Cybersecurity researchers have found the real-world identification of the risk actor behind Golden Chickens malware-as-a-service, who goes by the net persona “badbullzvenom.”
eSentire’s Menace Response Unit (TRU), in an exhaustive report revealed following a 16-month-long investigation, mentioned it “discovered a number of mentions of the badbullzvenom account being shared between two individuals.”
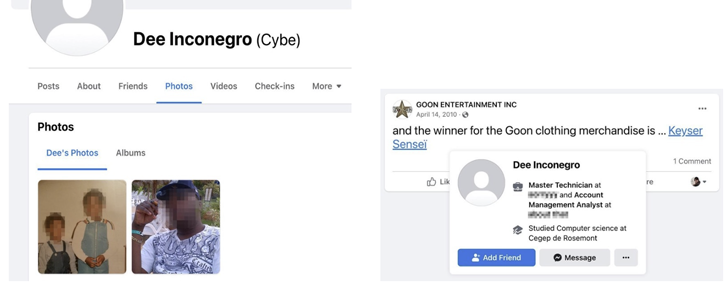
The second risk actor, often called Frapstar, is alleged to determine themselves as “Chuck from Montreal,” enabling the cybersecurity agency to piece collectively the legal actor’s digital footprint.
This consists of his actual identify, photos, residence tackle, the names of his mother and father, siblings, and pals, alongside together with his social media accounts and his pursuits. He’s additionally mentioned to be the only real proprietor of a small enterprise that is run from his own residence.
Golden Chickens, also called Venom Spider, is a malware-as-a-service (MaaS) supplier that is linked to quite a lot of instruments akin to Taurus Builder, software program to create malicious paperwork; and More_eggs, a JavaScript downloader that is used to serve further payloads.
The risk actor’s cyber arsenal has been put to make use of by different distinguished cybercriminal teams like Cobalt Group (aka Cobalt Gang), Evilnum, and FIN6, all of that are estimated to have collectively triggered losses totaling $1.5 billion.
Previous More_eggs campaigns, some relationship again to 2017, have concerned spear-phishing enterprise professionals on LinkedIn with bogus job affords that give risk actors distant management over the sufferer’s machine, leveraging it to reap info or deploy extra malware.
Final 12 months, in a reversal of kinds, the identical techniques had been employed to strike company hiring managers with resumes laden with malware as an an infection vector.
The earliest documented file of Frapster’s exercise goes again to Might 2015, when Pattern Micro described the person as a “lone legal” and a luxurious automotive fanatic.
“‘Chuck,’ who makes use of a number of aliases for his underground discussion board, social media, and Jabber accounts, and the risk actor claiming to be from Moldova, have gone to nice lengths to disguise themselves,” eSentire researchers Joe Stewart and Keegan Keplinger mentioned.
“They’ve additionally taken nice pains to obfuscate the Golden Chickens malware, attempting to make it undetectable by most AV firms, and limiting clients to utilizing Golden Chickens for ONLY focused assaults.”
It is suspected that Chuck is without doubt one of the two risk actors working the badbullzvenom account on the Exploit.in underground discussion board, with the opposite celebration presumably positioned in Moldova or Romania, eSentire famous.
The Canadian cybersecurity firm mentioned it additional uncovered a brand new assault marketing campaign concentrating on e-commerce firms, tricking recruiters into downloading a rogue Home windows shortcut file from an internet site that masquerades as a resume.
The shortcut, a malware dubbed VenomLNK, serves as an preliminary entry vector to drop More_eggs or TerraLoader, which subsequently acts as a conduit to deploy completely different modules, particularly TerraRecon (for sufferer profiling), TerraStealer (for info theft), and TerraCrypt (for ransomware extortion).
“The malware suite continues to be actively being developed and is being and offered to different risk actors,” the researchers concluded, urging organizations to be looking out for potential phishing makes an attempt.