ACM.66 Why it’s best to use Subnet NACLs even in the event you already use safety teams and the right way to create them
It is a continuation of my collection of posts on Automating Cybersecurity Metrics.
Prior to now few posts we automated the creation of private and non-private VPCs, route tables and subnets. On this put up, we’ll apply community guidelines utilizing a Community Entry Management Record or ACL utilized to a subnet. Right here’s what we’re going to create:
Personal VPC NACL
We are able to assign one NACL to each subnets since they each share the identical ruleset.
Personal HTTP NACLOutbound: 80, 443 TCP, Any IP
Inbound: Ephemeral Ports, Any IP
Distant Entry NACL
Inbound: 22, 3389, Any IP
Outbound: Ephemeral ports, Any IP
Be aware that I’m permitting any IP within the NACL for now as a result of I might be extra particular within the safety group. I might change that for my private use and particularly prohibit the distant entry IP handle to my very own IP handle since I’m the one one accessing assets on this account, however I presume in a bigger group you will have many individuals who must log into assets remotely in a improvement setting. In that case it’s simpler to go away the NACL board and make the safety teams extra particular.
There’s nobody proper reply to how it’s best to deploy your networking, however the aim must be to scale back accessible paths for an attacker and the blast radius related to any single useful resource. I cowl these subjects in additional element in my guide on the finish of this put up.
Ephemeral Ports
I’ve seen lots of people make errors with community guidelines considering if they should open port 80 inbound additionally they must open port 80 outbound. That’s normally incorrect, but it surely will depend on which community protocol you’re utilizing.
For HTTP and HTTPS, you’d open TCP 80 and 443 inbound and ephemeral ports outbound.
For entry to a DNS server you’d usually open UDP and possibly TCP 53 outbound and ephemeral ports inbound.
Rule Processing in NACLs
The principles in a NACL are processed so as till a rule matches. You may create each ALLOW and DENY guidelines which you’ll be able to’t do in a safety group which provides you some extra flexibility and choices. I’m not going to get into that proper now however this flexibility would allow you to create a 3 tier community the place solely the net server community can entry the applying tier community and solely the applying tier community can entry the database tier community, for instance.
Why use NACLS when you have got Safety Teams?
I get this query on a regular basis.
- A NACL blocks entry between networks. A Safety Group applies guidelines to a particular host. Usually you need to block what you already know won’t ever be allowed so far as ports and protocols in a NACL. The safety teams are typically extra utility particular and nil belief.
- If you concentrate on the place a NACL is enforced versus the place safety group guidelines are enforced you’ll be able to visualize how shut you’re letting a identified dangerous IP handle get to your assets earlier than you cease them. I personally need to cease them as quickly as I can inside my safety structure. The online-facing NACL is the primary entry level.
- You may create broad guidelines that defend your total community with a NACL. This could prevent if somebody makes a mistake with a safety group rule.
- You may segregate duties between who can create safety group guidelines and NACL guidelines. I desire a community crew creates all the pieces however some organizations let builders create safety teams and the community crew creates the subnets and NACLs.
- NACLs have DENY capabilities that Safety Teams don’t which might help with sure community designs and assault eventualities.
- You might get higher efficiency in the event you block identified dangerous proper out the gate with a NACL moderately than letting it get to the purpose of your Safety Group. This logically is sensible to me however I haven’t examined it out. NACLs are stateless that means they don’t should spend time determining if the packet is related to an present session to permit or deny the visitors. They are going to drop packets rapidly. A stateful firewall wants to find out if packets are related to an present session, as a result of if some inbound visitors is related to a longtime outbound connection or vice versa, then the visitors is allowed. This requires extra processing on the a part of community units. By the way in which, Azure and GCP don’t have stateless firewall choices the final time I checked.
Pricing
Again within the day after I ran e-commerce web sites at a colocation facility I used to be charged for bandwidth. I created one thing like AJAX on the time to create a quote calculator consumer facet in JavaScript to scale back spherical journeys to the server for a marriage invitation website. You haven’t any thought what number of occasions an individual would resubmit that kind earlier than a marriage on an order that they had “saved for later.” This dramatically lowered the hits on the web site and it did decrease my bandwidth prices a bit.
