An evaluation of leaked chats from the infamous Conti ransomware group earlier this yr has revealed that the syndicate has been engaged on a set of firmware assault strategies that might provide a path to accessing privileged code on compromised units.
“Management over firmware offers attackers nearly unmatched powers each to immediately trigger injury and to allow different long-term strategic objectives,” firmware and {hardware} safety agency Eclypsium mentioned in a report shared with The Hacker Information.
“Such degree of entry would enable an adversary to trigger irreparable injury to a system or to ascertain ongoing persistence that’s nearly invisible to the working system.”
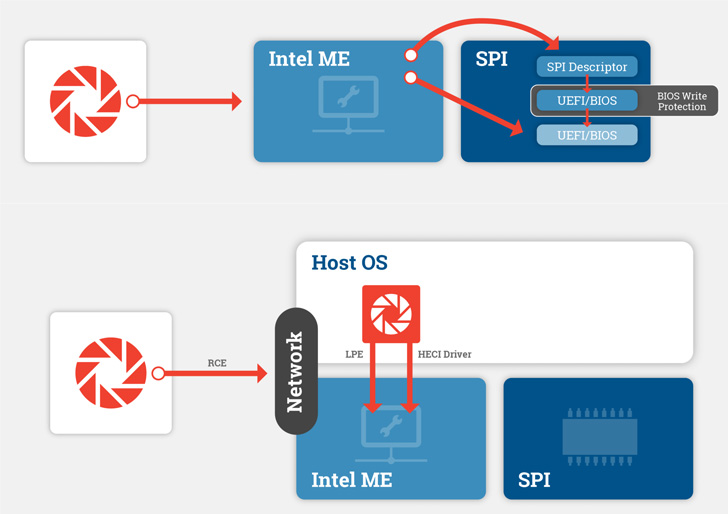
Particularly, this contains assaults geared toward embedded microcontrollers such because the Intel Administration Engine (ME), a privileged element that is a part of the corporate’s processor chipsets and which may utterly bypass the working system.
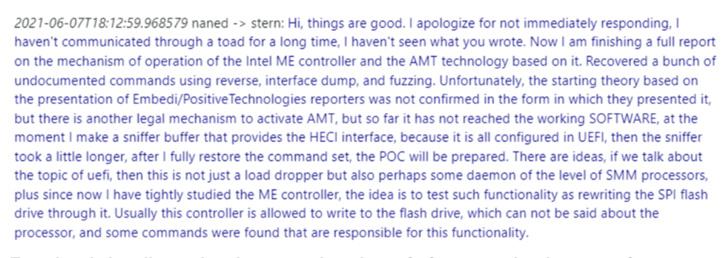
The conversations among the many Conti members, which leaked after the group pledged its help to Russia within the latter’s invasion of Ukraine, have make clear the syndicate’s makes an attempt to mine for vulnerabilities associated to ME firmware and BIOS write safety.
This entailed discovering undocumented instructions and vulnerabilities within the ME interface, reaching code execution within the ME to entry and rewrite the SPI flash reminiscence, and dropping System Administration Mode (SMM)-level implants, which might be leveraged to even modify the kernel.
The analysis finally manifested within the type of a proof-of-concept (PoC) code in June 2021 that may achieve SMM code execution by gaining management over the ME after acquiring preliminary entry to the host via conventional vectors like phishing, malware, or a provide chain compromise, the leaked chats present.
“By shifting focus to Intel ME in addition to focusing on units through which the BIOS is write protected, attackers might simply discover much more accessible goal units,” the researchers mentioned.
That is not all. Management over the firmware is also exploited to realize long-term persistence, evade safety options, and trigger irreparable system injury, enabling the menace actor to mount harmful assaults as witnessed in the course of the Russo-Ukrainian conflict.
“The Conti leaks uncovered a strategic shift that strikes firmware assaults even additional away from the prying eyes of conventional safety instruments,” the researchers mentioned.
“The shift to ME firmware offers attackers a far bigger pool of potential victims to assault, and a brand new avenue to reaching essentially the most privileged code and execution modes accessible on trendy techniques.”