Authorities entities and enormous organizations have been focused by an unknown risk actor by exploiting a safety flaw in Fortinet FortiOS software program to end in knowledge loss and OS and file corruption.
“The complexity of the exploit suggests a sophisticated actor and that it’s extremely focused at governmental or government-related targets,” Fortinet researchers Guillaume Lovet and Alex Kong stated in an advisory final week.
The zero-day flaw in query is CVE-2022-41328 (CVSS rating: 6.5), a medium safety path traversal bug in FortiOS that would result in arbitrary code execution.
“An improper limitation of a pathname to a restricted listing vulnerability (‘path traversal’) [CWE-22] in FortiOS might permit a privileged attacker to learn and write arbitrary information by way of crafted CLI instructions,” the corporate famous.
The shortcoming impacts FortiOS variations 6.0, 6.2, 6.4.0 via 6.4.11, 7.0.0 via 7.0.9, and seven.2.0 via 7.2.3. Fixes can be found in variations 6.4.12, 7.0.10, and seven.2.4 respectively.
The disclosure comes days after Fortinet launched patches to handle 15 safety flaws, together with CVE-2022-41328 and a vital heap-based buffer underflow difficulty impacting FortiOS and FortiProxy (CVE-2023-25610, CVSS rating: 9.3).
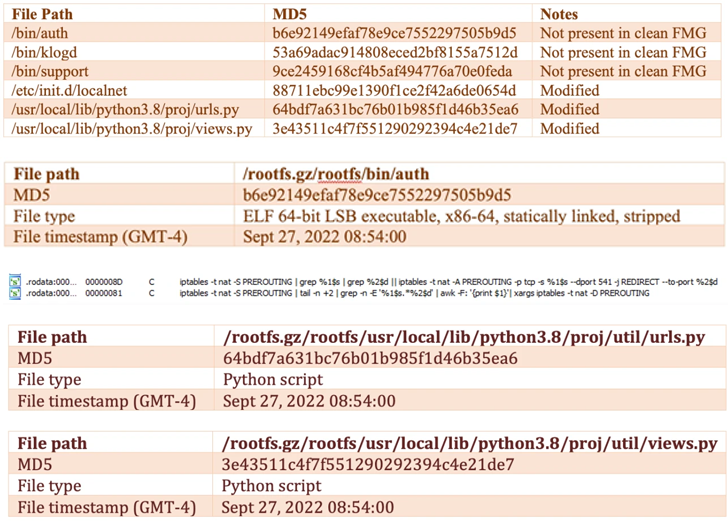
In accordance with the Sunnyvale-based firm, a number of FortiGate gadgets belonging to an unnamed buyer suffered from a “sudden system halt and subsequent boot failure,” indicating an integrity breach.
Additional evaluation of the incident revealed that the risk actors modified the gadget’s firmware picture to incorporate a brand new payload (“/bin/fgfm”) such that it is all the time launched earlier than the booting course of started.
The /bin/fgfm malware is designed to ascertain contact with a distant server to obtain information, exfiltrate knowledge from the compromised host, and grant distant shell entry.
Extra modifications launched to the firmware are stated to have offered the attacker with persistent entry and management, to not point out even disable firmware verification at startup.
Uncover the Hidden Risks of Third-Celebration SaaS Apps
Are you conscious of the dangers related to third-party app entry to your organization’s SaaS apps? Be part of our webinar to be taught concerning the sorts of permissions being granted and find out how to reduce threat.
Fortinet stated the assault was extremely focused, with proof pointing to governmental or government-affiliated organizations.
Given the complexity of the exploit, it is suspected that the attacker has a “deep understanding of FortiOS and the underlying {hardware}” and possesses superior capabilities to reverse engineer completely different features of the FortiOS working system.
It isn’t instantly clear if the risk actor has any connections to a different intrusion set that was noticed weaponizing a flaw in FortiOS SSL-VPN (CVE-2022-42475) earlier this January to deploy a Linux implant.