You don’t get charged for NALCs or Safety Teams on AWS however you do pay for information transferred out of an EC2 occasion.
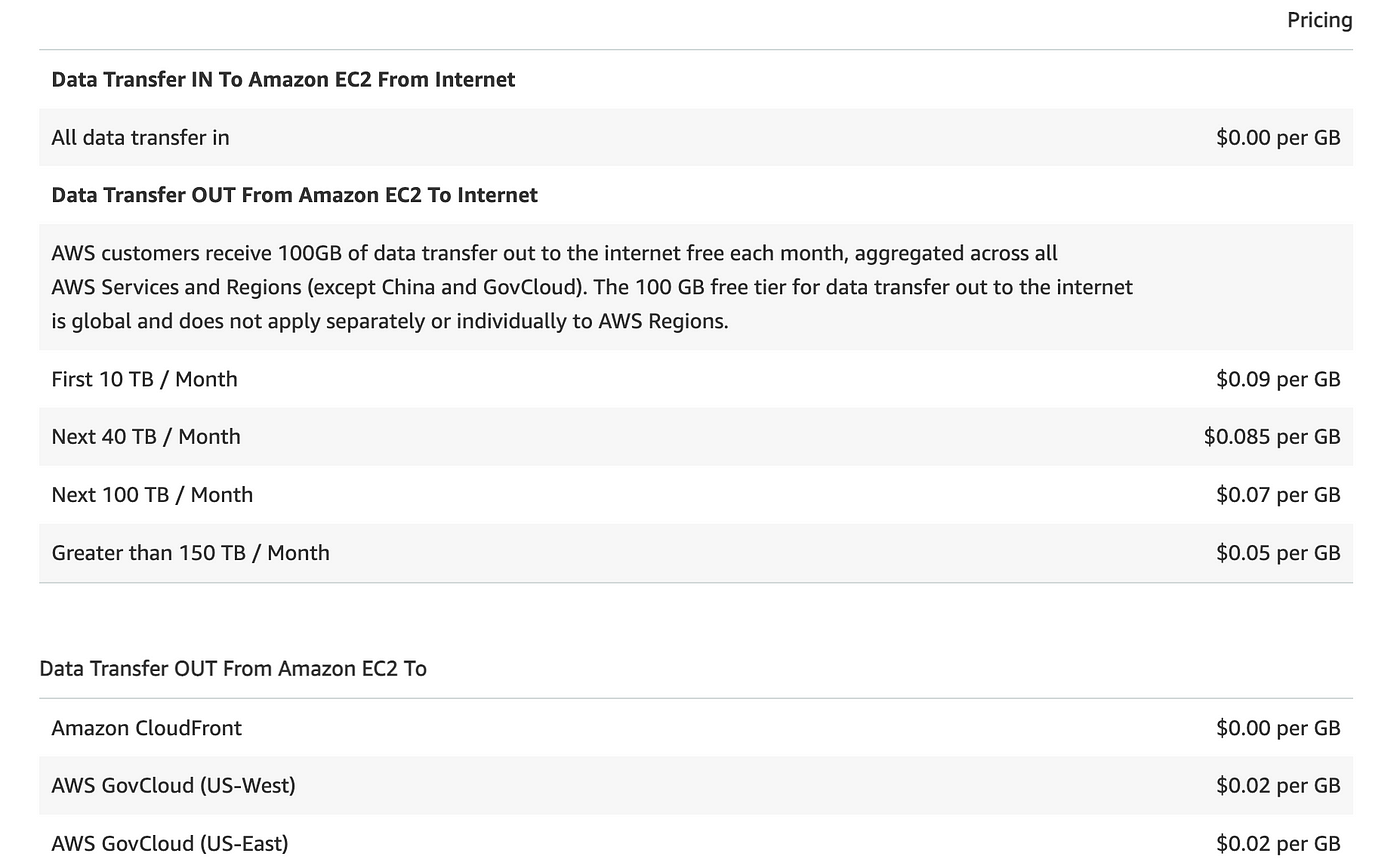
So what does “out” imply precisely. When it leaves the occasion community interface? Or when it hits the gateway? It could be fascinating to measure the influence of community guidelines blocking pointless outbound visitors to see if it makes a distinction in a big group. For instance, AWS used to make use of public NTP servers by default. How a lot visitors could be generated to NTP servers in a really giant group and what in the event you blocked that and switched to an inside NTP server? Undecided how a lot visitors NTP would generate however it could be fascinating to search out out.
