Probably the most superior cyberattackers attempt to seem like your directors, abusing authentic credentials, utilizing authentic system binaries or instruments which might be natively utilized within the sufferer’s setting. These “living-off-the-land’ (LotL) cyberattacks proceed to trigger complications for safety groups, which regularly don’t have any efficient technique of differentiating between malicious conduct and legit administrative conduct.
When an attacker makes use of functions and providers native to your setting, your individual workers additionally use these programs, and a signature- or rules-based detection system will both miss the exercise or find yourself alerting or disrupting your individual staff’ actions.
It’s no shock then that these assaults have been discovered to be extremely efficient, with the Ponemon Institute discovering that fileless malware assaults are about 10 instances extra more likely to succeed than file-based assaults.
LotL cyberattackers depend on quite a lot of instruments and strategies, together with:
- Utilizing PowerShell to launch malicious scripts, escalate privileges, set up backdoors, create new duties on distant machines, determine configuration settings, evade defences, exfiltrate knowledge, entry Energetic Listing info, and extra
- Utilizing Home windows Command Processor (CMD.exe), to run batch scripts, and (WScript.exe) and Console Primarily based Script Host (CScript.exe) to execute Visible Fundamental scripts, providing them extra automation.
- .NET functions for useful resource set up through the .NET Framework. Installutil.exe permits attackers to execute untrusted code through the trusted program
- Utilizing the Registry Console Software (reg.exe) to take care of persistence, retailer settings for malware, and retailer executables in subkeys.
- And lots of others, together with WMI (Home windows Administration Instrumentation), Service Management Supervisor Configuration Software (sc.exe), Scheduled Duties (AT.EXE Course of), and Sysinternals resembling PSExec.
LotL strategies involving Distant Desktop Protocol (RDP) connections might be a few of the most troublesome actions to triage for safety groups, as RDP typically represents a essential service for system directors. For safety groups, it may be exceptionally troublesome to parse by means of and determine which RDP connections are authentic and which aren’t, particularly when administrative credentials are concerned.
Defensive programs targeted on “identified bads” and historic assault knowledge fail to catch the malicious use of a few of the instruments described above. Stopping these assaults requires a business-centric defensive technique that makes use of AI to grasp “regular” conduct of each consumer and system in your group to detect anomalous exercise in actual time.
Take, for instance, this real-world assault that focused a Darktrace buyer in July 2022.
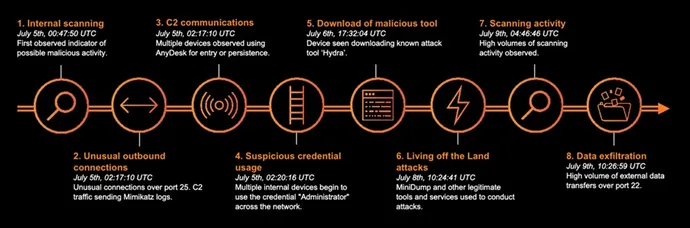
The primary signal of a compromise was noticed when Darktrace’s AI revealed an inner workstation and area controller (DC) partaking in uncommon scanning exercise, earlier than the DC made an outbound connection to a suspicious endpoint that was extremely uncommon for the setting. The contents of this connection revealed that the risk actor was exporting passwords from a profitable cracking try through Mimikatz — a presence that beforehand had been unknown to the safety staff.
A number of gadgets then started initiating outbound connections to AnyDesk-related web sites, a attainable technique of persistence or a backdoor for the attacker. Of their first demonstration of LotL strategies, the attacker initiated a “golden ticket assault” culminating in new admin logins. With their new place of privilege, use of the automating “ITaskSchedulerService” and Hydra brute-force device the subsequent day allowed for even deeper insights and enumeration of the shopper’s setting.
One system even remotely induced a living-off-the-land binary (LOLBin) assault. By creating and operating a brand new service on three totally different locations, the attacker retrieved MiniDump reminiscence contents and feed any info of curiosity again by means of Mimikatz. Not solely can this technique be used to determine additional passwords, but it surely permits for lateral motion through code executions and new file operations resembling downloading or transferring.
On the ultimate day, a brand new DC was seen partaking in an uncommonly excessive quantity of outbound calls to the DCE-RPC operations “samr” and “srvsvc” (each of that are authentic WMI providers). Later, the DC answerable for the preliminary compromise started partaking in outbound SSH connections to a uncommon endpoint and importing important volumes of knowledge over a number of connections.
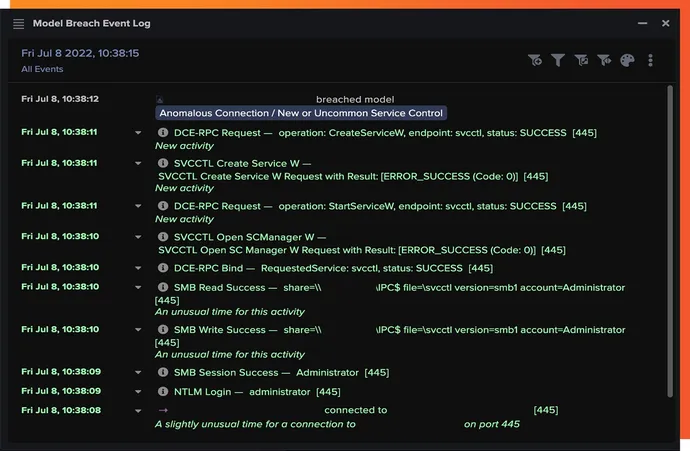
The attacker’s use of authentic and broadly used instruments all through this assault meant the assault flew underneath the radar of the remainder of the safety groups’ stack, however Darktrace’s AI stitched collectively a number of anomalies indicative of an assault and revealed the total scope of the incident to the safety staff, with each stage of the assault outlined.
This expertise can go additional than simply risk detection. Its understanding of what is “regular” for the enterprise permits it to provoke a focused response, containing solely the malicious exercise. On this case, this autonomous response performance was not configured, however the buyer turned it on quickly after. Even so, the safety staff was in a position to make use of the data gathered by Darktrace to comprise the assault and forestall any additional knowledge exfiltration or mission success.
LotL assaults are proving profitable for attackers and are unlikely to go away consequently. Because of this, safety groups are more and more transferring away from “legacy” defenses and towards AI that understands “‘regular” for everybody and all the things within the enterprise to shine a light-weight on the refined anomalies that comprise a cyberattack — even when that assault depends totally on authentic instruments.
Concerning the Writer

Tony Jarvis is Director of Enterprise Safety, Asia-Pacific and Japan, at Darktrace. Tony is a seasoned cybersecurity strategist who has suggested Fortune 500 firms all over the world on finest apply for managing cyber-risk. He has endorsed governments, main banks, and multinational firms, and his feedback on cybersecurity and the rising risk to essential nationwide infrastructure have been reported in native and worldwide media together with CNBC, Channel Information Asia, and The Straits Occasions. Tony holds a BA in Info Techniques from the College of Melbourne.


