One other technique to watch the watchers and perceive potential provide chain assaults
This publish is a part of a sequence on an journey to attach a PFSense firewall and a Ubiquiti Dream Machine Professional. See the underside of the publish for all of the posts on this sequence.
I discussed within the earlier publish on first impressions utilizing a Ubiquiti UDM Professional, that I obtained to the situation setting and the web page simply spun, and nothing ever confirmed up. I speculated it was as a result of the UI was attempting to succeed in out to some third-party area that was not allowed by my firewall configuration, which is particularly set as much as solely enable the UDM Professional to succeed in out to domains I’ve added within the configuration.
I defined how I reverse-engineered what domains the gadget contacts in a previous publish. I additionally defined how I arrange an alias in PFSense to solely enable the domains I had particularly investigated and allowed. Apparently, the situation web page reaches out to one thing apart from what I had already allowed so it’s simply spinning and what I presume ought to be a map by no means reveals up.
I might have decided which area the UI was utilizing the identical means I did in my final publish. I additionally might have seemed on the browser growth instruments settings to see what area was failing.
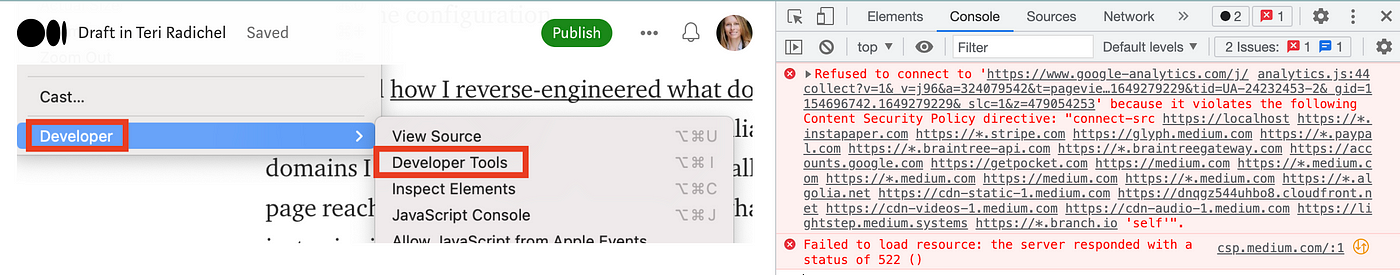
From there click on on Console and you may see what’s getting blocked. On this explicit case, it seems that Medium is obstructing a website it’s attempting to load in its content material safety coverage (Google Analytics). There’s additionally a failure to load one other URL on csp.medium.com with a 522 HTTP error. I’m not blocking both of these issues. It appears to be like Medium has a number of misconfigurations they may wish to look into. Nonetheless, if I used to be blocking one thing, it could additionally present up right here with a failure to attach.
These mechanisms will detect after the very fact when a website identify is blocked. They received’t block an sudden area identify or permit you to assessment and permit or disallow it as a web page opens or a connection is made. It might be fairly annoying to examine each connection however if you’re a safety researcher geek like me that’s simply one thing you love to do. I prefer to see what’s connecting to what.
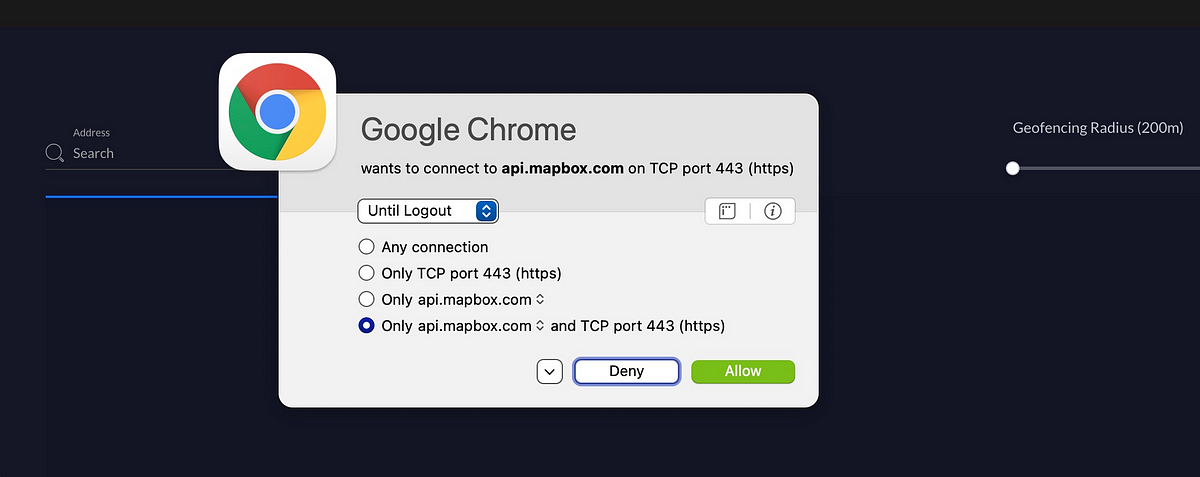
A technique to ensure your network-based firewall is working is to run a host-based firewall on prime of that. A number-based firewall will permit you to examine connections your machine makes. I used to be working my host-based firewall when the places web page on the Ubiquiti Dream Machine Professional did not load, and this connection popped up. Now I do know that the UI is attempting to get to api.mapbox.com. Even when I allowed this API connection right here on my host, the connection would later be blocked when it reaches the PFSense.