Be aware that AWS doesn’t do this anymore. I’ve an upcoming put up on DNS and NTP that covers that in additional element.
DDOS prevention and Efficiency
What in the event you don’t use NACLs and let that visitors get all the way in which to your Safety Group earlier than you block it? How does that influence your efficiency? Do the hits in your Safety Group influence the useful resource it protects in any approach? I by no means sat down and examined this as I’m all the time too busy however I’ve been interested by this for a very long time. In case you take a look at it let me know. In my case, I block as a lot known-bad visitors on the NACL as I can fairly do with out overcomplicating my guidelines. I don’t have an enormous quantity of visitors in any case so the distinction is probably going negligible to me.
Nevertheless, I did write a put up about auto-blocking any dangerous visitors utilizing a firewall that had that functionality as soon as. I proposed that you possibly can cut back the influence of assaults and automatic scanners and enhance community efficiency by instantly dropping packets that has despatched invalid visitors prior to now. In fact you’d whitelist out identified good IP addresses and also you most likely wouldn’t apply this to an inside community, however moderately your Web-facing community entry.
Somebody who labored at that very same safety vendor as me attacked my put up publicly within the feedback (appears a bit obnoxious versus coming to my desk to debate the matter — don’t be that particular person), however clients of the seller got here to my protection within the feedback and stated they did, in truth, keep at bay DDOS assaults utilizing these strategies. The earlier you’ll be able to weed out known-bad visitors and with out evaluating the state of a session, the higher. NACLS are your first line of protection and as already talked about, stateless.
Attackers utilizing your endpoints to relay visitors
By the way in which, have you ever checked our load balancer logs currently for any endpoints instantly linked to the Web to see who’s relaying visitors off of them? Are you paying for that noisy visitors? Is it impacting your efficiency? Add community guidelines to dam the offenders and report them to your cloud supplier.
Limitations and Community Design
NACLs are restricted to twenty ingress an egress guidelines. Though you’ll be able to enhance these numbers to 40 each methods, AWS warns that would trigger a efficiency hit. Usually I exploit NACLs for broad primarily based guidelines moderately than particular hosts except there are some actually dangerous, repeat offenders that I need to block out of the gate.
For instance, I’d create a single net tier, app tier, and information tier in a VPC for micros-services that share the identical guidelines (abstraction as I wrote about earlier) after which service particular safety teams that create zero-trust guidelines for every service.
For our public VPC I’m going to permit 3389 and 22 in. Then I’m going to create a safety group that enables a particular IP handle to connect with a particular occasion on port 22 for Linux servers and one other safety group for port 3389 that can get utilized to Home windows servers. In case your builders should use a VPN to login it is possible for you to to create very particular guidelines and lock issues down additional — an idea individuals don’t normally consider after they use VPNs. I’d write about this extra in a later put up.
