ACM.120 Add multiple MFA machine to an AWS IAM account for various functions or in case of a misplaced machine
This can be a continuation of my sequence on Automating Cybersecurity Metrics.
I’m thrilled to see that we will now add a number of MFA gadgets to a consumer in AWS IAM. I’m stopping in the midst of one other weblog submit to attempt it out. AWS SSO already permits a number of keys however there are some things you may’t do with AWS SSO and should still wish to use AWS IAM in some circumstances as defined on this weblog sequence.
Why you may want a number of MFA keys in your AWS IAM account
I spoke about why this function is required on the AWS Atlanta Summit earlier this 12 months. Let’s say you utilize a Yubikey and you’ve got a loopy canine just like the one we simply received it could be operating round by your laptop and break your Yubikey. You need to use a backup machine to entry your account.
In truth, earlier this 12 months my husband was goofing round once I was engaged on my laptop and I virtually utterly destroyed a Yubikey. Fortunately it had two ends and the one which labored in my cell phone nonetheless labored so I might nonetheless get into a few of my accounts that used that key.
There’s additionally the chance that you may lose your key or it merely stops working. What about your root account? Maybe you may have two completely different keys saved in two separate locations in case one or different areas is affected by a catastrophe.
Separate MFA gadgets for automation and the AWS Console
I defined why I don’t use Yubikeys with the AWS CLI right here:
Though I don’t wish to set up the Yubikey CLI if I don’t need to on my major work machine, I do like utilizing a Yubikey finest to login to web sites.
It might be nice if I might use a Yubikey for the AWS Console (website online) however a digital MFA machine for automation. That’s what I’m going to check out.
Including a Yubikey to our IAM Consumer account
We used CloudFormation to deploy a consumer account.
I defined how you can use MFA with the AWS CLI on this submit with digital MFA:
On this submit we used CloudFormation to auto-generate a password to make use of with the AWS console.
We leverage the AWS Console to implement entry to a user-specific AWS Secrets and techniques Supervisor Secret utilizing MFA. As a result of I might solely add one MFA machine to our consumer I’ve been utilizing the digital MFA machine to log into the console and with automation.
Now I wish to know if I can use a separate machine for the AWS Console and automation.
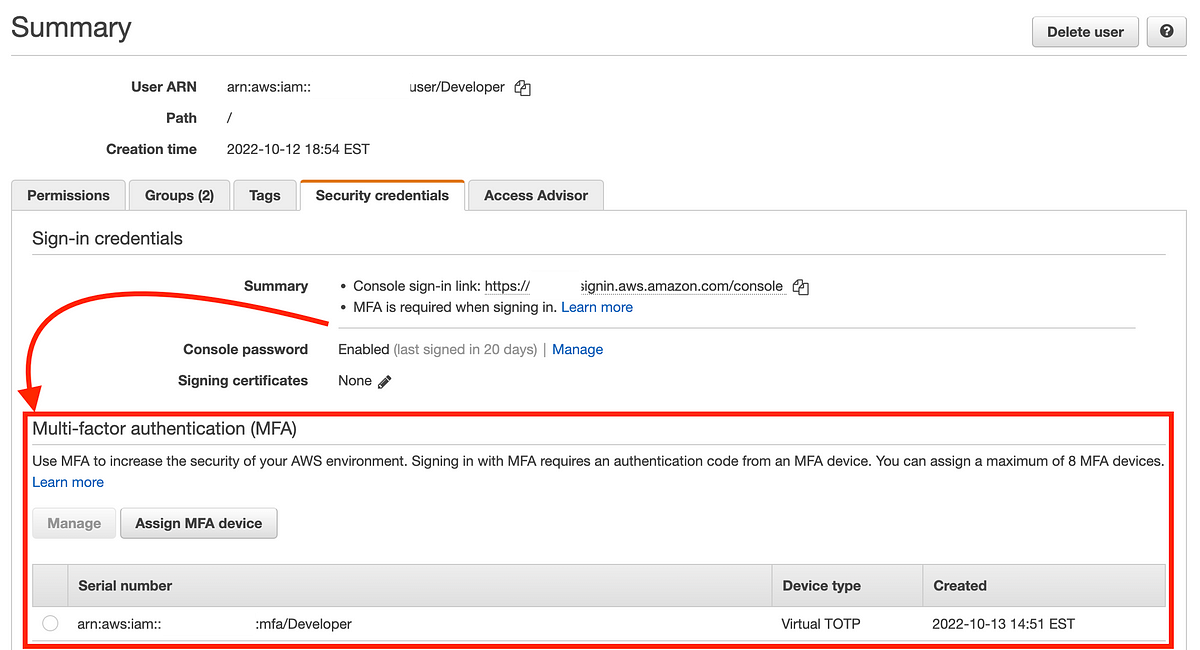
Including a second MFA machine within the AWS Console
Login to the AWS Console.
Click on on the consumer for whom you wish to add the second MFA machine.
Observe that the primary time I logged in and regarded on the display the place you
can edit MFA, I initially didn't see the brand new display. I might solely add
one machine. I added a brand new consumer and there I might see the brand new display.
Then I checked out a special consumer that had MFA assigned and there was no
MFA machine assigned! What? To not fear. Clicking round some extra, I
was capable of see the brand new MFA display and all the present MFA gadgets
have been current. It may very well be that AWS was rolling out updates or a caching
problem however simply click on round a bit and you need to be capable to see the display
under in case you do not at first for an present consumer.
MFA gadgets have moved to a listing below the consumer password part.
We have already got a digital MFA machine assigned.
Let’s see if we will add a {hardware} machine additionally. Click on “Assign MFA Gadget.”
Enter a Identify. Choose Safety key.
After coming into the pin for my machine and clicking the buttom I now have two several types of MFA gadgets related to the developer account.
In the event you recall from the submit on utilizing MFA with the CLI you specify a specific MFA machine to make use of with a profile. For our Developer consumer, we will specify the digital MFA machine as our MFA machine for automation.
Now you may take a look at logging into the AWS Console utilizing your new {hardware} MFA machine assigned to the Developer IAM consumer.
One factor I want to discover additional: the flexibility to restrict automation to a particular MFA machine and console entry to a different.
Observe for updates.
Teri Radichel
In the event you preferred this story please clap and observe:
******************************************************************
Medium: Teri Radichel or E mail Listing: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests companies by way of LinkedIn: Teri Radichel or IANS Analysis
******************************************************************
© 2nd Sight Lab 2022
All of the posts on this sequence:
____________________________________________
Writer:
Cybersecurity for Executives within the Age of Cloud on Amazon
Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration take a look at or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety courses, articles, white papers, displays, and podcasts