The menace actors behind the CatB ransomware operation have been noticed utilizing a way referred to as DLL search order hijacking to evade detection and launch the payload.
CatB, additionally known as CatB99 and Baxtoy, emerged late final yr and is alleged to be an “evolution or direct rebrand” of one other ransomware pressure often known as Pandora primarily based on code-level similarities.
It is price noting that the usage of Pandora has been attributed to Bronze Starlight (aka DEV-0401 or Emperor Dragonfly), a China-based menace actor that is recognized to make use of short-lived ransomware households as a ruse to seemingly conceal its true targets.
One of many key defining traits of CatB is its reliance on DLL hijacking through a legit service referred to as Microsoft Distributed Transaction Coordinator (MSDTC) to extract and launch the ransomware payload.
“Upon execution, CatB payloads depend on DLL search order hijacking to drop and cargo the malicious payload,” SentinelOne researcher Jim Walter mentioned in a report revealed final week. “The dropper (variations.dll) drops the payload (oci.dll) into the System32 listing.”
The dropper can be liable for finishing up anti-analysis checks to find out if the malware is being executed inside a digital setting, and in the end abusing the MSDTC service to inject the rogue oci.dll containing the ransomware into the msdtc.exe executable upon system restart.
“The [MSDTC] configurations modified are the title of the account below which the service ought to run, which is modified from Community Service to Native System, and the service begin choice, which is modified from Demand begin to Auto begin for persistency if a restart happens,” Minerva Labs researcher Natalie Zargarov defined in a earlier evaluation.
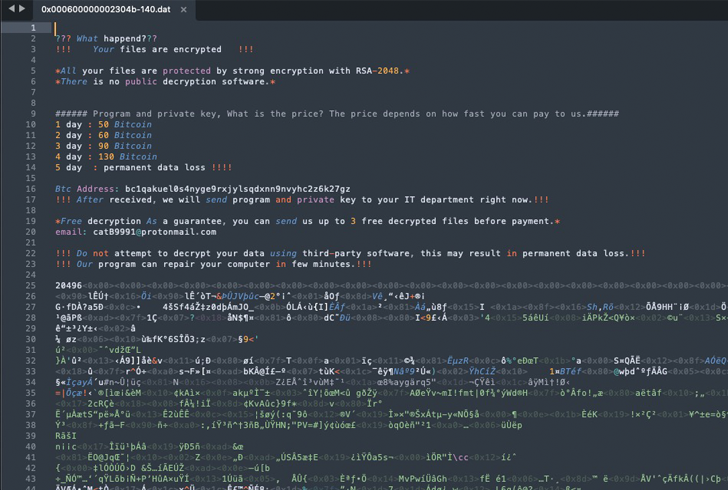
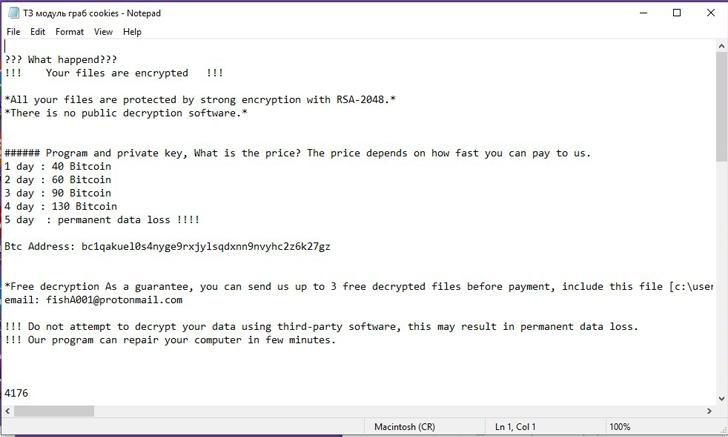
One placing facet of the ransomware is its absence of a ransom be aware. As a substitute, every encrypted file is up to date with a message urging the victims to make a Bitcoin fee.
Uncover the Hidden Risks of Third-Get together SaaS Apps
Are you conscious of the dangers related to third-party app entry to your organization’s SaaS apps? Be part of our webinar to be taught in regards to the sorts of permissions being granted and how you can reduce threat.
One other trait is the malware’s potential to reap delicate knowledge equivalent to passwords, bookmarks, historical past from net browsers Google Chrome, Microsoft Edge (and Web Explorer), and Mozilla Firefox.
“CatB joins an extended line of ransomware households that embrace semi-novel methods and atypical behaviors equivalent to appending notes to the pinnacle of recordsdata,” Walter mentioned. “These behaviors look like carried out within the curiosity of detection evasion and a few stage of anti-analysis trickery.”
This isn’t the primary time the MSDTC service has been weaponized for malicious functions. In Could 2021, Trustwave disclosed a novel malware dubbed Pingback that leveraged the identical approach to attain persistence and bypass safety options.