Creating NACLs with CloudFormation
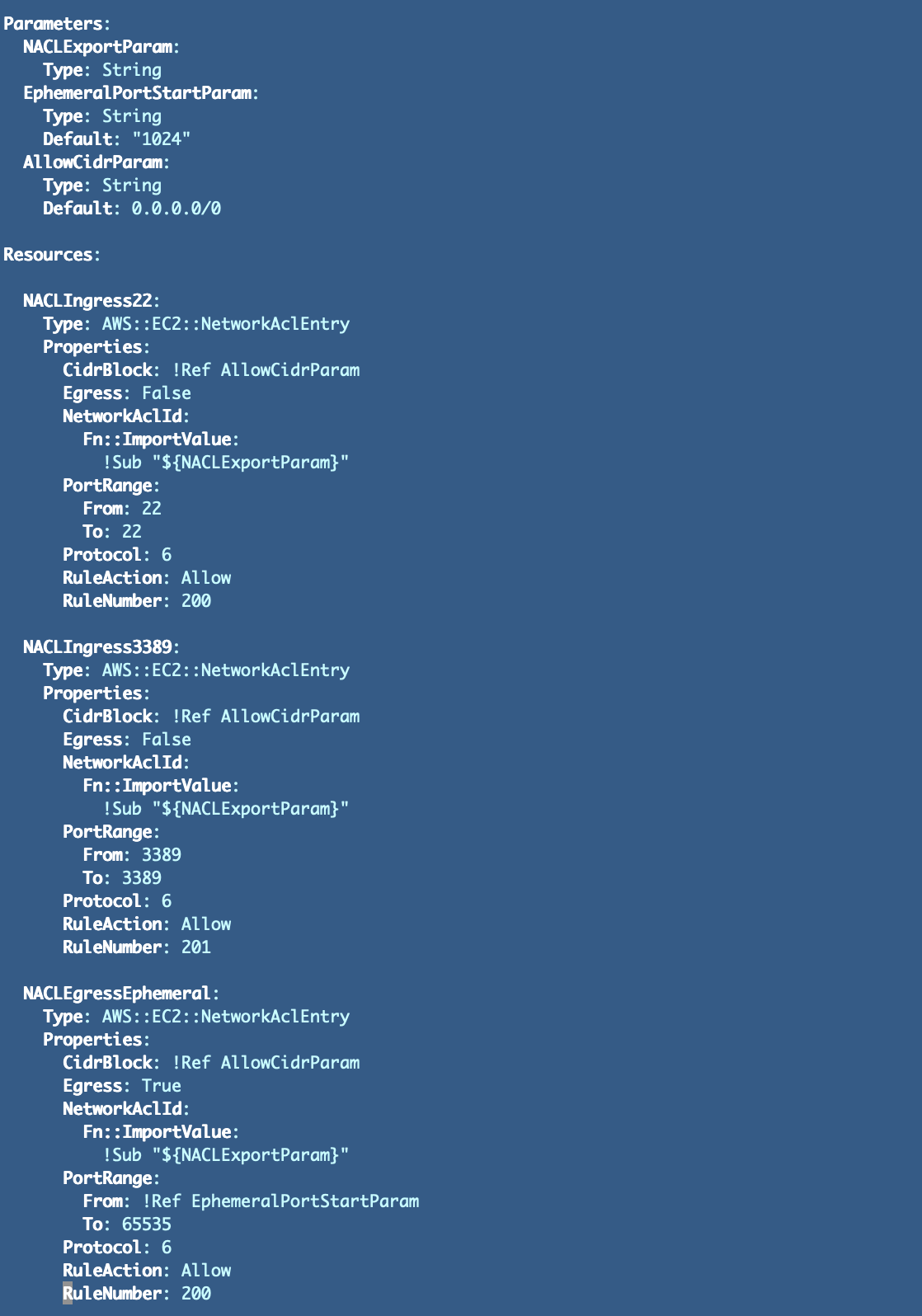
As a result of I’ve some expertise attempting to automate community guidelines on AWS I can inform you that it’s difficult. For now, I’m going create units of NALC guidelines in separate templates that may be related to a NACL. I’ll add a NACLRules folder in my CFN listing and create a separate yaml file for every ruleset.
To start out I’ll create the next recordsdata and rulesets:
- HTTPOutbound.yaml
- RemoteAccessInbound.yaml
We are able to set the next properties when making a NACL on AWS with CloudFormation.
