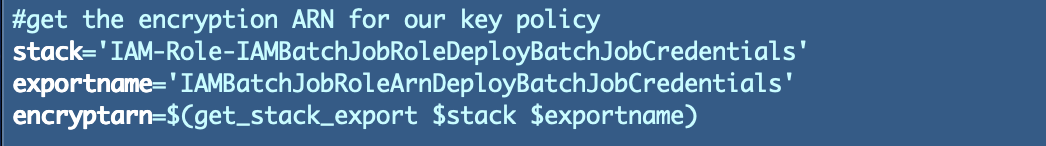
I retrieve outputs to acquire parameters utilized in a few of the KMS CloudFormation templates.
Lastly we’ve our frequent perform to deploy a stack that doesn’t require IAM_CAPABILITIES.
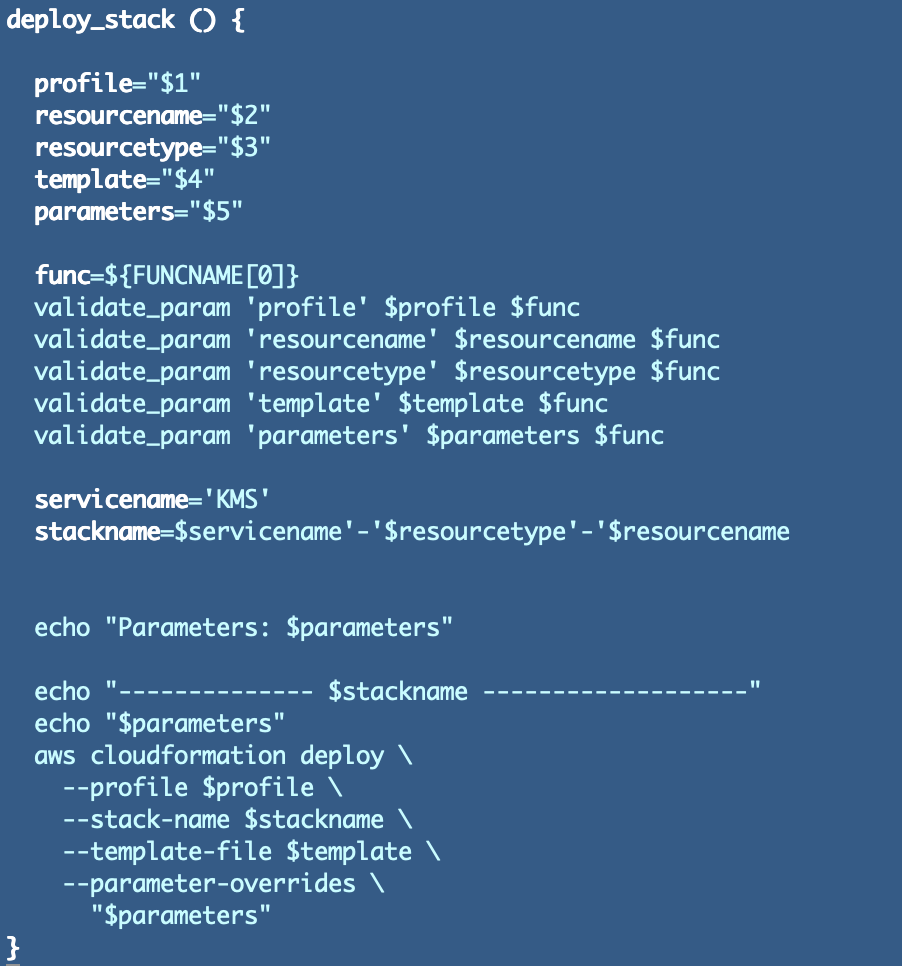
I added the road above to get the present perform title:
func=${FUNCNAME[0]}
That approach I can cross it into the validate_param perform above. The perform can return a pleasant error message that tells me precisely which argument in precisely which perform is receiving an empty string when it mustn’t. I already can consider different methods to enhance this code however for the second we’ll transfer on.
Initially I saved the stack deployment perform particular to IAM within the IAM subfolder however later I moved it into frequent capabilities as a result of I wanted to make use of it throughout two repositories. I altered the frequent perform so I might run an IAM stack from it. I additionally realized that I don’t all the time must cross in parameters so I needed to deal with that state of affairs as nicely.
One different factor I bumped into was passing parameters with areas into CloudFormation stacks. I needed to alter the parameters two other ways. The primary methodology labored once I wrote the AWS CLI command out usually. I needed to revise it once more when forming the CLI command as a concatenated string as I’m doing beneath. I’m going into element on this publish on the modifications I needed to make.
