Cybersecurity researchers are calling consideration to a zero-day flaw in Microsoft Workplace that could possibly be abused to attain arbitrary code execution on affected Home windows techniques.
The vulnerability got here to mild after an unbiased cybersecurity analysis crew generally known as nao_sec uncovered a Phrase doc (“05-2022-0438.doc“) that was uploaded to VirusTotal from an IP tackle in Belarus.
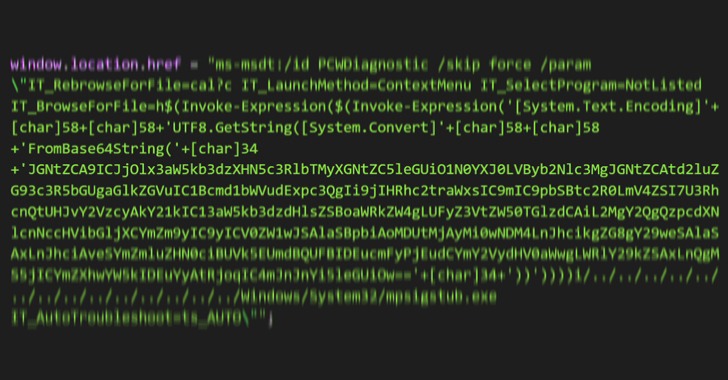
“It makes use of Phrase’s exterior hyperlink to load the HTML after which makes use of the ‘ms-msdt’ scheme to execute PowerShell code,” the researchers famous in a collection of tweets final week.
In accordance with safety researcher Kevin Beaumont, who dubbed the flaw “Follina,” the maldoc leverages Phrase’s distant template function to fetch an HTML file from a server, which then makes use of the “ms-msdt://” URI scheme to run the malicious payload.
The shortcoming has been so named as a result of the malicious pattern references 0438, which is the realm code of Follina, a municipality within the Italian metropolis of Treviso.
MSDT is brief for Microsoft Help Diagnostics Device, a utility that is used to troubleshoot and accumulate diagnostic knowledge for evaluation by help professionals to resolve an issue.
“There’s quite a bit happening right here, however the first drawback is Microsoft Phrase is executing the code by way of msdt (a help device) even when macros are disabled,” Beaumont defined.
“Protected View does kick in, though in case you change the doc to RTF type, it runs with out even opening the doc (by way of the preview tab in Explorer) not to mention Protected View,” the researcher added.
A number of Microsoft Workplace variations, together with Workplace, Workplace 2016, and Workplace 2021, are mentioned to be affected, though different variations are anticipated to be susceptible as properly.
What’s extra, Richard Warren of NCC Group managed to show an exploit on Workplace Skilled Professional with April 2022 patches operating on an up-to-date Home windows 11 machine with the preview pane enabled.
“Microsoft are going to want to patch it throughout all of the completely different product choices, and safety distributors will want sturdy detection and blocking,” Beaumont mentioned. We’ve got reached out to Microsoft for remark, and we’ll replace the story as soon as we hear again.