Entities in Armenia have come beneath a cyber assault utilizing an up to date model of a backdoor known as OxtaRAT that permits distant entry and desktop surveillance.
“The device capabilities embody looking for and exfiltrating recordsdata from the contaminated machine, recording the video from the net digicam and desktop, remotely controlling the compromised machine with TightVNC, putting in an online shell, performing port scanning, and extra,” Test Level Analysis stated in a report.
The newest marketing campaign is claimed to have commenced in November 2022 and marks the primary time the menace actors behind the exercise have expanded their focus past Azerbaijan.
“The menace actors behind these assaults have been concentrating on human rights organizations, dissidents, and unbiased media in Azerbaijan for a number of years,” the cybersecurity agency famous, calling the marketing campaign Operation Silent Watch.
The late 2022 intrusions are important, not least due to the adjustments within the an infection chain, the steps taken to enhance operational safety, and equip the backdoor with extra ammunition.
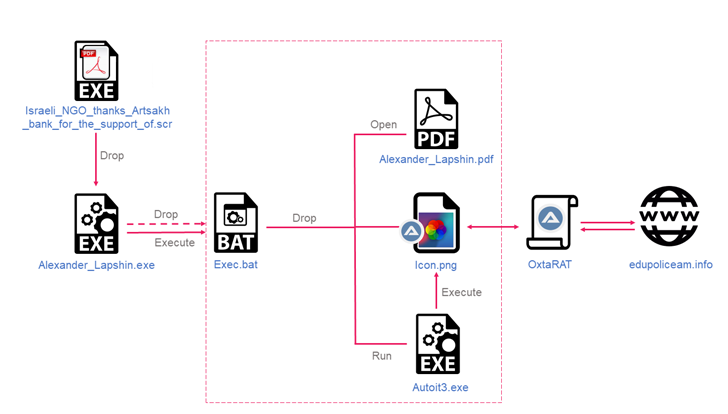
The start line of the assault sequence is a self-extracting archive that mimics a PDF file and bears a PDF icon. Launching the purported “doc” opens a decoy file whereas additionally stealthily executing malicious code hidden inside a picture.
A polyglot file that mixes compiled AutoIT script and a picture, OxtaRAT options instructions that allow the menace actor to run further instructions and recordsdata, harvest delicate info, carry out reconnaissance and surveillance through an online digicam, and even pivot to different.
OxtaRAT has been put to make use of by the adversary way back to June 2021, albeit with considerably lowered performance, indicating an try and consistently replace its toolset and trend it right into a Swiss Military knife malware.
The November 2022 assault additionally stands out for quite a few causes. The primary is that the .SCR recordsdata that activate the kill chain already comprise the OxtaRAT implant versus performing as a downloader to fetch the malware.
“This protects the actors from needing to make further requests for binaries to the C&C server and attracting pointless consideration, in addition to hides the principle malware from being simply found on the contaminated machine, because it seems like a daily picture and bypasses type-specific protections,” Test Level defined.
The second putting facet is the geofencing of command-and-control (C2) domains that host the auxiliary instruments to Armenian IP addresses.
Additionally of word is the flexibility of OxtaRAT to run instructions for port scanning and to check the pace of an web connection, that latter of which is probably going used as a method to cover the “intensive” information exfiltration.
“OxtaRAT, which beforehand had principally native recon and surveillance capabilities, can now be used as a pivot for lively reconnaissance of different units,” Test Level stated.
“This will point out that the menace actors are getting ready to increase their essential assault vector, which is at the moment social engineering, to infrastructure-based assaults. It additionally is likely to be an indication that the actors are transferring from concentrating on people to concentrating on extra advanced or company environments.”
“The underlying menace actors have been sustaining the event of Auto-IT primarily based malware for the final seven years, and are utilizing it in surveillance campaigns whose targets are in step with Azerbaijani pursuits.”