As I point out within the above publish, I’m additionally not totally up on the safety ramifications with out performing some fuzzing and pentesting on all if this. However I’m hoping to maneuver to a greater programming language with a greater option to validate parameters and kinds sooner or later so I’m leaving it this manner for now.
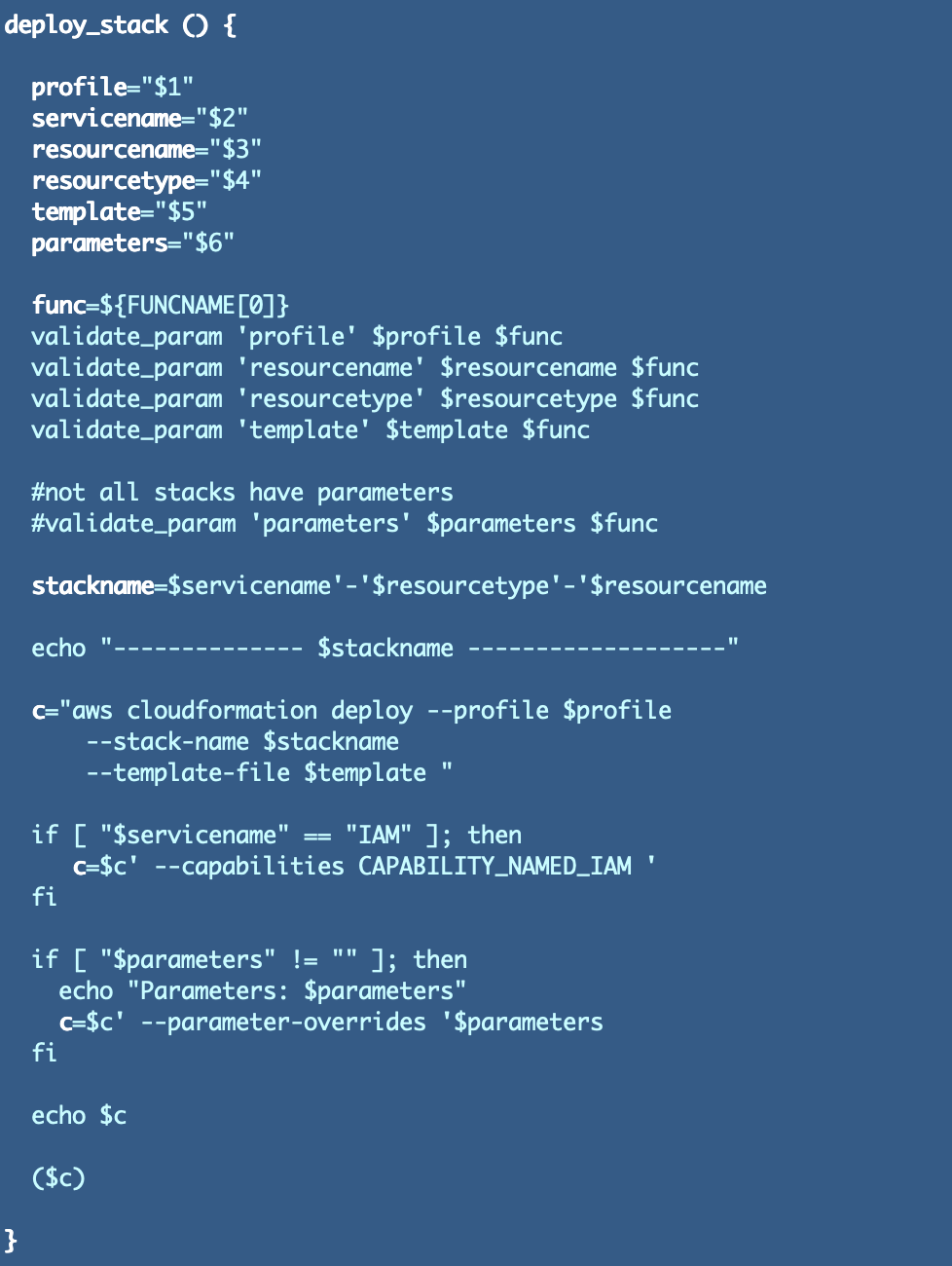
Since I already had a number of issues calling my perform to deploy an IAM stack I added which I can take away later if I need to replace all the opposite code. Nevertheless it’s additionally type of good to have a perform particularly for IAM and have the ability to cross in much less parameters. This method is just like the decorator sample in object oriented programming. I don’t really want to set all of the parameters beneath. That code does nothing however I did so only for readability.
Teri Radichel
For those who preferred this story please clap and observe:
Medium: Teri Radichel or E mail Record: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests companies by way of LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this collection:
____________________________________________
Creator:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety lessons, articles, white papers, shows, and podcasts