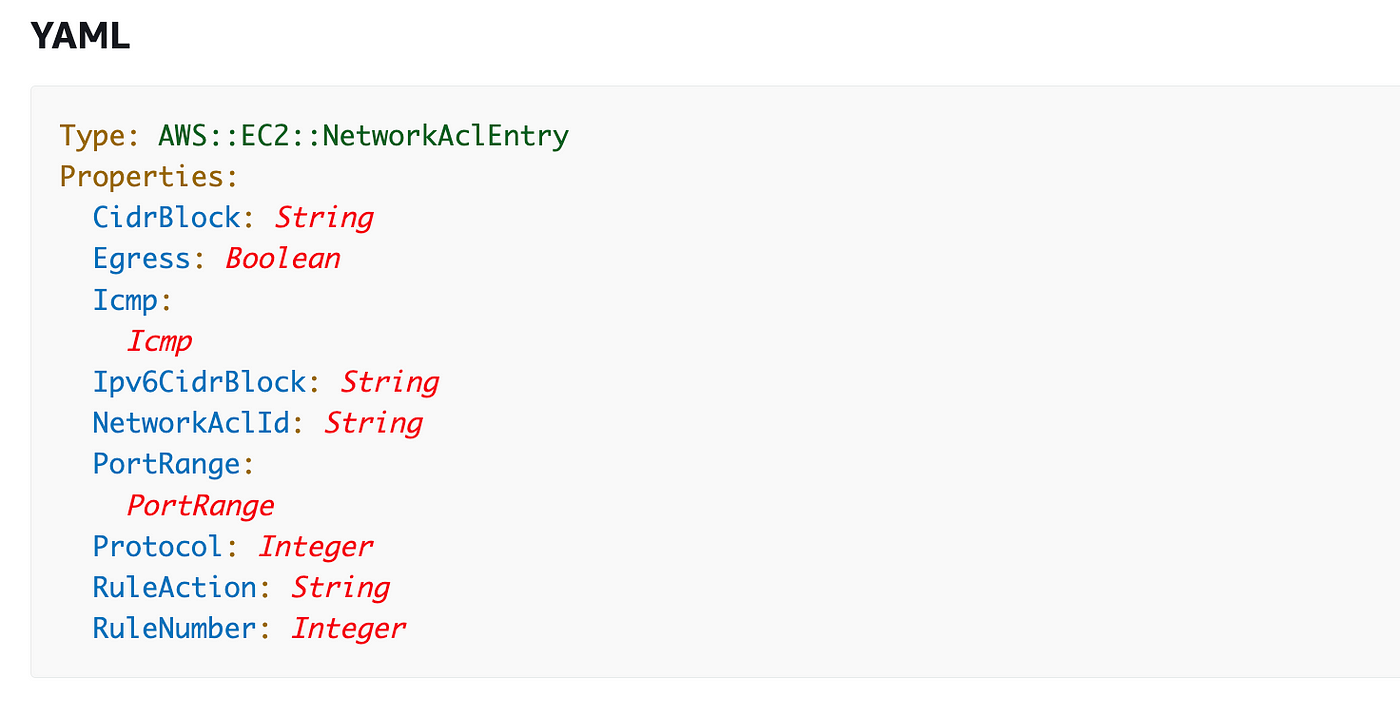
CidrBlock: We’re going to permit all for now 0.0.0.0/0
Egress: Relying whether or not we’re creating an inbound or outbound rule this might be set to true or false. (Ingress means inbound. Egress means outbound)
NetworkAclId: The NACL to which we’re including the rule. This might be handed in as a parameter so we’ve a resusable ruleset we will apply to different NACLs.
Port vary: A rule for every port above. Not like Azure you’ll be able to’t specify a listing of ports with a comma.
Protocol: We are going to solely be utilizing TCP in our guidelines (6).
RuleAction: Permit or Deny
RuleNumber: For the reason that guidelines are processed so as we need to quantity then accordingly. If, for instance, we had been being attacked by a selected IP handle, we might create a deny all rule for that IP handle and checklist that rule first with the bottom quantity. Then we might create our permit guidelines after that with increased numbers.
