A Brazilian menace actor generally known as Prilex has resurfaced after a year-long operational hiatus with a complicated and sophisticated malware to steal cash by the use of fraudulent transactions.
“The Prilex group has proven a excessive degree of data about credit score and debit card transactions, and the way software program used for fee processing works,” Kaspersky researchers mentioned. “This allows the attackers to maintain updating their instruments with a purpose to discover a method to circumvent the authorization insurance policies, permitting them to carry out their assaults.”
The cybercrime group emerged on the scene with ATM-focused malware assaults within the South American nation, offering it the flexibility to interrupt into ATM machines to carry out jackpotting – a kind of assault aiming to dispense money illegitimately – and clone hundreds of bank cards to steal funds from the focused financial institution’s clients.
Prilex’s modus operandi over time has since developed to make the most of processes referring to point-of-sale (PoS) software program to intercept and modify communications with digital gadgets corresponding to PIN pads, that are used to facilitate funds utilizing debit or bank cards.
Identified to be lively since 2014, the operators are additionally adept at finishing up EMV replay assaults by which site visitors from a legit EMV-based chip card transaction is captured and replayed to a fee processor like Mastercard, however with the transaction fields modified to incorporate stolen card knowledge.
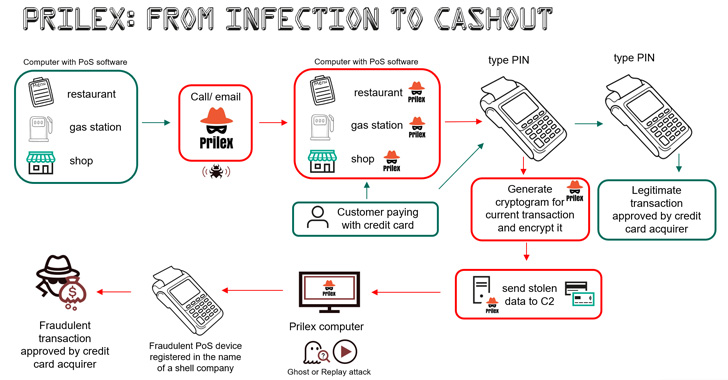
Infecting a pc with PoS software program put in is a highly-targeted assault incorporating a social engineering ingredient that enables the menace actor to deploy the malware.
“A goal enterprise could obtain a name from a ‘technician’ who insists that the corporate must replace its PoS software program,” the researchers famous. “The faux technician could go to the goal in particular person or request the victims to put in AnyDesk and supply distant entry for the ‘technician’ to put in the malware.”
The newest installments noticed in 2022, nevertheless, exhibit one essential distinction in that the replay assaults have been substituted with an alternate method to illicitly money out funds utilizing cryptograms generated by the sufferer card throughout the in-store fee course of.
The strategy, known as GHOST transactions, features a stealer element that grabs all communications between the PoS software program and the PIN pad used for studying the cardboard throughout the transaction with the aim of acquiring the cardboard data.
That is subsequently transmitted to a command-and-control (C2) server, allowing the menace actor to make transactions by means of a fraudulent PoS machine registered within the title of a faux firm.
Now, it is price mentioning that EMV chip playing cards use what’s known as a cryptogram to safe cardholder knowledge each time a transaction is made. That is completed in order to validate the id of the cardboard and the approval from the cardboard issuer, thereby decreasing the danger of counterfeit transactions.
Whereas earlier variations of Prilex circumvented these safety measures by monitoring the continued transaction to get the cryptogram and conduct a replay assault utilizing the collected “signature,” the GHOST assault requests for brand spanking new EMV cryptograms which can be put to make use of to finish the rogue transactions.
Additionally baked into the malware is a backdoor module that is engineered to debug the PoS software program conduct and make adjustments on the fly. Different backdoor instructions authorize it to terminate processes, begin and cease display screen captures, obtain arbitrary recordsdata from the C2 server, and execute instructions utilizing CMD.
Prilex is “dealing straight with the PIN pad {hardware} protocol as an alternative of utilizing larger degree APIs, doing real-time patching in goal software program, hooking working system libraries, messing with replies, communications and ports, and switching from a replay-based assault to generate cryptograms for its GHOST transactions even from bank cards protected with CHIP and PIN expertise,” the researchers mentioned.