A beforehand undocumented Chinese language-speaking superior persistent risk (APT) actor dubbed Aoqin Dragon has been linked to a string of espionage-oriented assaults geared toward authorities, schooling, and telecom entities mainly in Southeast Asia and Australia relationship way back to 2013.
“Aoqin Dragon seeks preliminary entry primarily by doc exploits and using faux detachable gadgets,” SentinelOne researcher Joey Chen stated in a report shared with The Hacker Information. “Different methods the attacker has been noticed utilizing embrace DLL hijacking, Themida-packed recordsdata, and DNS tunneling to evade post-compromise detection.”
The group is claimed to have some stage of affiliation with one other risk actor generally known as Naikon (aka Override Panda), with campaigns primarily directed towards targets in Australia, Cambodia, Hong Kong, Singapore, and Vietnam.
Infections chains mounted by Aoqin Dragon have banked on Asia-Pacific political affairs and pornographic-themed doc lures in addition to USB shortcut methods to set off the deployment of considered one of two backdoors: Mongall and a modified model of the open-source Heyoka challenge.
This concerned leveraging outdated and unpatched safety vulnerabilities (CVE-2012-0158 and CVE-2010-3333), with the decoy paperwork attractive targets into opening the recordsdata. Through the years, the risk actor additionally employed executable droppers masquerading as antivirus software program to deploy the implant and connect with a distant server.
“Though executable recordsdata with faux file icons have been in use by quite a lot of actors, it stays an efficient instrument particularly for APT targets,” Chen defined. “Mixed with ‘fascinating’ e-mail content material and a catchy file title, customers might be socially engineered into clicking on the file.”
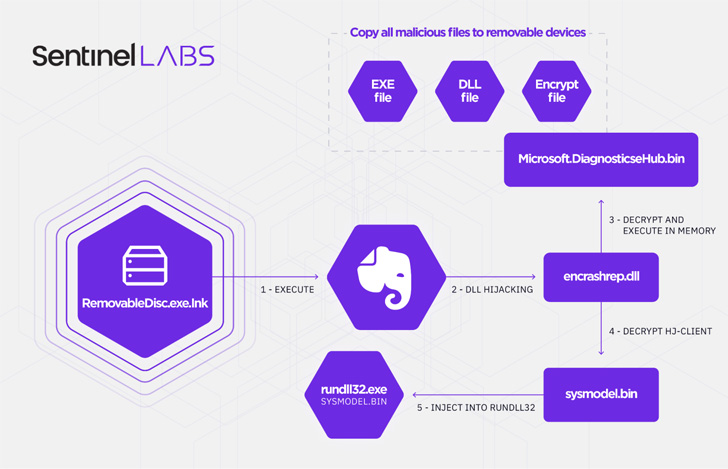
That stated, Aoqin Dragon’s latest preliminary entry vector of selection since 2018 has been its use of a faux detachable machine shortcut file (.LNK), which , when clicked, runs an executable (“RemovableDisc.exe”) that sports activities the icon for the favored note-taking app Evernote however is engineered to operate as a loader for 2 completely different payloads.
One of many elements within the an infection chain is a spreader that copies all malicious recordsdata to different detachable gadgets and the second module is an encrypted backdoor that injects itself into rundll32‘s reminiscence, a native Home windows course of used to load and run DLL recordsdata.
Identified to be used since not less than 2013, Mongall (“HJ-client.dll”) is described as a not-so “notably characteristic wealthy” implant however one which packs sufficient options to create a distant shell and add and obtain arbitrary recordsdata to and from the attacker-control server.
Additionally utilized by the adversary is a reworked variant of Heyoka (“srvdll.dll”), a proof-of-concept (PoC) exfiltration instrument “which makes use of spoofed DNS requests to create a bidirectional tunnel.” The modified Heyoka backdoor is extra highly effective, outfitted with capabilities to create, delete, and seek for recordsdata, create and terminate processes, and collect course of data on a compromised host.
“Aoqin Dragon is an lively cyber espionage group that has been working for practically a decade,” Chen stated, including, “it’s doubtless they may also proceed to advance their tradecraft, discovering new strategies of evading detection and keep longer of their goal community.”