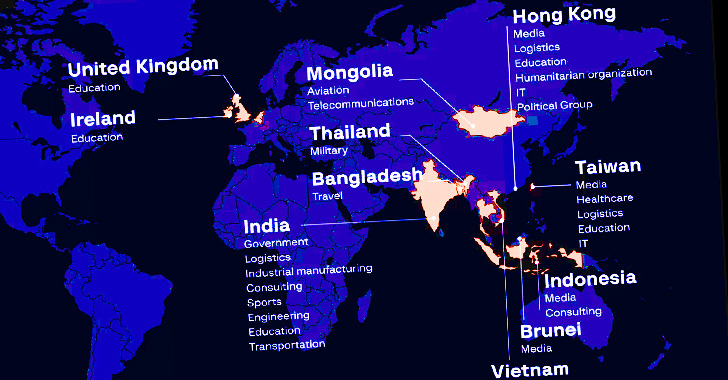
The Chinese language superior persistent risk (APT) actor tracked as Winnti (aka APT41) has focused not less than 13 organizations geographically spanning throughout the U.S, Taiwan, India, Vietnam, and China towards the backdrop of 4 totally different campaigns in 2021.
“The focused industries included the general public sector, manufacturing, healthcare, logistics, hospitality, training, in addition to the media and aviation,” cybersecurity agency Group-IB stated in a report shared with The Hacker Information.
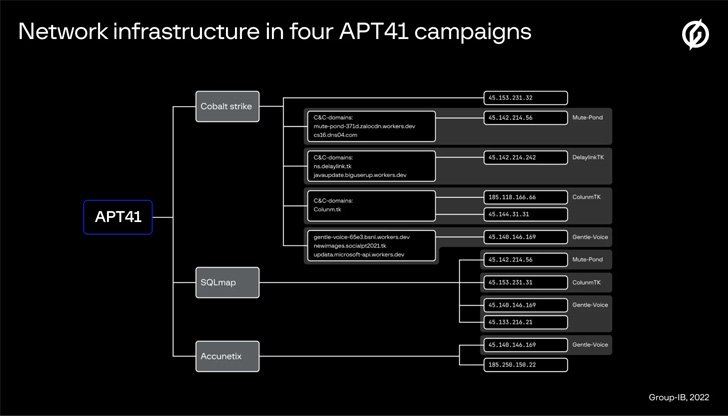
This additionally included the assault on Air India that got here to gentle in June 2021 as a part of a marketing campaign codenamed ColunmTK. The opposite three campaigns have been assigned the monikers DelayLinkTK, Mute-Pond, and Light-Voice based mostly on the domains used within the assaults.
APT41, also referred to as Barium, Bronze Atlas, Double Dragon, Depraved Panda, or Winnti, is a prolific Chinese language cyber risk group that is recognized to hold out state-sponsored espionage exercise in parallel with financially motivated operations not less than since 2007.
Describing 2021 as an “intense 12 months for APT41,” assaults mounted by the adversary concerned primarily leveraging SQL injections on focused domains because the preliminary entry vector to infiltrate sufferer networks, adopted by delivering a customized Cobalt Strike beacon onto the endpoints.
“APT41 members normally use phishing, exploit numerous vulnerabilities (together with Proxylogon), and conduct watering gap or supply-chain assaults to initially compromise their victims,” the researchers stated.
Different actions carried out post-exploitation ranged from establishing persistence to credential theft and conducting reconnaissance by means of living-off-the-land (LotL) strategies to assemble details about the compromised atmosphere and laterally transfer throughout the community.
The Singapore-headquartered firm stated it recognized 106 distinctive Cobalt Strike servers that have been solely utilized by APT41 between early 2020 and late 2021 for command-and-control. Many of the servers are now not lively.
The findings mark the continued abuse of the professional adversary simulation framework by totally different risk actors for post-intrusion malicious actions.
“Previously, the instrument was appreciated by cybercriminal gangs concentrating on banks, whereas at the moment it’s widespread amongst numerous risk actors no matter their motivation, together with notorious ransomware operators,” Group-IB Menace Analyst, Nikita Rostovtsev, stated.