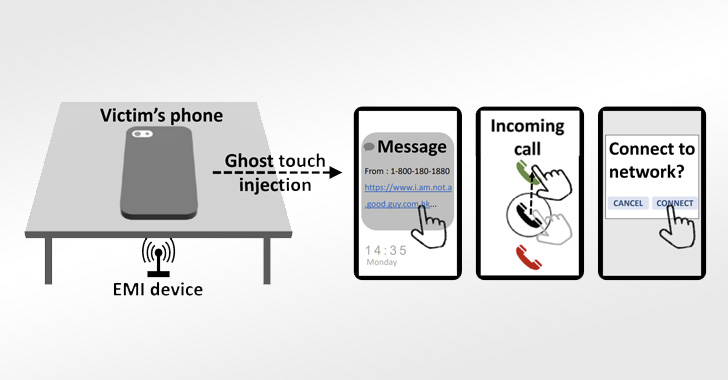
Researchers have demonstrated what they name the “first energetic contactless assault in opposition to capacitive touchscreens.”
GhostTouch, because it’s referred to as, “makes use of electromagnetic interference (EMI) to inject faux contact factors right into a touchscreen with out the necessity to bodily contact it,” a gaggle of lecturers from Zhejiang College and Technical College of Darmstadt mentioned in a brand new analysis paper.
The core concept is to reap the benefits of the electromagnetic indicators to execute fundamental contact occasions similar to faucets and swipes into focused places of the touchscreen with the objective of taking up distant management and manipulating the underlying gadget.
The assault, which works from a distance of as much as 40mm, hinges on the truth that capacitive touchscreens are delicate to EMI, leveraging it to inject electromagnetic indicators into clear electrodes which are constructed into the touchscreen in order to register them as contact occasions.
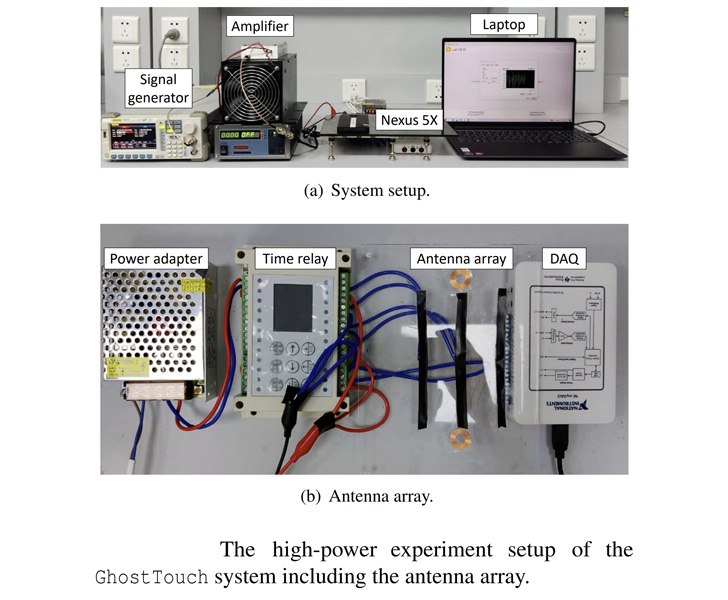
The experimental setup includes an electrostatic gun to generate a robust pulse sign that is then despatched to an antenna to transmit an electromagnetic subject to the telephone’s touchscreen, thereby inflicting the electrodes — which act as antennas themselves — to choose up the EMI.
This may be additional fine-tuned by tweaking the sign and the antenna to induce a wide range of contact behaviors, similar to press and maintain and swipe to pick, relying on the gadget mannequin focused.
In a real-world situation, this might play out in numerous methods, together with swiping as much as unlock a telephone, connecting to a rogue Wi-Fi community, stealthily clicking on a malicious hyperlink containing malware, and even answering a telephone name on the sufferer’s behalf.
“In locations like a restaurant, library, assembly room, or convention lobbies, folks may place their smartphone face-down on the desk,” the researchers mentioned. “An attacker could embed the assault gear below the desk and launch assaults remotely.”
As many as 9 totally different smartphone fashions have been discovered susceptible to GhostTouch, together with Galaxy A10s, Huawei P30 Lite, Honor View 10, Galaxy S20 FE 5G, Nexus 5X, Redmi Notice 9S, Nokia 7.2, Redmi 8, and an iPhone SE (2020), the latter of which was used to determine a malicious Bluetooth connection.
To counteract the menace, the researchers advocate including electromagnetic shielding to dam EMI, bettering the detection algorithm of the touchscreen, and prompting customers to enter the telephone’s PIN or confirm their faces or fingerprints previous to executing high-risk actions.
“GhostTouch controls and shapes the near-field electromagnetic sign, and injects contact occasions into the focused space on the touchscreen, with out the necessity for bodily contact or entry to the sufferer’s gadget,” the researchers mentioned.