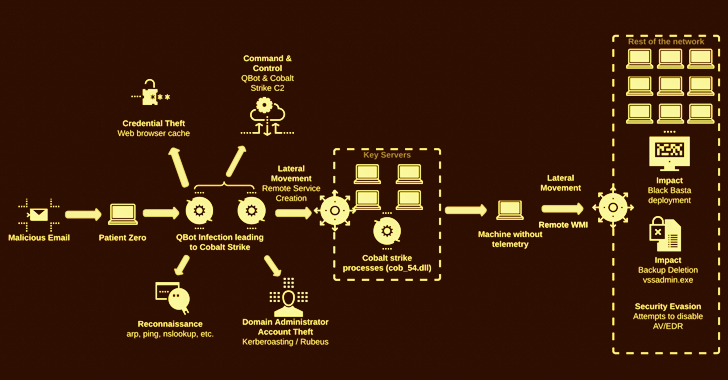
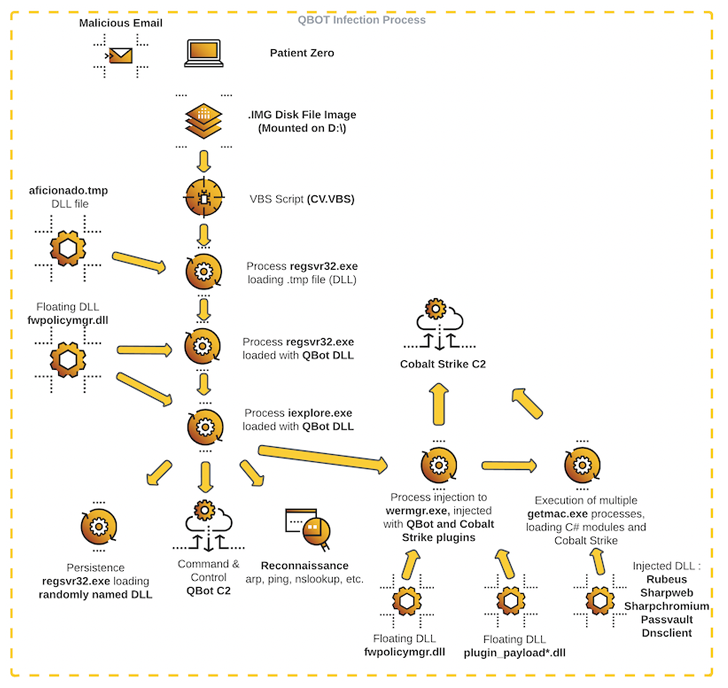
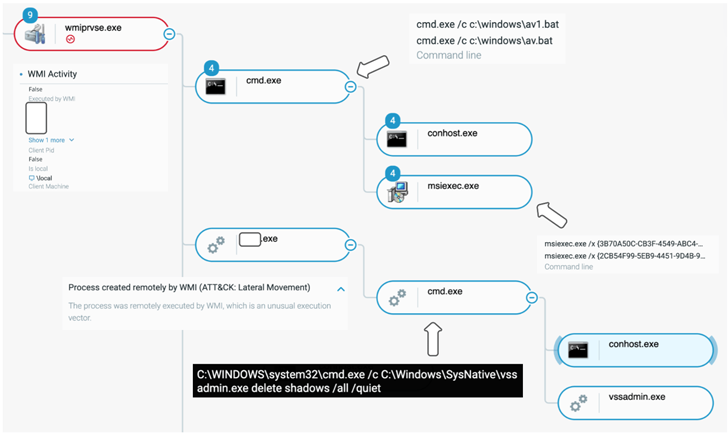
Corporations based mostly within the U.S. have been on the receiving finish of an “aggressive” Qakbot malware marketing campaign that results in Black Basta ransomware infections on compromised networks.
“On this newest marketing campaign, the Black Basta ransomware gang is utilizing QakBot malware to create an preliminary level of entry and transfer laterally inside a corporation’s community,” Cybereason researchers Joakim Kandefelt and Danielle Frankel mentioned in a report shared with The Hacker Information.
Black Basta, which emerged in April 2022, follows the tried-and-tested strategy of double extortion to steal delicate information from focused firms and use it as leverage to extort cryptocurrency funds by threatening to launch the stolen info.
This isn’t the primary time the ransomware crew has been noticed utilizing Qakbot (aka QBot, QuackBot, or Pinkslipbot). Final month, Pattern Micro disclosed related assaults that entailed using Qakbot to ship the Brute Ratel C4 framework, which, in flip, was leveraged to drop Cobalt Strike.
The intrusion exercise noticed by Cybereason cuts out Brute Ratel C4 from the equation, as a substitute utilizing Qakbot to instantly distribute Cobalt Strike on a number of machines within the contaminated atmosphere.
The assault chain commences with a spear-phishing e mail bearing a malicious disk picture file that, when opened, kickstarts the execution of Qbot, which, for its half, connects to a distant server to retrieve the Cobalt Strike payload.
At this stage, credential harvesting and lateral motion actions are carried out to position the crimson staff framework on a number of servers, earlier than breaching as many endpoints as potential utilizing the collected passwords and launching the Black Basta ransomware.
“The menace actor obtained area administrator privileges in lower than two hours and moved to ransomware deployment in lower than 12 hours,” the researchers famous, including over 10 totally different clients have been impacted by the contemporary set of assaults previously two weeks.
In two situations noticed by the Israeli cybersecurity firm, the intrusions not solely deployed the ransomware but additionally locked the victims out of their networks by disabling the DNS service in a bid to make a restoration tougher.
Black Basta stays a extremely lively ransomware actor. In accordance with information gathered by Malwarebytes, Black Basta efficiently focused 25 firms in October 2022 alone, placing it behind LockBit, Karakurt, and BlackCat.