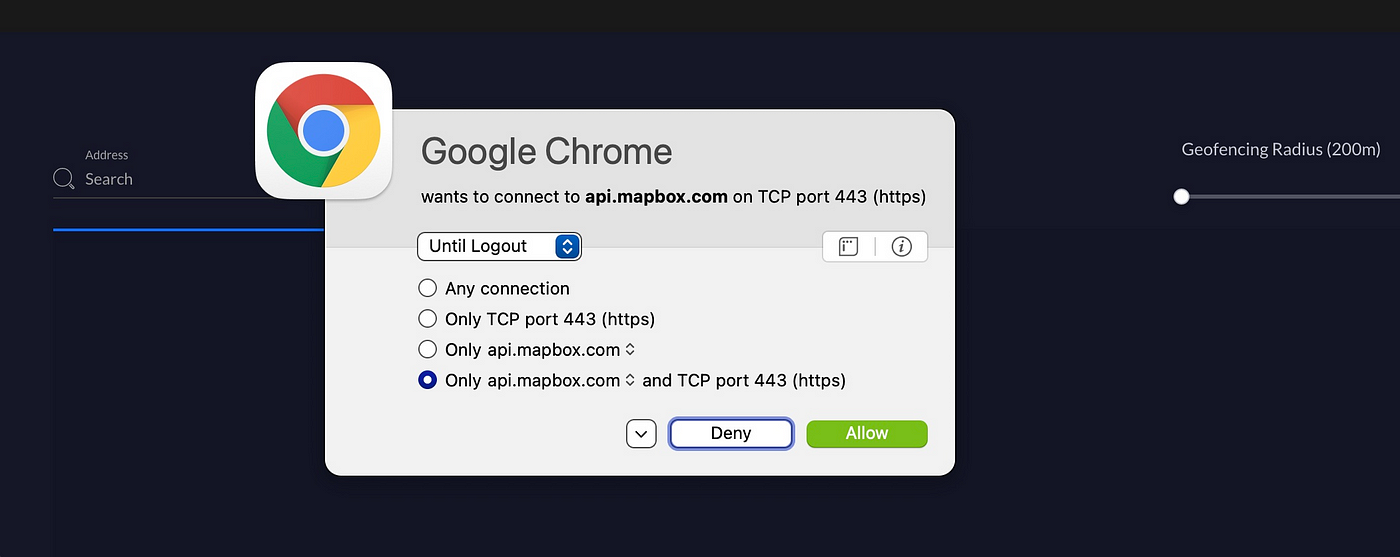
As I discussed in my final publish, all connections are allowed by default within the Ubiquiti gadget, in order that wouldn’t have blocked something. I haven’t tried out the firewall to see if and the way that will behave with regard to connections required for the UI to operate correctly.
In case you are utilizing a MAC OS, you may Little Snitch to observe your community connections.
In case you are working a Home windows machine, you should utilize Home windows Defender Firewall.
In case you are on Linux, use IP Tables.
I might want to analysis this API a bit extra and a few others I’ve discovered whereas utilizing the product. Nonetheless, as I discussed, dynamically together with third-party code in a manufacturing setting may be harmful. I defined on this publish how together with parts and code by yourself methods every time doable is safer on this weblog publish and why.
Now, not solely do that you must fear a few safety drawback at Ubiquiti, you’ll have to observe for safety issues at Mapbox. That is named a provide chain assault, the place a third-party part used to construct a product has a safety drawback. One thing to pay attention to every time you’re utilizing code and merchandise and particularly community home equipment.
Teri Radichel — Comply with me @teriradichel
© 2nd Sight Lab 2022
P.S. Should you learn my final publish, I discovered the place the configuration for assigning VLANs to ports exists within the UI and added it, if you’re curious. I additionally suppose I fastened my VLAN drawback however want to research it a bit additional to ensure it doesn’t have a safety drawback. I’ve a query out to Ubiquiti assist, however the remainder of the configuration ought to be coming quickly.
Extra on this sequence on the safety of community safety home equipment and community linked units:
To be continued…
____________________________________________

Wish to be taught extra about Cybersecurity and Cloud Safety? Try: Cybersecurity for Executives within the Age of Cloud on Amazon
Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Sources by Teri Radichel: Cybersecurity and Cloud safety courses, articles, white papers, shows, and podcasts