For six months, the notorious Emotet botnet has proven nearly no exercise, and now it is distributing malicious spam. Let’s dive into particulars and focus on all you might want to know in regards to the infamous malware to fight it.
Why is everybody frightened of Emotet?
Emotet is by far probably the most harmful trojans ever created. The malware turned a really damaging program because it grew in scale and class. The sufferer will be anybody from company to non-public customers uncovered to spam e mail campaigns.
The botnet distributes via phishing containing malicious Excel or Phrase paperwork. When customers open these paperwork and allow macros, the Emotet DLL downloads after which masses into reminiscence.
It searches for e mail addresses and steals them for spam campaigns. Furthermore, the botnet drops extra payloads, equivalent to Cobalt Strike or different assaults that result in ransomware.
The polymorphic nature of Emotet, together with the numerous modules it contains, makes the malware difficult to establish. The Emotet crew consistently adjustments its techniques, strategies, and procedures to make sure that the present detection guidelines can’t be utilized. As a part of its technique to remain invisible within the contaminated system, the malicious software program downloads additional payloads utilizing a number of steps.
And the outcomes of Emotet habits are devastating for cybersecurity specialists: the malware is sort of not possible to take away. It spreads rapidly, generates defective indicators, and adapts in response to attackers’ wants.
How has Emotet upgraded over time?
Emotet is a sophisticated and consistently altering modular botnet. The malware began its journey as a easy banking trojan in 2014. However since then, it has acquired a bunch of various options, modules, and campaigns:
- 2014. Cash switch, mail spam, DDoS, and tackle ebook stealing modules.
- 2015. Evasion performance.
- 2016. Mail spam, RIG 4.0 exploit equipment, supply of different trojans.
- 2017. A spreader and tackle ebook stealer module.
- 2021. XLS malicious templates, makes use of MSHTA, dropped by Cobalt Strike.
- 2022. Some options remained the identical, however this yr additionally introduced a number of updates.
This tendency proves that Emotet is not going anyplace regardless of frequent “holidays” and even the official shutdown. The malware evolves quick and adapts to every part.
What options has a brand new Emotet 2022 model acquired?
After nearly half a yr of a break, the Emotet botnet returned even stronger. Here’s what you might want to learn about a brand new 2022 model:
- It drops IcedID, a modular banking trojan.
- The malware masses XMRig, a miner that steals pockets information.
- The trojan has binary adjustments.
- Emotet bypasses detection utilizing a 64-bit code base.
- A brand new model makes use of new instructions:
Invoke rundll32.exe with a random named DLL and the export PluginInit
- Emotet’s objective is to get credentials from Google Chrome and different browsers.
- It is also focused to utilize the SMB protocol to gather firm information
- Like six months in the past, the botnet makes use of XLS malicious lures, however it adopted a brand new one this time:
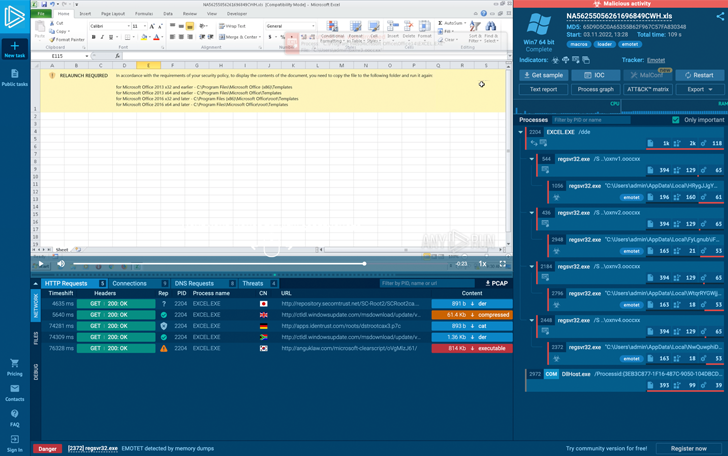 |
| The Emotet’s Excel lure |
How you can detect Emotet?
The primary Emotet problem is to detect it within the system rapidly and precisely. In addition to that, a malware analyst ought to perceive the botnet’s habits to stop future assaults and keep away from attainable losses.
With its lengthy story of improvement, Emotet stepped up within the anti-evasion technique. By the evolution of the method execution chain and malware exercise contained in the contaminated system adjustments, the malware has modified detection strategies drastically.
For instance, in 2018, it was attainable to detect this banker by wanting on the identify of the method – it was certainly one of these:
eventswrap, implrandom, turnedavatar, soundser, archivesymbol, wabmetagen, msrasteps, secmsi, crsdcard, narrowpurchase, smxsel, watchvsgd, mfidlisvc, searchatsd, lpiograd, noticesman, appxmware, sansidaho
Later, within the first quarter of 2020, Emotet began to create particular key into the registry – it writes into the important thing HKEY_CURRENT_USERSOFTWAREMICROSOFTWINDOWSCURRENTVERSIONEXPLORER worth with the size 8 symbols (letters and characters).
After all, Suricata guidelines at all times establish this malware, however detection methods typically proceed past the primary wave as a result of guidelines have to replace.
One other option to detect this banker was its malicious paperwork – crooks use particular templates and lures, even with grammatical errors in them. One of the crucial dependable methods to detect Emotet is by the YARA guidelines.
To beat malware’s anti-evasion strategies and seize the botnet – use a malware sandbox as probably the most handy software for this objective. In ANY.RUN, you can’t solely detect, monitor, and analyze malicious objects but additionally get already extracted configurations from the pattern.
There are some options that you simply use only for Emotet evaluation:
- reveal C2 hyperlinks of a malicious pattern with the FakeNet
- use Suricata and YARA rulesets to efficiently establish the botnet
- Get information about C2 servers, keys, and strings extracted from the pattern’s reminiscence dump
- collect recent malware’s IOCs
The software helps to carry out profitable investigations rapidly and exactly, so malware analysts can save helpful time.
ANY.RUN sandbox has ready unbelievable offers for Black Friday 2022! Now’s the most effective time to spice up your malware evaluation and avoid wasting cash! Take a look at particular provides for his or her premium plans however for a restricted time – from 22-29 November, 2022.
Emotet has not demonstrated full performance and constant follow-on payload supply. Use trendy instruments like ANY.RUN on-line malware sandbox to enhance your cybersecurity and detect this botnet successfully. Keep protected and good menace searching!




