The cyber espionage group generally known as Bahamut has been attributed as behind a extremely focused marketing campaign that infects customers of Android gadgets with malicious apps designed to extract delicate info.
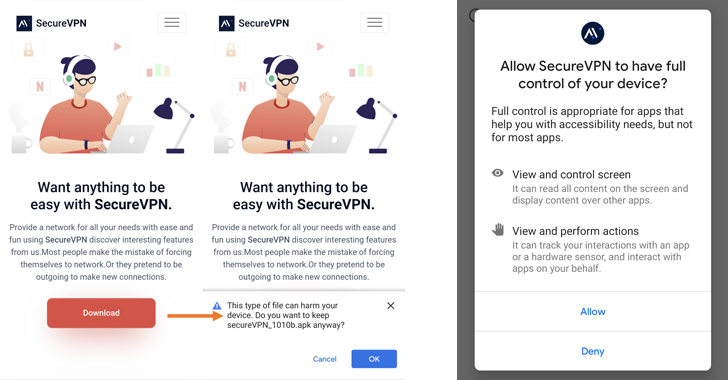
The exercise, which has been lively since January 2022, entails distributing rogue VPN apps via a pretend SecureVPN web site arrange for this function, Slovak cybersecurity agency ESET mentioned in a brand new report shared with The Hacker Information.
No less than eight completely different variants of the spyware and adware apps have been found to this point, with them being trojanized variations of authentic VPN apps like SoftVPN and OpenVPN.
The tampered apps and their updates are pushed to customers via the fraudulent web site. It is also suspected that the targets are rigorously chosen, since launching the app requires the sufferer to enter an activation key to allow the options.
This means the usage of an undetermined distribution vector, though previous proof reveals that it might take the type of spear-phishing emails, SMS messages, or direct messages on social media apps.
The activation key mechanism can be designed to speak with an actor-controlled server, successfully stopping the malware from being by chance triggered proper after launch on a non-targeted person system.
Bahamut was unmasked in 2017 by Bellingcat as a hack-for-hire operation concentrating on authorities officers, human rights teams, and different high-profile entities in South Asia and the Center East with malicious Android and iOS apps to spy on its victims.
“Maybe essentially the most distinctive facet of Bahamut’s tradecraft that BlackBerry found is the group’s use of authentic, painstakingly crafted web sites, functions and personas,” BlackBerry famous in October 2020.
Earlier this yr, Cyble detailed two units of phishing assaults orchestrated by the group to push counterfeit Android apps masquerading as chat functions.
The most recent wave follows an analogous trajectory, tricking customers into putting in seemingly innocuous VPN apps that may exfiltrate a large swathe of knowledge, together with information, contact lists, SMSes, cellphone name recordings, areas, and messages from WhatsApp, Fb Messenger, Sign, Viber, Telegram, and WeChat.
“The info exfiltration is completed through the keylogging performance of the malware, which misuses accessibility providers,” ESET researcher Lukáš Štefanko mentioned.
In an indication that the marketing campaign is nicely maintained, the risk actor initially packaged the malicious code throughout the SoftVPN utility, earlier than shifting to OpenVPN, a shift defined by the truth that the precise SoftVPN app stopped functioning and it was now not attainable to determine a VPN connection.
“The cell marketing campaign operated by the Bahamut APT group continues to be lively; it makes use of the identical technique of distributing its Android spyware and adware apps through web sites that impersonate or masquerade as authentic providers, as has been seen prior to now,” Štefanko added.