1000’s of Citrix Software Supply Controller (ADC) and Gateway endpoints stay weak to 2 vital safety flaws disclosed by the corporate over the previous few months.
The problems in query are CVE-2022-27510 and CVE-2022-27518 (CVSS scores: 9.8), which had been addressed by the virtualization companies supplier on November 8 and December 13, 2022, respectively.
Whereas CVE-2022-27510 pertains to an authentication bypass that could possibly be exploited to realize unauthorized entry to Gateway consumer capabilities, CVE-2022-27518 considerations a distant code execution bug that might allow the takeover of affected techniques.
Citrix and the U.S. Nationwide Safety Company (NSA), earlier this month, warned that CVE-2022-27518 is being actively exploited within the wild by menace actors, together with the China-linked APT5 state-sponsored group.
Now, based on a new evaluation from NCC Group’s Fox-IT analysis crew, hundreds of internet-facing Citrix servers are nonetheless unpatched, making them a beautiful goal for hacking crews.
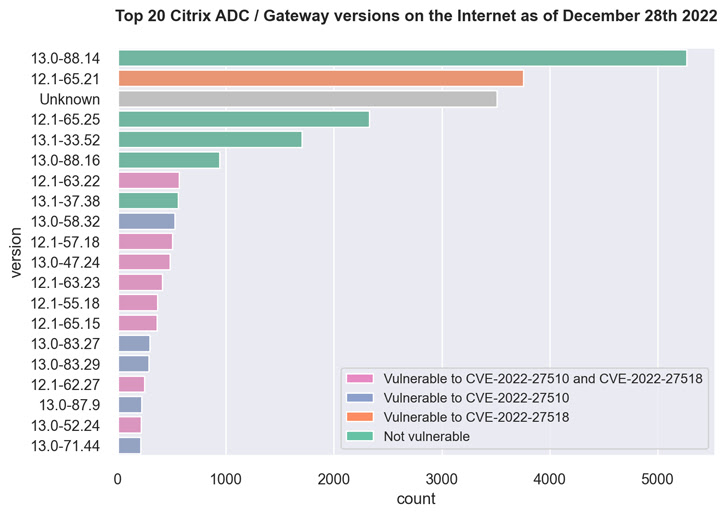
This contains over 3,500 Citrix ADC and Gateway servers working model 12.1-65.21 which can be prone to CVE-2022-27518, in addition to greater than 500 servers working 12.1-63.22 which can be weak to each flaws.
A majority of the servers, amounting to at least 5,000, are working 13.0-88.14, a model that is resistant to CVE-2022-27510 and CVE-2022-27518.
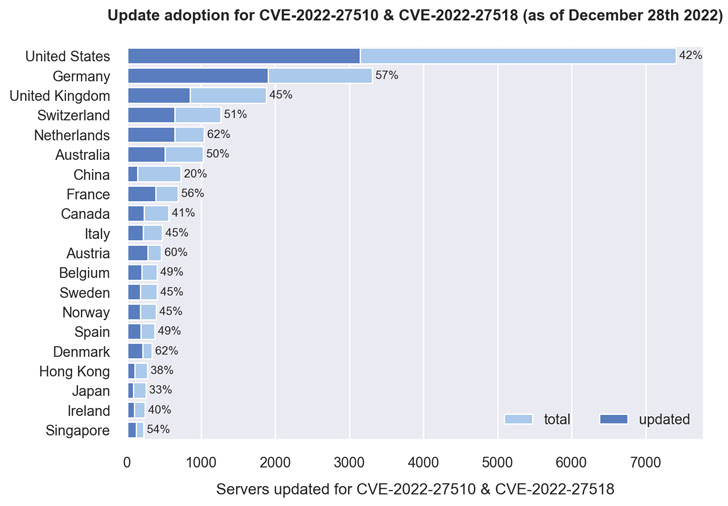
A rustic-wise breakdown reveals that greater than 40% of servers situated in Denmark, the Netherlands, Austria, Germany, France, Singapore, Australia, the U.Ok., and the U.S. have been up to date, with China faring the worst, the place solely 20% of practically 550 servers have been patched.
Fox-IT stated it was capable of deduce the model info from an MD5-like hash worth current within the HTTP response of login URL (i.e., “ns_gui/vpn/index.html”) and mapping it to their respective variations.