HTTP Outbound Template:

Distant Entry Inbound Template:
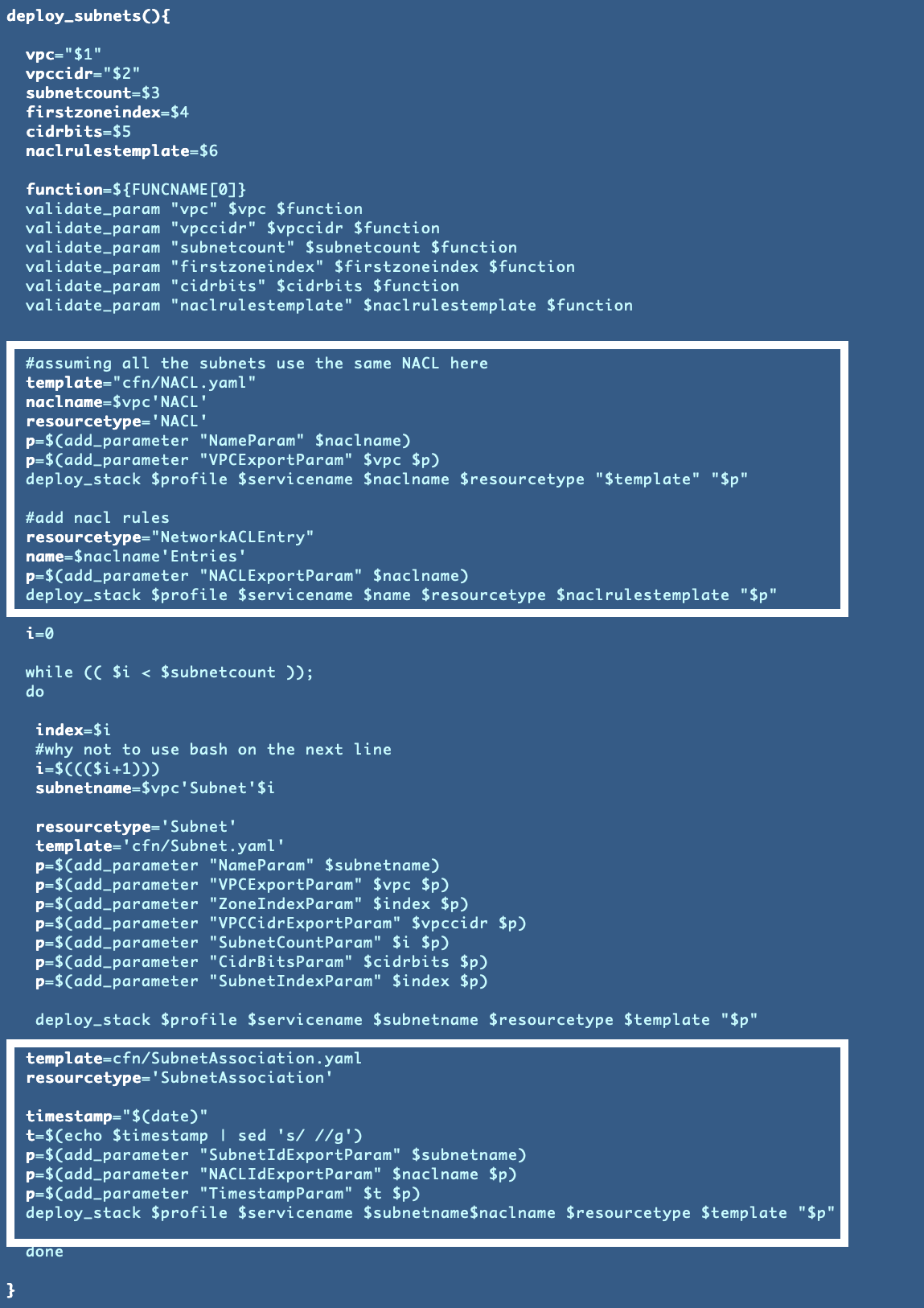
Right here’s the up to date deploy_subnets operate, which sadly will get a bit extra sophisticated when including NACL deployment:
Subsequent up. Safety Teams. Observe for updates.
Teri Radichel
In case you favored this story please clap and comply with:
Medium: Teri Radichel or Electronic mail Record: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests providers by way of LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this collection:
____________________________________________
Creator:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration take a look at or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Sources by Teri Radichel: Cybersecurity and Cloud safety courses, articles, white papers, displays, and podcasts


