The China-aligned espionage-focused actor dubbed Winnti has set its sights on authorities organizations in Hong Kong as a part of an ongoing marketing campaign dubbed Operation CuckooBees.
Energetic since at the very least 2007, Winnti (aka APT41, Barium, Bronze Atlas, and Depraved Panda) is the title designated to a prolific cyber menace group that carries out Chinese language state-sponsored espionage exercise, predominantly geared toward stealing mental property from organizations in developed economies.
The menace actor’s campaigns have focused healthcare, telecoms, high-tech, media, agriculture, and schooling sectors, with an infection chains primarily counting on spear-phishing emails with attachments to initially break into the victims’ networks.
Earlier this Might, Cybereason disclosed long-running assaults orchestrated by the group since 2019 to siphon expertise secrets and techniques from expertise and manufacturing firms primarily situated in East Asia, Western Europe, and North America.
The intrusions, clubbed underneath the moniker Operation CuckooBees, are estimated to have resulted within the exfiltration of “tons of of gigabytes of data,” the Israeli cybersecurity firm revealed.
The most recent exercise, in response to the Symantec Menace Hunter workforce, a part of Broadcom Software program, is a continuation of the proprietary knowledge theft marketing campaign, however with a concentrate on Hong Kong.
The attackers remained energetic on among the compromised networks for so long as a 12 months, the corporate stated in a report shared with The Hacker Information, including the intrusions paved the best way for the deployment of a malware loader known as Spyder, which first got here to mild in March 2021.
“[Spyder] is getting used for focused assaults on info storage methods, accumulating details about corrupted gadgets, executing mischievous payloads, coordinating script execution, and C&C server communication,” the SonicWall Seize Labs Menace Analysis Group famous on the time.
Additionally deployed alongside Spyder have been different post-exploitation instruments, reminiscent of Mimikatz and a trojanized zlib DLL module that is able to receiving instructions from a distant server or loading an arbitrary payload.
Symantec stated that it didn’t observe the supply of any final-stage malware, though the motives of the marketing campaign are suspected to be linked to intelligence gathering primarily based on tactical overlaps with earlier assaults.
“The truth that this marketing campaign has been ongoing for a number of years, with completely different variants of the Spyder Loader malware deployed in that point, signifies that the actors behind this exercise are persistent and targeted adversaries, with the power to hold out stealthy operations on sufferer networks over an extended time period,” Symantec stated.
Winnti targets Sri Lankan authorities entities
As an additional signal of Winnti’s sophistication, Malwarebytes uncovered a separate set of assaults concentrating on authorities entities in Sri Lanka in early August with a brand new backdoor known as DBoxAgent that leverages Dropbox for command-and-control.
“To our information, Winnti (a China-backed APT) is concentrating on Sri Lanka for the primary time,” the Malwarebytes Menace Intelligence workforce stated.
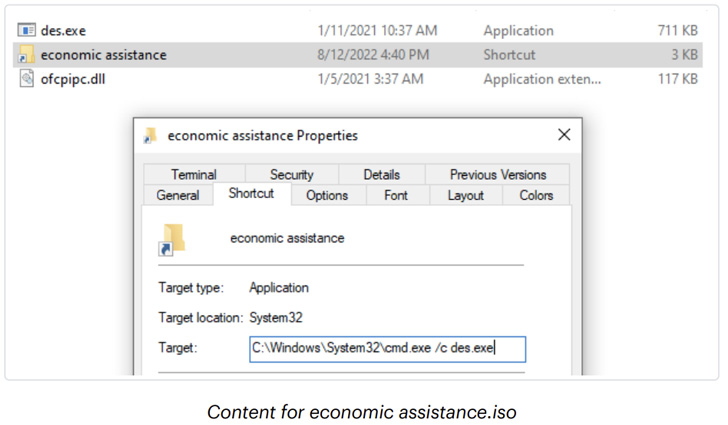
The killchain can be notable for making use of an ISO picture hosted on Google Drive that purports to be a doc containing details about financial help, indicating an try by the menace actor to capitalize on the ongoing financial disaster within the nation.
Launching an LNK file contained inside the ISO picture results in the execution of the DBoxAgent implant that allows the adversary to distant commandeer the machine and export delicate knowledge again to the cloud storage service. Dropbox has since disabled the rogue account.
The backdoor additional acts as a conduit to drop exploitation instruments that may open the door for different assaults and knowledge exfiltration, together with activating a multi-stage an infection sequence that culminates in using a complicated C++ backdoor named KEYPLUG, which was documented by Google’s Mandiant in March 2022.
The event marks the primary time APT41 has been noticed using Dropbox for C&C functions, illustrating the rising use by attackers of respectable software-as-a-service and cloud choices to host malicious content material.
“Winnti stays energetic and its arsenal retains rising as one of the crucial refined teams these days,” the cybersecurity agency stated. “Sri Lanka’s location in South Asia is strategic for China because it has open entry to the Indian Ocean and is near India.”